From b48345ab69d7ac38f61cd4da5dc42409d972028c Mon Sep 17 00:00:00 2001
From: StrangerealIntel <54320855+StrangerealIntel@users.noreply.github.com>
Date: Tue, 17 Nov 2020 18:49:01 +0100
Subject: [PATCH] Update Analysis.md
---
China/APT/APT27/2020-11-17/Analysis.md | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/China/APT/APT27/2020-11-17/Analysis.md b/China/APT/APT27/2020-11-17/Analysis.md
index 3ff9cff..43e2033 100644
--- a/China/APT/APT27/2020-11-17/Analysis.md
+++ b/China/APT/APT27/2020-11-17/Analysis.md
@@ -642,7 +642,7 @@ case 0xc: // 0xc -> Remove to the DNS entry
The method for hooking the files, process and bypass iptables are similiar to XOR DDoS in the rootkit feature and implementation of the structure. That isn't excludes that can be reversed or the code source have been intercepted and modified by China APT operators.
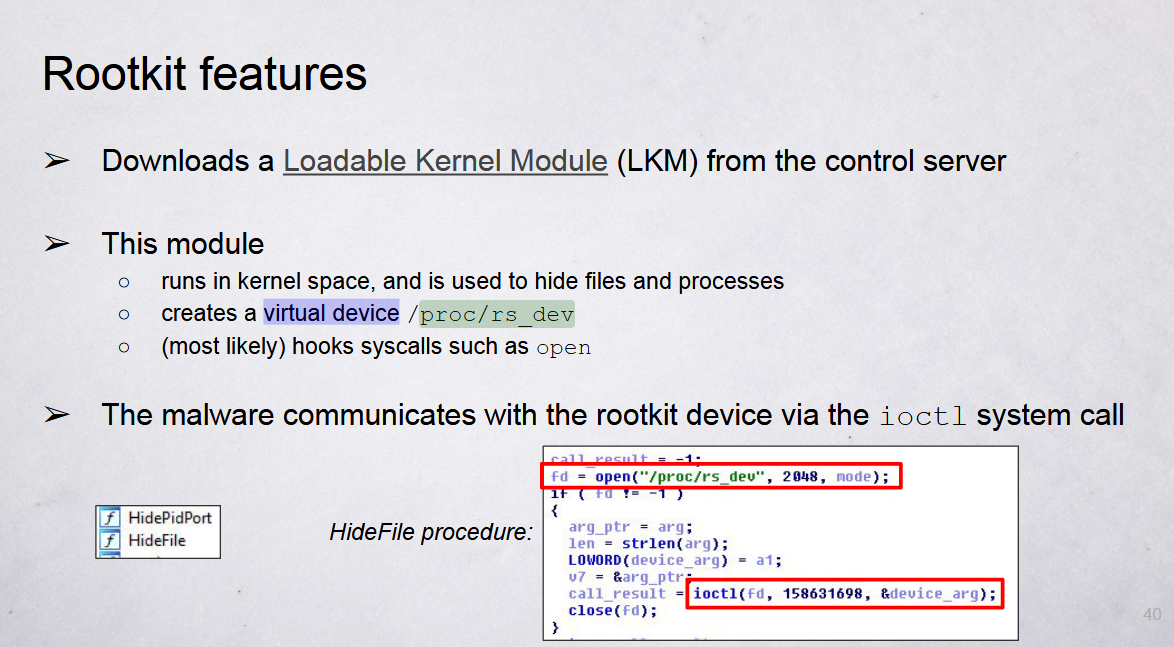
-The rest matches with some parts of the blackberry analysis about bronzeunion group but without the samples, hard to confirm it.
+The rest matches with some parts of the blackberry analysis about Bronze Union group and Winnti group but without the samples, hard to confirm it.
About XOR DDoS, another Linux botnet malware focus Docker containers and IOT and called Kaiji are used on a side operation by another Threat Actor (TA) reported by Trend Micro. I thinking to be in link to this at the beginning but finally different, this show that a leak of the source code maybe have been intercepted and reused.
