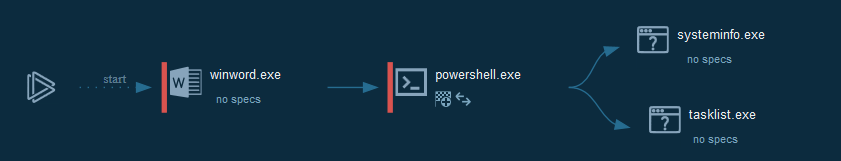
 -
-| Hash (SHA1) | -Filename | -Domain | -
| 757a71f0fbd6b3d993be2a213338d1f2 | -코로나바이러스 대응.doc | -vnext.mireene.com | -
| 5f2d3ed67a577526fcbd9a154f522cce | -비건 미국무부 부장관 서신 20200302.doc | -nhpurumy.mireene.com | -
| a4388c4d0588cd3d8a607594347663e0 | -COVID-19 and North Korea.docx | -crphone.mireene.com | -
| IP | -Route | -ASN | -Organization | -City | -Region | -Coordinates | -Country | -
| 101.79.5.222 | -101.79.5.0/24 | -AS38661 | -purplestones | -Kwangmyŏng | -Gyeonggi-do | -37.4772,126.8664 | -South Korea | -
- 