diff --git a/Indian/APT/SideWinder/11-10-2019/Analysis.md b/Indian/APT/SideWinder/11-10-2019/Analysis.md
index 8a74407..9e7c44c 100644
--- a/Indian/APT/SideWinder/11-10-2019/Analysis.md
+++ b/Indian/APT/SideWinder/11-10-2019/Analysis.md
@@ -1,4 +1,4 @@
-# Analysis of the new TA505 campaign
+# The SideWinder campaign continue
## Table of Contents
* [Malware analysis](#Malware-analysis)
* [Cyber Threat Intel](#Cyber-Threat-Intel)
@@ -11,7 +11,7 @@
## Malware analysis
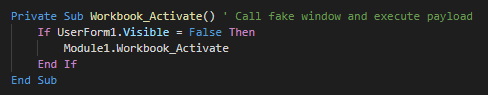
###### The initial vector is a malicious excel file which used an XLM macro (macro v4). This uses a function for launch the payload when the excel windows is active (selected as primary window). As first action, this executes the module 1.
-
+![alt text]()
## Cyber Threat Intel
######
@@ -37,6 +37,6 @@
###### Original tweet:
* [https://twitter.com/Timele9527/status/1182587382626996224](https://twitter.com/Timele9527/status/1182587382626996224)
###### Links Anyrun:
-* [Letter 7711.xls](https://app.any.run/tasks/7cdd1bfc-f0a3-4dd6-a29c-5ed70a77e76c)
+* [zhengce.doc](https://app.any.run/tasks/7cdd1bfc-f0a3-4dd6-a29c-5ed70a77e76c)
###### Ressources:
* [DotNetToJScript](https://github.com/tyranid/DotNetToJScript)