From bfb56c00b085b628b61aeafccf6cb443c38a933e Mon Sep 17 00:00:00 2001
From: StrangerealIntel <54320855+StrangerealIntel@users.noreply.github.com>
Date: Sun, 10 Nov 2019 23:25:48 +0100
Subject: [PATCH] Update analysis.md
---
North Korea/APT/Lazarus/23-10-19/analysis.md | 23 ++++++++++++++++----
1 file changed, 19 insertions(+), 4 deletions(-)
diff --git a/North Korea/APT/Lazarus/23-10-19/analysis.md b/North Korea/APT/Lazarus/23-10-19/analysis.md
index 9be6766..d7c5e6c 100644
--- a/North Korea/APT/Lazarus/23-10-19/analysis.md
+++ b/North Korea/APT/Lazarus/23-10-19/analysis.md
@@ -885,7 +885,21 @@ function PulsetoC2($rid)
For conclude North Korea, try to get avanced technologies in multiples sectors aeronautics, space, energetic, but also useful energetic independence in the current situation that could lead to an international blockade.
Cyber kill chain
- The process graphs resume all the cyber kill chains used by the attacker.
+ The process graphs resume cyber kill chains used by the attacker in the differents incidents
+
+ - Powershell agents
+
+ 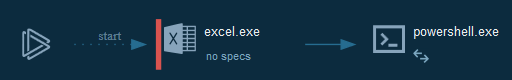 +
+
- HAL incident
+
+ 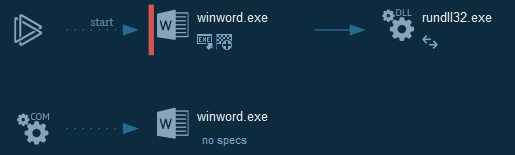 +
+
- Nuclear's plant incident
+
+ 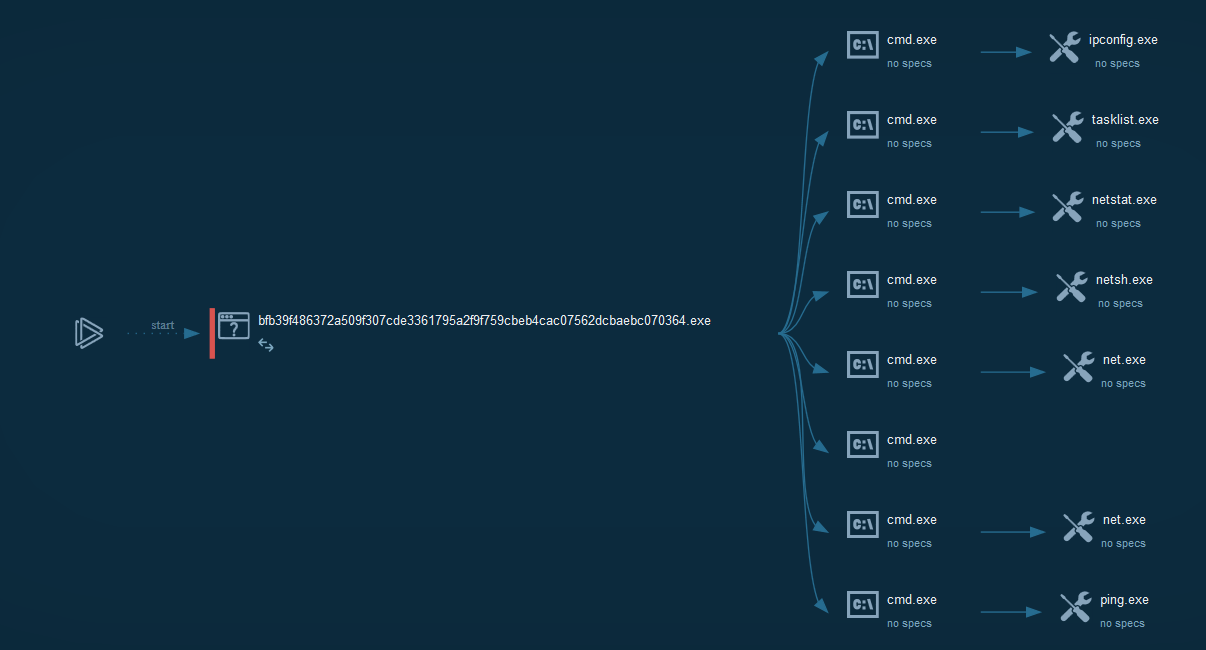 +
+
+
+
+
References MITRE ATT&CK Matrix
List of all the references with MITRE ATT&CK Matrix
@@ -972,7 +986,8 @@ function PulsetoC2($rid)
|dtrack.exe.bin|bfb39f486372a509f307cde3361795a2f9f759cbeb4cac07562dcbaebc070364|
This can be exported as JSON format Export in JSON
-
+Yara Rules
+ A list of YARA Rule is available here
Links
Originals tweets:
@@ -989,12 +1004,12 @@ function PulsetoC2($rid)
* [JD-HAL-Manager.doc](https://app.any.run/tasks/42c972b1-ec38-4637-9354-9de930ff50b2)
* [public.dll](https://app.any.run/tasks/9eb78213-df55-44c3-9465-e58eb0869e58)
* [CES2020 참관단.hwp](https://app.any.run/tasks/31be34b3-4d72-4831-8b76-6dfebe729b84)
-* [6850189bbf5191a76761ab20f7c630ef.xls](https://app.any.run/tasks/a766e70e-b07f-4a59-80fb-b18597d85b08)
+* [B578CCF307D55D3267F98349E20ECFF1.dll](https://app.any.run/tasks/a766e70e-b07f-4a59-80fb-b18597d85b08)
* [a0664ac662802905329ec6ab3b3ae843f191e6555b707f305f8f5a0599ca3f68.exe](https://app.any.run/tasks/6396ddf7-4000-4ffb-92ea-bc33612ec8c0)
External analysis:
-* [Analysis of Powershell malware of Lazarus group](https://blog.alyac.co.kr/2388 )
+* [Analysis of Powershell malware of Lazarus group](https://blog.alyac.co.kr/2388)
* [Cryptocurrency businesses still being targeted by Lazarus](https://securelist.com/cryptocurrency-businesses-still-being-targeted-by-lazarus/90019/)
Ressources :
+
+
+
+
+
+