Create Readme.md
This commit is contained in:
parent
a4e192a865
commit
3cf0ac1e03
10
offshore APT organization/Bitter/27-08-19/decrypt/Readme.md
Normal file
10
offshore APT organization/Bitter/27-08-19/decrypt/Readme.md
Normal file
@ -0,0 +1,10 @@
|
|||||||
|
## Tool for decoding the encoded strings of ArtraDownloader
|
||||||
|
##### This tool decoding the encoded strings of the three variants of ArtraDownloader used by the APT Bitter group (August 2019)
|
||||||
|
##### The following syntax is the next :
|
||||||
|
```sh
|
||||||
|
> decrypt.ps1 "[Encoded string]" [Num Variant]
|
||||||
|
```
|
||||||
|
##### This will be give you the following result :
|
||||||
|
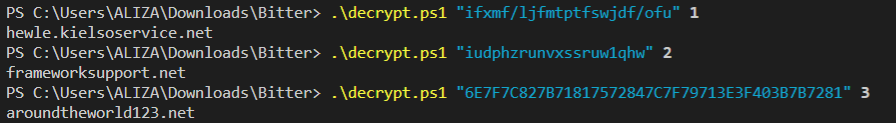
|
||||||
|
##### URL Tool : https://github.com/StrangerealIntel/CyberThreatIntel/blob/master/offshore%20APT%20organization/Bitter/27-08-19/decrypt/decrypt.ps1
|
||||||
|
##### Ref Analysis: https://unit42.paloaltonetworks.com/multiple-artradownloader-variants-used-by-bitter-to-target-pakistan/
|
||||||
Loading…
Reference in New Issue
Block a user