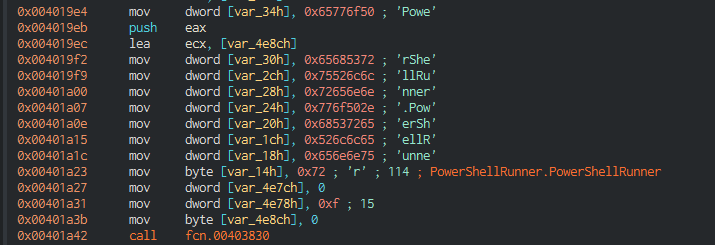
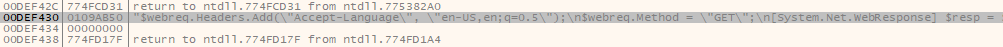
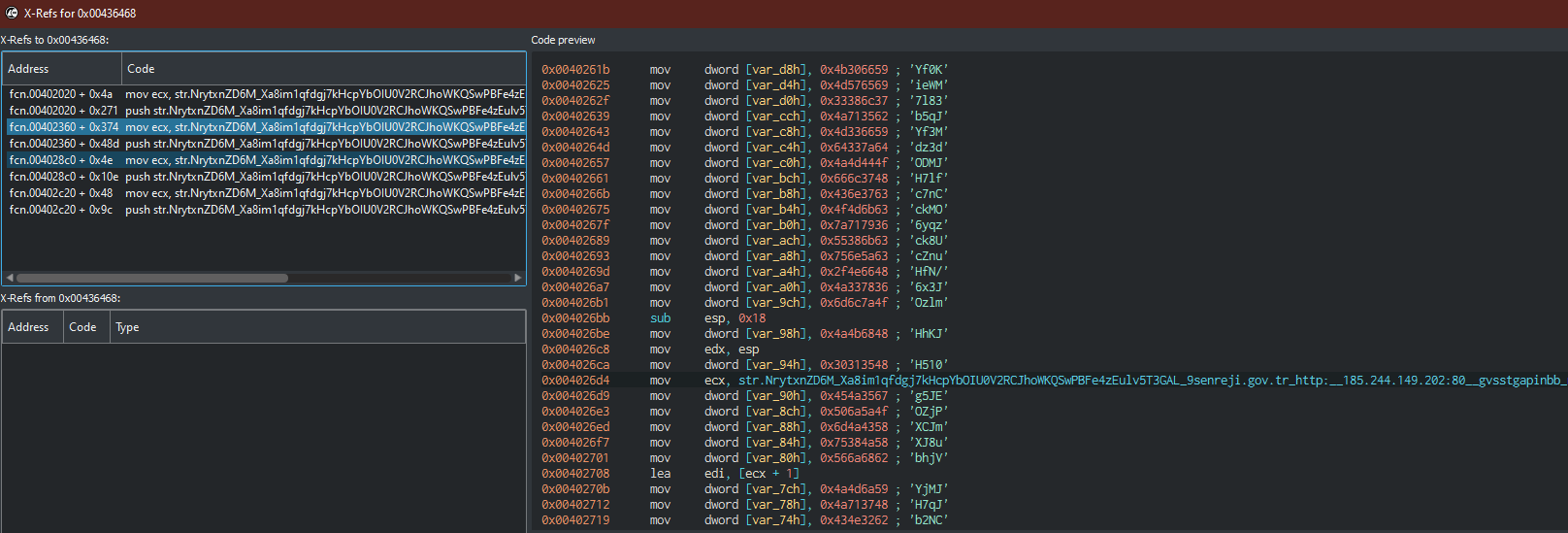
+
+| Name of lure |
+Topic |
+Victim ? |
+
+
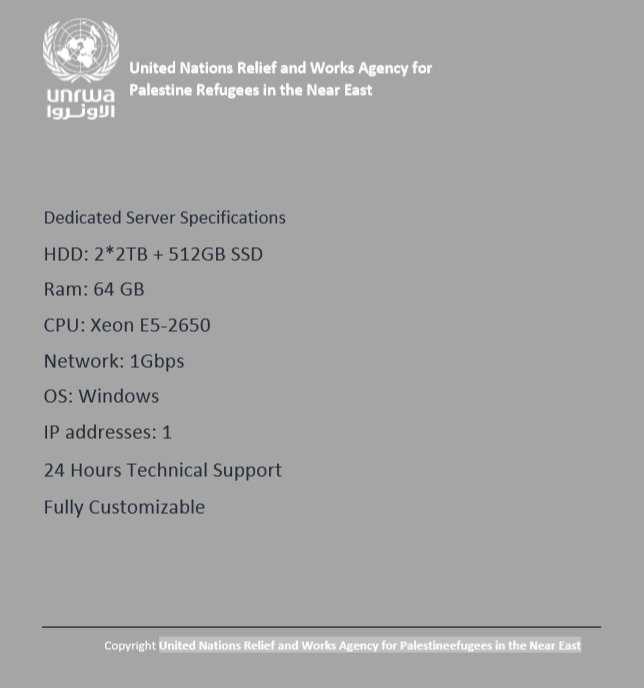
+| Jawaejifahi.pdf |
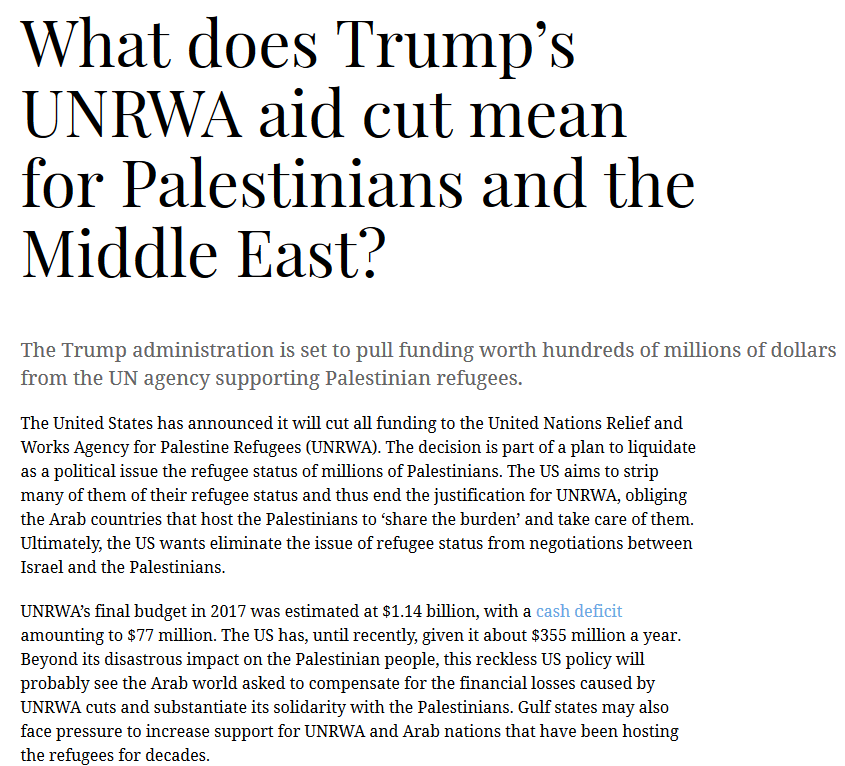
+United Nations Relief and Works Agency for Palestine Refugees in the Near East |
+UNRWA Palestine |
+
+
+| Jejytylavi.pdf |
+Second conference of Institutes of Public Administration and administrative development in the states members of the Gulf Cooperation Council (reuse an 2012 pdf ?) |
+Kingdom of Saudi Arabia |
+
+
+| Jyhynyjegu.pdf |
+MINISTRY OF FOREIGN INFORMATION PROCESSING GENERAL MANAGER ASSISTANT 07.04.2020 |
+Republic of Turkey - Ministry of Foreign Affairs |
+
+
+| Kopexaekaeru.pdf |
+Unknown |
+Unknown |
+
+| Kytuqasylu.pdf |
+Corona Virus and Cyber Defense |
+Republic of Turkey |
+
+
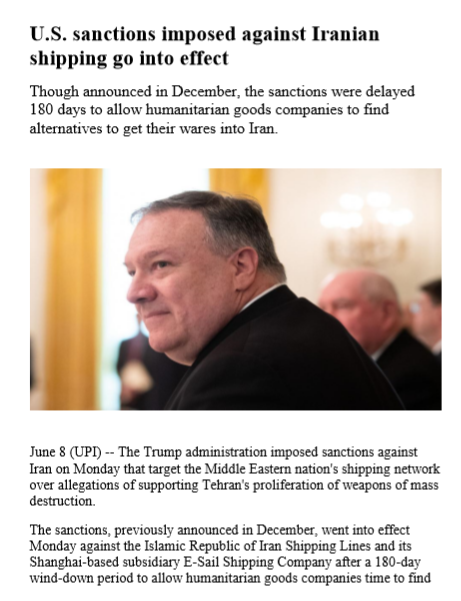
+| Lodolutaelae.pdf |
+U.S. sanctions imposed against Iranian shipping go into effect |
+USA |
+
+
+