From 02a74a251e509c0c8c293cee5284314fa074d648 Mon Sep 17 00:00:00 2001
From: StrangerealIntel <54320855+StrangerealIntel@users.noreply.github.com>
Date: Sun, 17 Nov 2019 12:46:24 +0100
Subject: [PATCH] Update Analysis APT33.md
---
Iran/APT/APT33/16-11-19/Analysis APT33.md | 6 +++---
1 file changed, 3 insertions(+), 3 deletions(-)
diff --git a/Iran/APT/APT33/16-11-19/Analysis APT33.md b/Iran/APT/APT33/16-11-19/Analysis APT33.md
index cc95d1e..ed46023 100644
--- a/Iran/APT/APT33/16-11-19/Analysis APT33.md
+++ b/Iran/APT/APT33/16-11-19/Analysis APT33.md
@@ -154,15 +154,15 @@ try {main} catch {}
-  +
+ 
The fake page redirect by submit buttom to a real job proposed by the same company DynCorp International. An american global service provider. Started as an aviation company, the company also provides flight operations support, training and mentoring, international development, intelligence training and support, contingency operations, security, and operations and maintenance of land vehicles.
Threat Intelligence
The second layer of the powershell backdoor is edited from an open source framework POSHC2 (cf. ressource link). Compared to Muddywater, APT33 have gone to the open source framework probably for financial resson and better payload abilities.
According to Symantec analysis this used the same TTPs with POSHC2 payload sice the last months.
-  +
+ 
-G
+
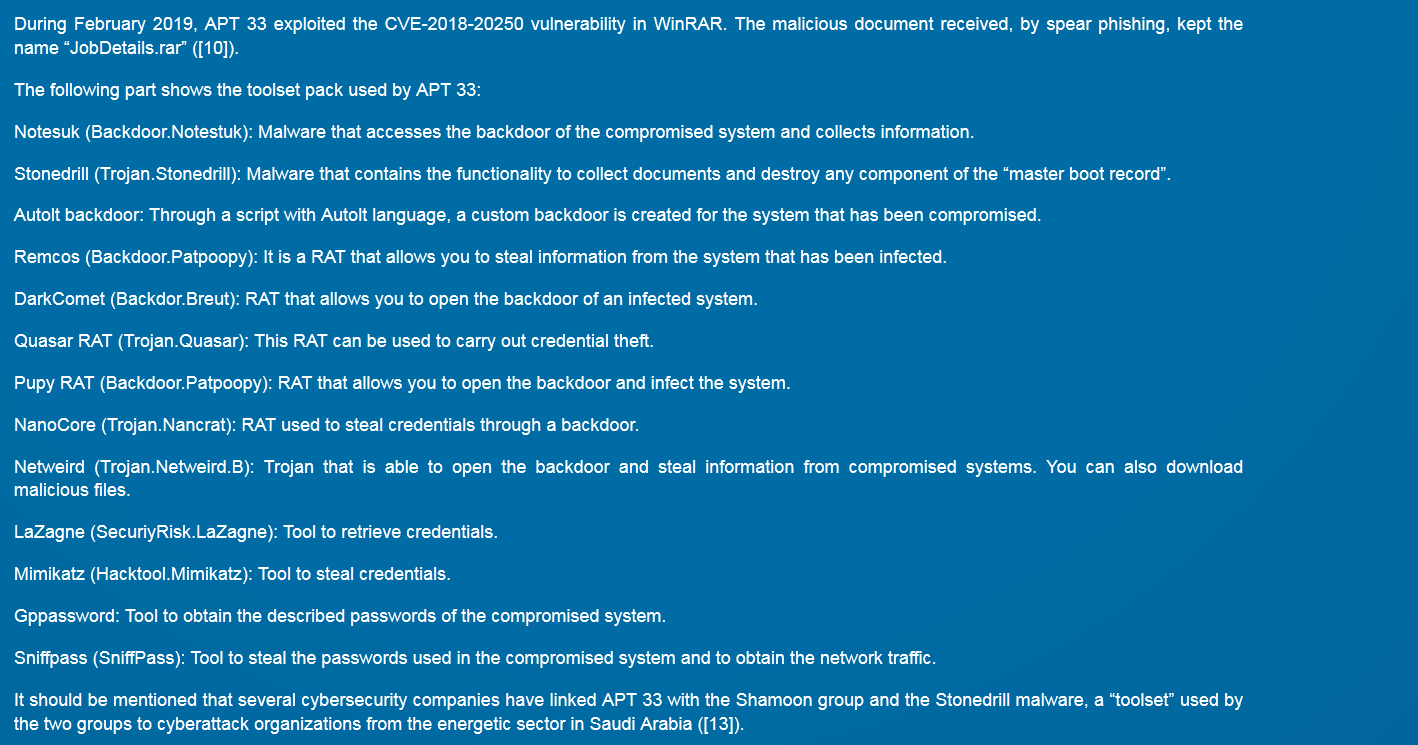
APT33 have since get an watch out for new open-source tools that can be used in their operations. By example, APT33 have been used in the new exploit on winrar archive found by Checkpoint for the campagn of February 2019.
 +
+ 

 +
+ 
+